
Vidar infostealer has released version 2.0, now featuring a complete rewrite in C, multithreading support, and advanced credential theft techniques that allow it to bypass Chrome's latest memory protection features.
The release closely follows the decline of Lumma Stealer, positioning Vidar as the new frontrunner in the malware-as-a-service (MaaS) ecosystem.
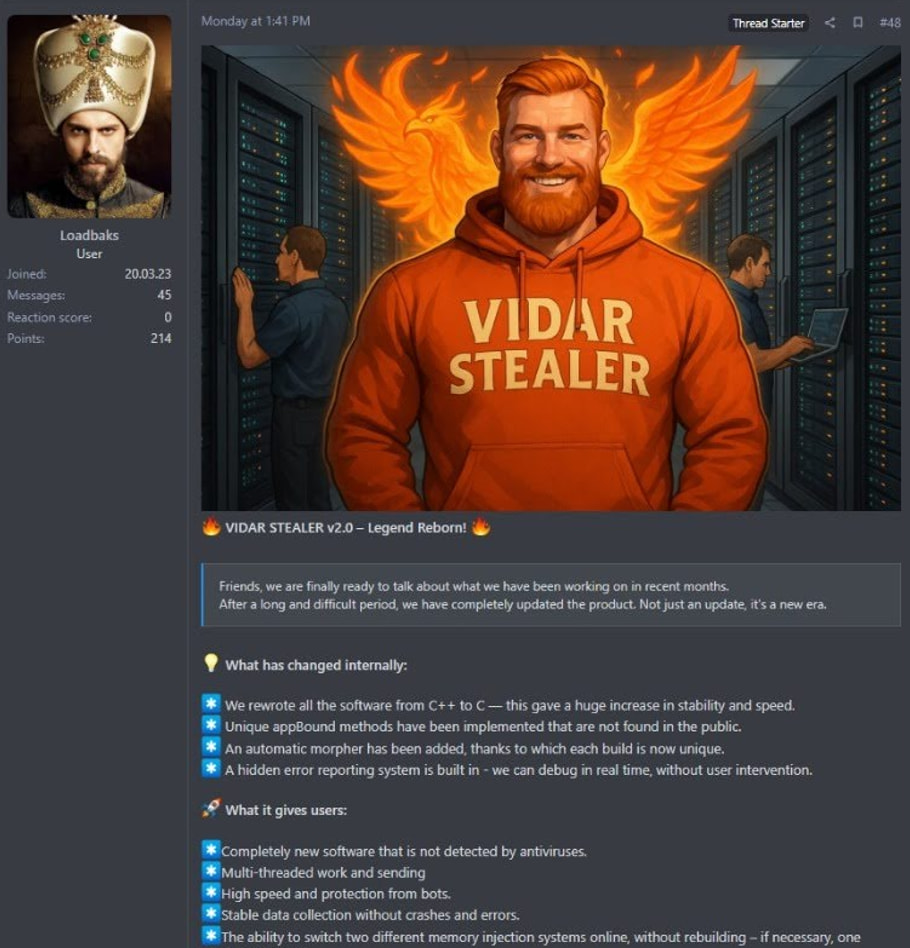
Trend Micro reports that Vidar 2.0 was released on October 6, 2025, by a developer operating under the alias “Loadbaks” on underground forums. Loadbaks touted the rewrite from C++ to C as a performance and stability boost, alongside the integration of a polymorphic builder and an intelligent multithreading system for accelerated data theft.
Vidar has been active since 2018, initially forked from the Arkei stealer, and gained popularity for its broad data harvesting capabilities and low price point, reportedly a one-time $300 fee. It competed with other popular stealers such as Raccoon and RedLine, though its consistent updates and wider compatibility with browsers and wallet apps have allowed it to maintain a strong foothold in cybercriminal markets. With Lumma Stealer's presence fading, adoption of Vidar has surged, as evidenced by telemetry showing a sharp increase in activity through early October.
Vidar 2.0 systematically targets a wide array of platforms and applications:
- Browsers: Chrome, Edge, Firefox, Opera, Vivaldi, Waterfox, Palemoon
- Wallets: Monero, browser-based extensions (via IndexedDB, LevelDB)
- Cloud services: AWS (.aws), Azure (.azure, msal.cache), Office 365 tokens
- Gaming and communication platforms: Steam (ssfn, loginusers.vdf), Discord, Telegram
In addition to credentials, the malware captures system information, screenshots, and specific application session files. Exfiltration occurs via HTTP multipart forms to a rotating set of command-and-control (C2) channels, including Telegram bots and Steam profiles—further complicating takedown efforts.
Trend Micro
C rebuild and multi-threading
Vidar 2.0's transition to the C programming language represents more than a cosmetic update. The rewrite discards legacy C++ dependencies and runtime structures in favor of low-level control and efficiency, granting attackers a more stable and performant tool. This foundation enables a new multithreaded architecture that dynamically adjusts to the victim's system specs, allowing the malware to run multiple data collection routines in parallel. On higher-end systems, Vidar spawns more threads to harvest information rapidly, minimizing dwell time and reducing the chances of detection.
The use of multithreading permits simultaneous theft from multiple sources, such as browsers, cryptocurrency wallets, cloud config files, FTP clients, and more, without interrupting the system's functionality or alerting users. This design not only enhances speed but also gives Vidar an advantage in evading behavioral detection engines that monitor long-running or sequential data access patterns.
Bypassing AppBound encryption
A standout upgrade in Vidar 2.0 is its ability to bypass Chrome's AppBound encryption, a security feature introduced to tie decryption keys to the browser process itself. Traditionally, stealers had to extract browser encryption keys from disk, which AppBound was designed to disrupt. However, Vidar circumvents this by injecting shellcode or reflective DLLs directly into a running browser session, siphoning decryption keys from active memory and relaying them back to the main malware process via named pipes, avoiding disk artifacts altogether.
This approach allows Vidar to extract stored passwords, autofill data, cookies, and browsing history from Chrome, Firefox, Edge, and several other Chromium-based browsers. It targets encrypted database files such as Login Data, Web Data, logins.json, and master key files like key4.db for Firefox, combining traditional decryption techniques with memory-based attacks to maximize credential exposure.
Polymorphism and anti-analysis
To further hinder detection, Vidar 2.0 introduces a built-in polymorphic builder that produces uniquely obfuscated binaries for each customer or campaign. These builds employ control flow flattening and numeric state machines, creating highly irregular and complex execution paths that resist static analysis and signature-based detection.
Anti-analysis routines are deeply embedded in the malware's initialization process, including checks for virtual machines, debugging environments, unusual system uptimes, and hardware anomalies. These checks must pass for the malware to continue execution; otherwise, it self-terminates, limiting opportunities for researchers to examine its behavior in sandboxed environments.
The malware is designed to clean up after itself, deleting temporary files and gracefully shutting down its thread pool to avoid leaving artifacts behind.
To minimize the risk of Vidar 2.0 infections, avoid downloading executables from dubious sites, only download software from official sources, and always scan files with an up-to-date antivirus.







Leave a Reply