Microsoft has uncovered a sophisticated cyberespionage campaign by the threat actor Marbled Dust, which exploited a previously unknown vulnerability in the popular messaging platform Output Messenger.
The group, believed to be affiliated with Turkey, has used this zero-day exploit (CVE-2025-27920) since April 2024 to gather intelligence on Kurdish military targets in Iraq.
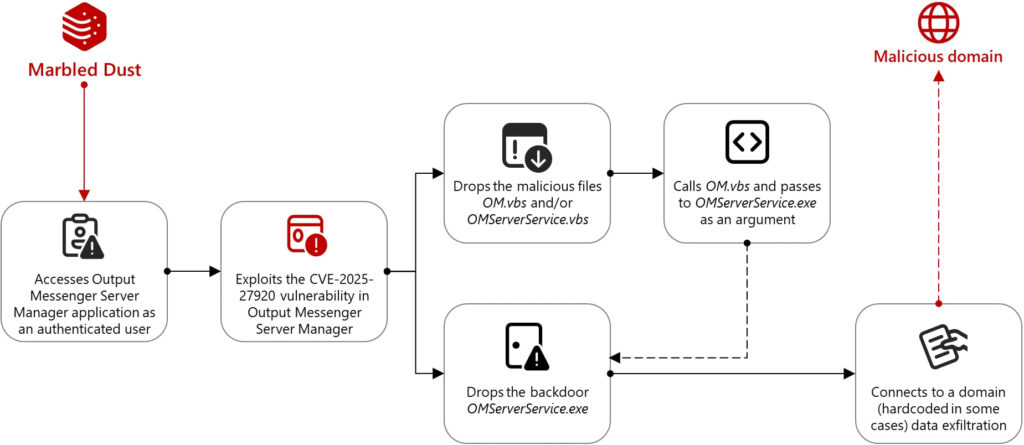
According to Microsoft Threat Intelligence, Marbled Dust targeted Output Messenger — a multiplatform internal chat and collaboration tool developed by Srimax — by leveraging a directory traversal flaw in its Server Manager component. The flaw enabled authenticated users to upload malicious scripts to the server's startup directory, effectively compromising the entire server environment. Victims observed so far are reportedly connected to the Kurdish military, a focus consistent with Marbled Dust's history of targeting entities seen as counter to Turkish strategic interests.
Marbled Dust is known for targeting government and telecom entities in Europe and the Middle East and overlaps with threat actor designations Sea Turtle and UNC1326 in other vendor reports. Previously, the group has used DNS hijacking, credential harvesting, and manipulation of domain registries to compromise targets. This latest campaign, however, reflects a leap in technical maturity, evidenced by its use of a zero-day vulnerability and deployment of cross-platform GoLang malware.
The exploited vulnerability (CVE-2025-27920) affects Output Messenger Server Manager, where the server's “output drive” feature lets users upload files. An attacker, once authenticated, can manipulate the file path to place a malicious VBS script named OMServerService.vbs in the server's startup folder. This script launches another file, OM.vbs, which in turn invokes OMServerService.exe, a GoLang-based backdoor communicating with the Marbled Dust command-and-control domain api.wordinfos[.]com.
Output Messenger is a widely used internal communication solution for on-premises deployments, favored by businesses and governmental institutions in regions where cloud services are limited or tightly regulated. Its architecture involves a client-server model with centralized file sharing and user authentication — an arrangement that makes a compromised server a high-value intelligence node. Once inside, attackers could read messages, impersonate users, and exfiltrate sensitive files.
Microsoft noted that on the client side, a secondary GoLang backdoor named OMClientService.exe is installed alongside the legitimate Output Messenger client binary. This component initiates contact with the threat actor's infrastructure to deliver victim identification data and receive commands, potentially executing arbitrary code via Windows command prompt. In one observed instance, data was exfiltrated by creating a compressed archive on the desktop and transmitting it through a tunnel established using Plink, the command-line interface of PuTTY.
Microsoft
Following its discovery, Microsoft privately disclosed the vulnerability to Srimax, who promptly issued patches for both CVE-2025-27920 and a second, currently unexploited flaw (CVE-2025-27921). Fixed versions are: Windows Client – Version 2.0.63, and Server – Version 2.0.62.
To defend against similar threats, Microsoft recommends organizations to update Output Messenger to patched versions immediately, enable cloud-delivered protection in endpoint antivirus solutions, and require phishing-resistant MFA for critical apps via Entra ID Conditional Access.
This campaign highlights a concerning evolution in Marbled Dust's toolkit and strategy, signaling a move toward zero-day exploitation to achieve strategic surveillance objectives. Organizations operating in geopolitically sensitive regions or using Output Messenger on-premises should prioritize patching and review authentication and DNS security configurations.







Leave a Reply