
A coalition of Western intelligence agencies has released a detailed technical advisory revealing the inner workings of two sophisticated spyware tools — MOONSHINE and BADBAZAAR — used to surveil and collect data from minority communities and civil society groups viewed as politically sensitive by the Chinese state.
The 30-page advisory is the result of a joint investigation led by the UK's National Cyber Security Centre (NCSC) in collaboration with intelligence and cybersecurity counterparts from the United States, Canada, Germany, Australia, and New Zealand. The document sheds light on years-long spyware operations targeting Uyghurs, Tibetans, Taiwanese nationals, and advocates of democratic movements, including those supporting the Falun Gong.
Spyware discovery and attack methods
The advisory is based on intelligence from government agencies and industry sources, including Trend Micro, Citizen Lab, Lookout, and Volexity. It provides case studies that demonstrate how the two spyware strains operate by exploiting mobile devices through trojanized apps — seemingly benign software embedded with surveillance capabilities.
MOONSHINE, initially reported by Citizen Lab in 2019, re-emerged in recent campaigns targeting Uyghur Muslims through apps like “قۇرئان ئاۋازلىق” (“Audio Quran.apk”). Once installed, this Android spyware grants attackers access to live audio, photos, GPS data, and personal files. Its distribution network includes Telegram groups and WhatsApp messages that are frequently used by targeted communities.
The UK NCSC and its partners noted links between MOONSHINE's control panels and infrastructure associated with “UPSEC,” a name possibly linked to Sichuan Dianke Network Security Technology Co., Ltd., although this claim remains unverified by official agencies.
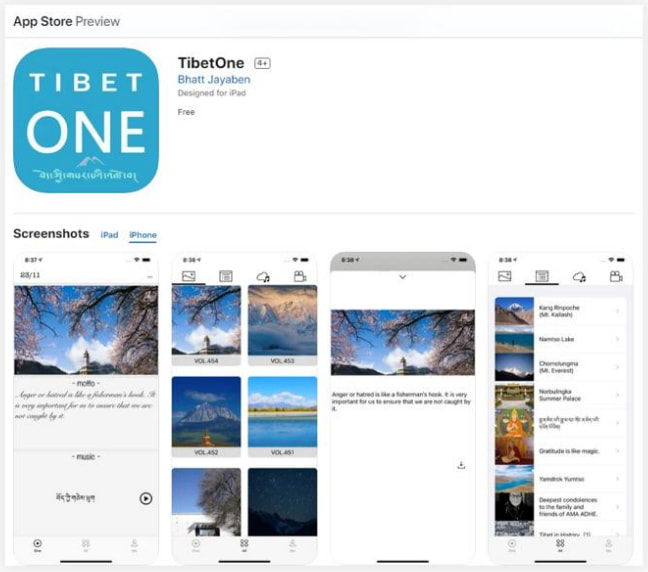
BADBAZAAR, a dual-platform spyware with variants for both iOS and Android, has been used to target Tibetans via the now-removed ‘TibetOne' app from the Apple App Store. This app was also promoted in Telegram groups and Reddit forums. Investigators observed that attackers impersonated known Tibetan activists, using fabricated identities and comments on websites like “tibetone[.]org” to bolster credibility.
FBI
BADBAZAAR and MOONSHINE share similar capabilities, including:
- Access to microphone and camera
- GPS tracking
- Collection of call logs, SMS messages, and device metadata
- Real-time surveillance mechanisms
These functionalities serve surveillance objectives likely aligned with Chinese state interests in monitoring dissent and silencing criticism, both domestically and abroad.
Global targeting
According to the advisory, the spyware campaigns are not restricted to activists within China. Individuals and organizations globally who are perceived to support independence or autonomy for Taiwan, Tibet, and Xinjiang or who promote democratic values are also considered potential targets. The campaigns show a clear pattern of exploiting the trust within online communities to spread malicious applications.
Victims include journalists, human rights organizations, religious groups, and members of the diaspora. The spyware is often disguised in culturally or linguistically relevant apps, such as navigation tools and religious texts, and distributed via third-party sites or, in some cases, through official app stores, bypassing security vetting mechanisms.
To mitigate the risk of falling victim to these campaigns, it is recommended to only download apps from trusted sources such as Google Play or Apple's App Store, avoid “jailbreaking” or “rooting” mobile devices, and apply available security updates for your device as soon as possible.







China has threatened to invade Taiwan if they do not agree to be ruled by the Chinese Communist Party, when that happens they will try to intimidate us into not supporting democracy and free speech in Taiwan, the time to get ready to prepare against a Chinese backed offensive is now, we should not be waiting until they invade Taiwan for us to get ready.