
Amnesty International has uncovered fresh evidence of NSO Group’s Pegasus spyware being used to target two investigative journalists at Serbia-based BIRN via Viber, deepening concerns about the country’s systemic misuse of digital surveillance tools.
The findings, published in a technical briefing by Amnesty International’s Security Lab, confirm that two reporters from the Balkan Investigative Reporting Network (BIRN) were targeted on February 14, 2025, with Pegasus spyware links delivered through the Viber messaging platform. This is the third Pegasus-related incident involving Serbian civil society in under two years and follows recent revelations of Cellebrite forensic tools being used against a student activist — further evidence of an escalating surveillance apparatus targeting dissent in Serbia.
Getting spyware on Viber
The two targeted journalists, identified as “Bogdana” and Jelena Veljković, received similar Pegasus-laced messages on the same day via a Serbian phone number registered with the state-owned operator Telekom Srbija. Amnesty’s forensic analysis confirmed the messages were part of a coordinated 1-click Pegasus infection attempt, with links pointing to decoy pages mimicking Serbian media websites such as n1info.com — a known tactic linked to earlier Pegasus attacks in the country.
The attack against “Bogdana” was delivered to her iPhone via Viber at 13:46 local time. The message contained an ambiguous question referencing a possible source and embedded a short, redacted URL. Amnesty identified the domain as associated with NSO Group’s Pegasus infrastructure. Although the journalist did not open the link, the message closely mirrored prior Pegasus infection chains, including the use of familiar decoy websites. Forensics confirmed this was a deliberate 1-click attack aimed at covertly installing spyware.
Jelena Veljković, a veteran investigative reporter covering corruption and public finance, received an almost identical Viber message just an hour earlier. While the original link was deleted before it could be analyzed in full, its format and origin mirrored the one sent to her colleague, leading investigators to conclude with high confidence that it was part of the same Pegasus campaign.
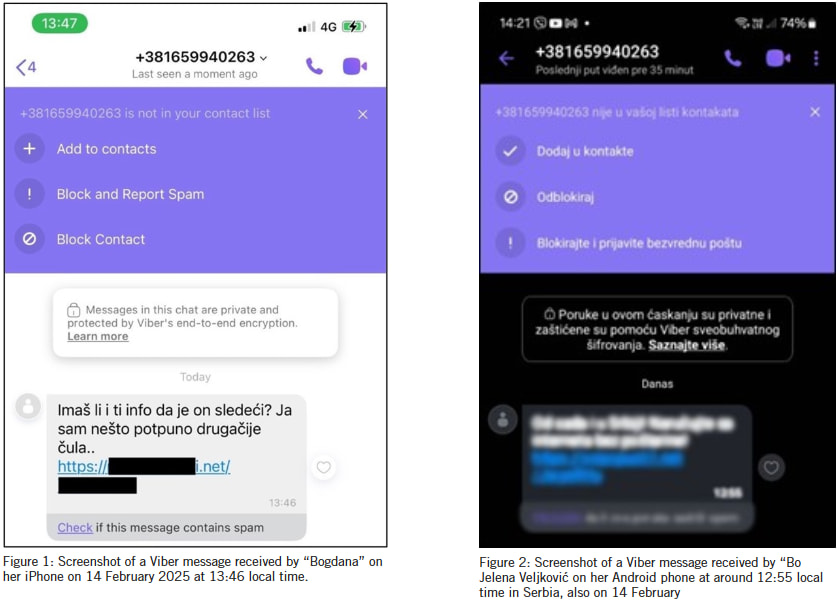
The use of Viber as an infection vector marks a disturbing evolution in spyware delivery methods. The platform’s popularity in Serbia makes it an attractive medium for social engineering, and attackers appear to have exploited its contact suggestion feature to bypass user suspicion.
BIRN, the target organization, is an award-winning regional network of investigative journalists with a track record of uncovering high-level corruption and organized crime. Its staff has been routinely harassed and threatened, and currently faces multiple Strategic Lawsuits Against Public Participation (SLAPPs), including ones filed by senior officials such as the mayor of Belgrade. The outlet’s prominent role in exposing government-linked abuses makes it a target for state surveillance.
When confronted with the latest Pegasus findings, the NSO Group reiterated its policy of not commenting on specific customers and emphasized its adherence to human rights standards under the UN Guiding Principles. However, Amnesty International has criticized the firm’s failure to suspend suspected abusive clients, particularly after prior warnings and documented misuse in Serbia.
Amnesty also notes that Pegasus is officially licensed only to government agencies, suggesting the Serbian state or affiliated actors are directly responsible for these attacks.
In response to the report, Viber acknowledged receipt of Amnesty’s findings and stated it would review the matter internally. However, no specific mitigation or public security advisory has yet been issued.







Leave a Reply