
A critical vulnerability in the Verizon Call Filter app for iOS exposed incoming call records of potentially all Verizon Wireless customers, allowing unauthorized access to sensitive metadata without authentication or device compromise.
The flaw was discovered by independent security researcher Evan Connelly on February 22, 2025, and responsibly disclosed to Verizon the same day. The researcher observed that a backend API used by the Call Filter app failed to verify that the phone number requested for call history matched the authenticated user’s number. As a result, any attacker with a valid JWT token — readily available to logged-in users — could manipulate the request header to retrieve call logs for any Verizon customer.
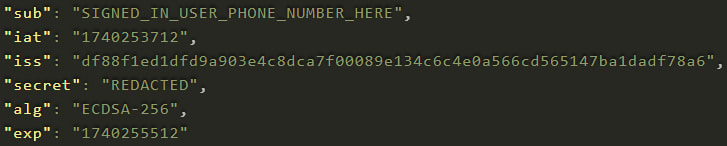
The vulnerable endpoint, ‘https://clr-aqx.cequintvzwecid.com/clr/callLogRetrieval,' accepted a JSON Web Token (JWT) in the Authorization header and a phone number in the X-Ceq-MDN header. Although the JWT’s payload included the authenticated user's number as the sub (subject) field, the server did not enforce a check to ensure this matched the phone number being requested — an elementary yet critical oversight in access control.
Evan Connelly
Verizon Call Filter is a service designed to protect users from robocalls and spam, and is enabled by default for many, if not all, Verizon Wireless customers. The app is powered by infrastructure operated by Cequint, a lesser-known telecom technology provider specializing in caller ID services. Cequint’s involvement was inferred through domain analysis, as the vulnerable API was hosted on a server tied to the company (cequintvzwecid.com) and registered via GoDaddy — a peculiar choice for a major telecom operation.
Evan Connelly
Massive potential exposure
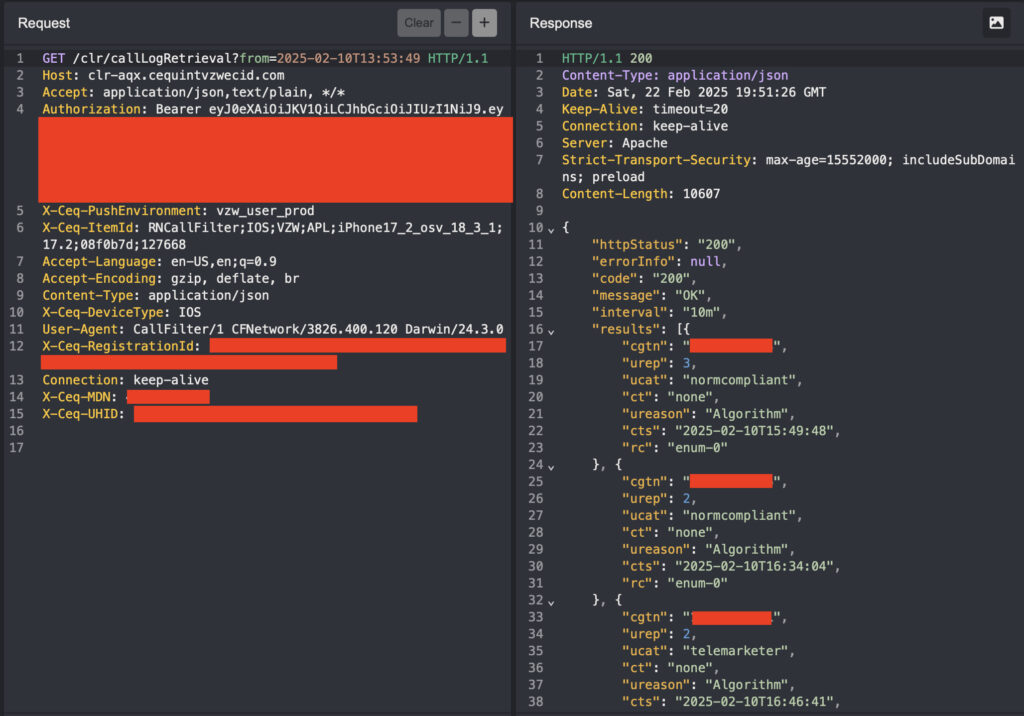
The implications of this flaw were severe. The exposed data included lists of received calls and timestamps, revealing patterns of communication and potential physical movement when cross-referenced with social media or other public data. While no content of the calls was accessible, call metadata alone is a powerful surveillance vector, capable of endangering sensitive individuals such as journalists, law enforcement officers, abuse survivors, and political figures.
The vulnerability also affected users beyond those specifically targeted. Because many Verizon subscribers likely had Call Filter enabled by default, the scope of potential exposure encompassed a large swath of the U.S. mobile user base. Even though only incoming call records were leaked, attackers could still piece together communication patterns — especially if multiple targeted users were within the Verizon network.
Following responsible disclosure, Verizon acknowledged the issue on February 24, 2025, and confirmed it was fixed by March 25, 2025, after the researcher verified the vulnerability had been mitigated. The exact date of patching remains unclear.
This incident highlights broader concerns about the role and accountability of third-party vendors like Cequint in managing sensitive telecom infrastructure. Cequint’s website is currently offline, and little public information is available about their data handling policies or security posture — raising questions about the oversight of firms entrusted with access to high-value telecom data.
Users should consider disabling services like Call Filter if not needed, especially when privacy is paramount. Periodic reviews of app permissions and account settings are also recommended to ensure minimal exposure to data leak risks.







My mother in law calls every night and if she doesn’t get anyone….engage panic mode.
Mid May all of a sudden her calls wouldn’t even ring, goes straight to voicemail.
We tried calling from her home to other people outside our family either Apple, android, AT&T even other Verizon customers and all calls went through and not to voicemail.
It was just effecting our family.
Called Verizon, they looked and researched and came up blank.
We reached out to Apple….nope.
My wife was digging around her account and Verizon installed a free Verizon call filter. She removed it from all our accounts and now my mother in law calls ring and no longer go directly to VM…..great job Verizon why didn’t you mention it?