
A US carmaker’s dealership management platform contained a pair of critical vulnerabilities that could have allowed remote car unlocking, customer data theft, and access to over 1,000 dealers’ internal systems, all from a web browser.
The flaws, revealed by security researcher Eaton Zveare at DEF CON 33, required no insider credentials and were exploitable from anywhere on the internet.
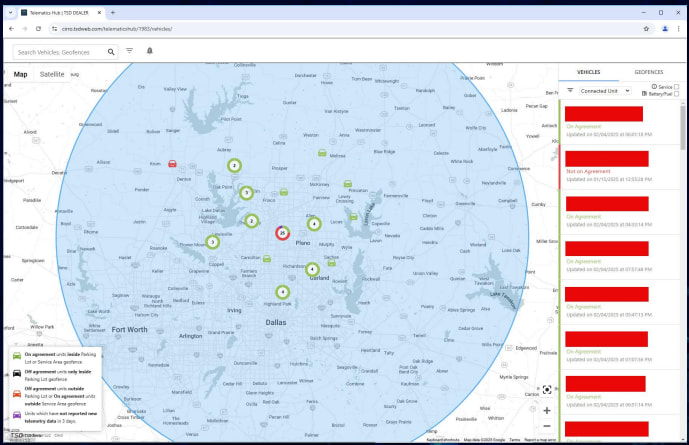
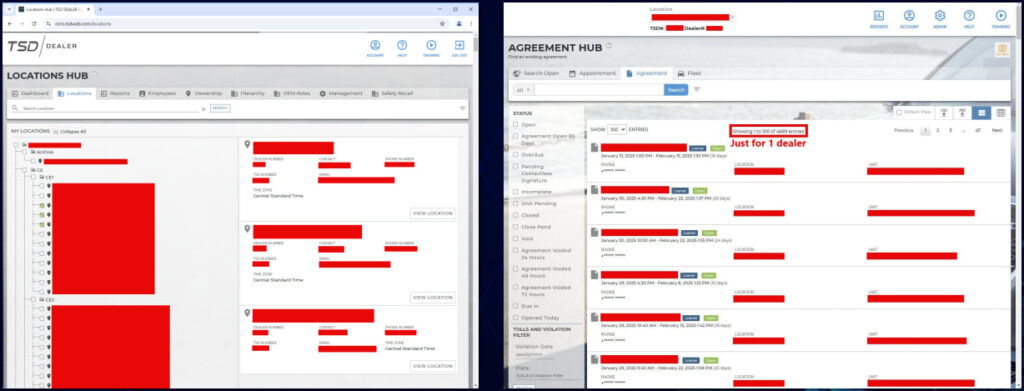
The affected platform, used daily by the automaker’s authorized dealerships, handled tasks like vehicle ordering, lead management, financing, and telematics tracking. It was invite-only, enforced two-factor authentication, and ran on an SAP/Java backend with an AngularJS frontend. Despite those safeguards, Zveare discovered that the system’s registration API failed to verify invite tokens, a lapse that let him register a dealer account without authorization. A second oversight allowed him to establish a valid session via a “profile update” feature, exposing hundreds of JavaScript files and undocumented admin APIs.
Eaton Zveare
By locally modifying the portal’s scripts, Zveare bypassed client-side security checks, unlocked the hidden user management interface, and created a “national admin” account. This top-tier account could impersonate any dealership employee, manage single sign-on (SSO) settings across interconnected systems, and access sensitive sub-brand portals. Within minutes, Zveare could pull up customer records by VIN or name, reassign vehicle ownership to new accounts, and control remote features like unlocking doors and starting engines, tested with a consenting friend’s car.
Eaton Zveare
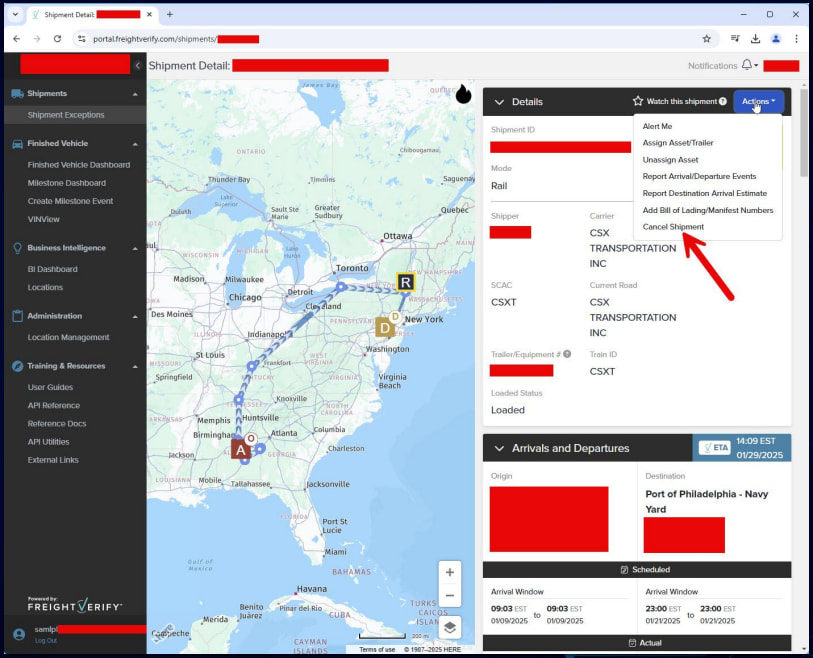
Beyond direct vehicle control, the compromise opened the door to a trove of personal and operational data. The portal linked to systems containing dealer employee SSNs, finance contracts, loaner fleet GPS tracking, and shipment management tools capable of canceling vehicle deliveries. Performance analytics dashboards, customer satisfaction surveys, and even built-in marketing tools were also in scope. Some features mirrored flaws Zveare previously saw in Toyota’s dealer portal, including insecure user impersonation.
Eaton Zveare
Zveare reported the bugs to the unnamed carmaker on February 3, 2025, and they were patched within a week. He emphasized that just two basic API authentication errors had “blasted the doors open” and that overly interconnected dealer systems amplify the fallout of a single breach.
Drivers can’t directly harden dealer portals, but they can reduce risk by limiting personal data shared with dealerships, monitoring for unusual account or vehicle activity, and avoiding unnecessary mobile app enrollments.






Leave a Reply