
Researchers at Infoblox and Eclypsium have identified a critical vulnerability in the domain name system (DNS), dubbed the “Sitting Ducks” attack, which is being exploited by over a dozen Russian-linked cybercriminal groups to hijack domain names unnoticed.
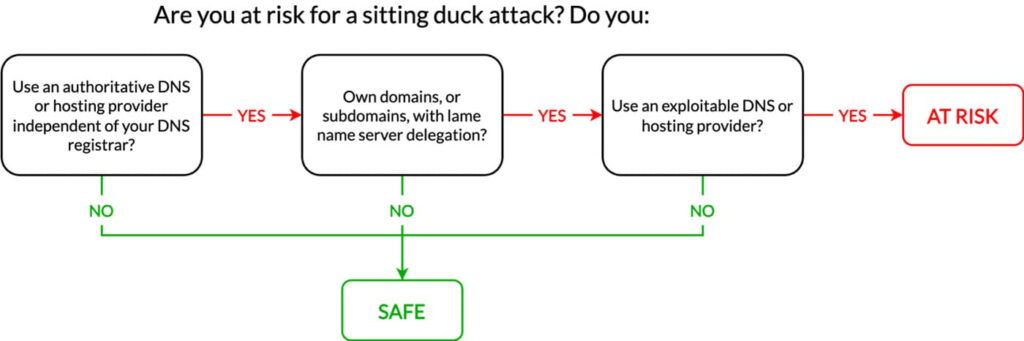
The Sitting Ducks attack allows cybercriminals to hijack registered domains without accessing the legitimate owner's account at the DNS provider or registrar. This attack vector, first detailed by Matt Bryant in 2016, exploits misconfigurations at domain registrars and DNS providers, making it easy to perform, difficult to detect, and almost entirely preventable.
Infoblox and Eclypsium's discovery came while investigating the infrastructure behind the 404TDS, a traffic distribution system (TDS) hosted in Russia and first identified by Proofpoint.
Sitting Ducks method and impact
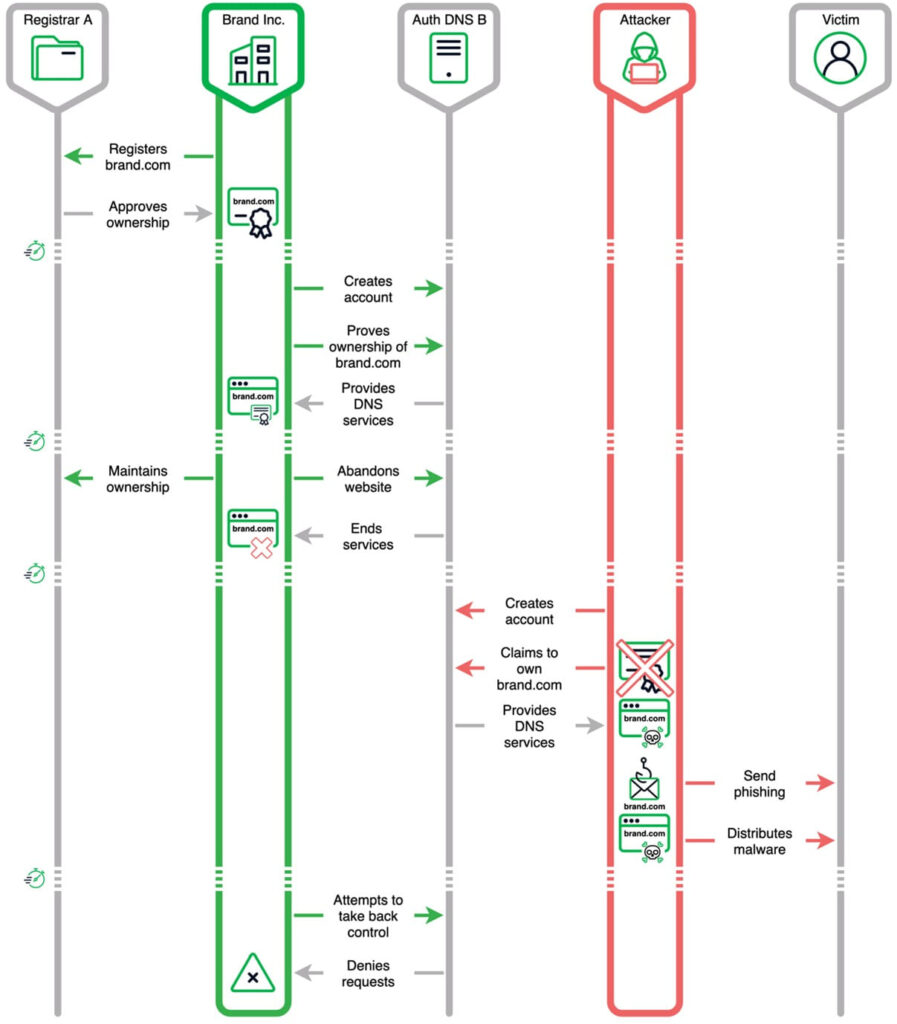
In a Sitting Ducks attack, the actor takes control of a domain by exploiting a “lame delegation” — a situation where the authoritative name server does not have information about the domain. This enables the attacker to claim the domain at the DNS provider, allowing them to conduct various malicious activities such as malware delivery, phishing campaigns, brand impersonation, and data exfiltration.
Researchers estimate over a million domains are vulnerable to this attack daily, with hundreds being hijacked each day, particularly by Russian cybercriminals.
The vulnerability affects domains across hundreds of top-level domains (TLDs), including those owned by large brands, small businesses, individuals, and even regional governments. Many hijacked domains are registered with brand protection registrars, making malicious use harder to detect.
For instance, the domain blizzaktires[.]com was hijacked by different actors over time, each using it for various malicious purposes:
- June 11 – July 11, 2022: Suspicious porn TDS transmitted through spam.
- April 4 – May 2, 2023: Unknown actor and use.
- June 11 – June 27, 2024: Vacant Viper 404TDS.
Since 2018, Sitting Ducks has been used to hijack over 35,000 domains, with the number likely much higher. The earliest known actor, Spammy Bear, began hijacking domains in late 2018 at GoDaddy. Multiple actors exploit DNS providers as a “domain lending library,” using free accounts to borrow domains for short periods, creating additional obfuscation.
Infoblox
Preventive measures
Prevention of Sitting Ducks attacks requires collaboration among all stakeholders in DNS management:
- Domain name holders need to evaluate risk and ensure active service relationships with DNS providers.
- Registrars need to prevent lame delegations in a timely manner and educate users on the risks.
- DNS providers should implement best practices such as random name server assignments and report lame requests for fixing.
- Government and regulatory bodies must enforce regulations requiring robust DNS provider practices.
The Sitting Ducks attack highlights the critical need for improved DNS management practices to prevent domain hijacking, which is currently deceptively easy, at least under certain conditions. Without concerted efforts from all parties involved, this attack vector will continue to pose a significant threat to internet security.







Leave a Reply