
The notorious 7777 botnet, also known as Quad7, has expanded its operations to include ASUS routers, according to a recent report by Team Cymru. This marks a significant shift in the botnet's strategy, which previously focused on TP-Link routers.
The 7777 botnet was first publicly reported by independent researcher Gi7w0rm in October 2023. Initially, it was known for its low-volume brute-force attacks on Microsoft Azure instances, targeting VIP users with only a few login attempts per week. The botnet derives its name from its unique use of TCP port 7777 on compromised devices, displaying an “xlogin:” banner when scanned.
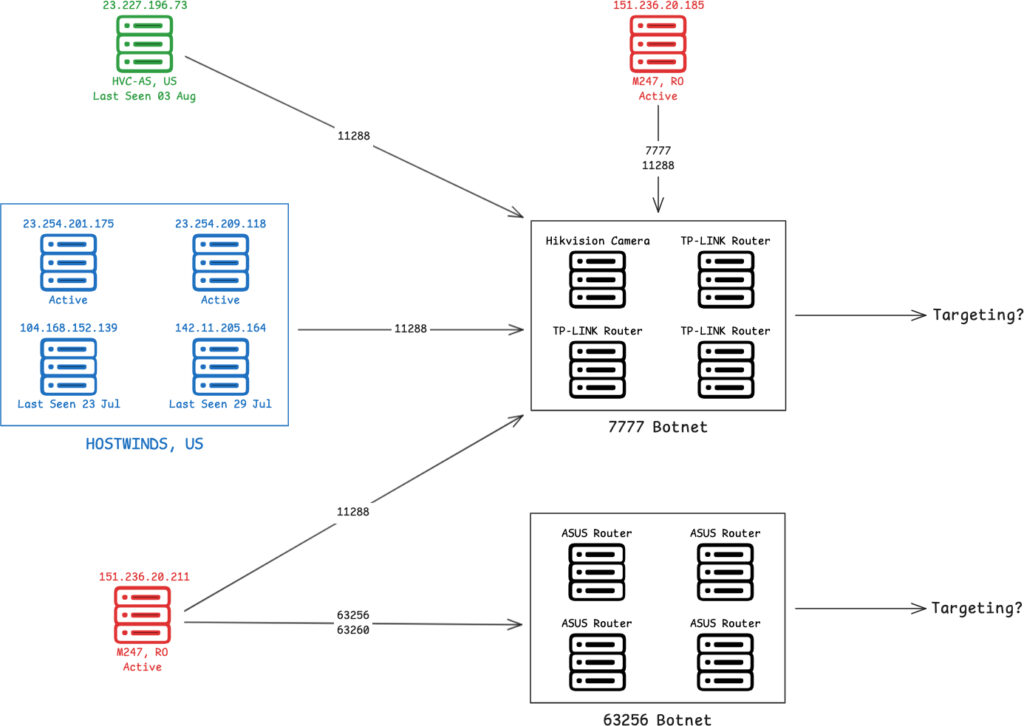
Team Cymru's latest research, aided by threat researchers Chris Fearnley and Gi7w0rm, reveals that the botnet has grown to include a secondary network of infected devices using TCP port 63256. This new tranche predominantly comprises ASUS routers, a significant deviation from the previously targeted TP-Link routers. The research identified 12,783 active bots over a 30-day period ending on August 5, 2024, indicating a substantial operational expansion.
ASUS routers under siege
The Quad7 botnet's operations are characterized by their stealth and adaptability. Team Cymru's findings show that the botnet remains active with a “healthy” number of bots despite public awareness and efforts to mitigate its impact. Their investigation involved querying IP addresses with open port 7777, identifying 7,038 devices as part of the Quad7 botnet.
Team Cymru
Recent data indicates that the botnet has expanded its arsenal with the addition of port 63256, specifically targeting ASUS routers. This shift in targeting was confirmed through detailed tagging of IP addresses and NetFlow data analysis, revealing communication patterns indicative of botnet management activities.
ASUS, a major player in the global router market, is known for its robust and feature-rich networking equipment. The company's routers are widely used in both consumer and enterprise environments. The targeting of ASUS routers by the Quad7 botnet suggests a strategic move by the botnet operators to diversify their compromised hardware, possibly to evade detection and maintain resilience against defensive measures.
Team Cymru's report highlights the identification of seven management IPs associated with the botnet's infrastructure. These IPs, spread across providers like HOSTWINDS, HVC-AS, and M247, play crucial roles in managing the compromised devices and facilitating attack activities. One IP, 151.236.20.185, continues to communicate with bots on remote port 7777, providing a remote shell for the threat operators.
Team Cymru
Defense recommendations
To defend against the Quad7 botnet and similar threats, users and administrators should implement the following measures:
- Ensure all devices have the latest firmware updates to prevent vulnerabilities from being exploited.
- Use strong, unique passwords, disable unused services, and regularly monitor network activity for suspicious behavior.
- Limit remote access to specific IP addresses or disable web admin panels entirely.
- Leverage tools like Pure Signal Recon and Scout to monitor botnet activity and query suspicious IPs.
The 7777 botnet's expansion to target ASUS routers underscores the evolving tactics of cybercriminals. Despite efforts to mitigate its impact, Quad7 remains a significant threat due to its adaptability and stealth.







Leave a Reply