
Cisco has issued a critical security advisory for its Smart Licensing Utility, highlighting two severe vulnerabilities that could allow remote attackers to gain control of systems or access sensitive data without authentication.
The vulnerabilities, identified as CVE-2024-20439 and CVE-2024-20440, received a critical CVSS score of 9.8. Both flaws stem from improper credential handling and excessive debug logging, with no current workarounds available. Cisco has released software updates to address these security issues.
The vulnerabilities were discovered by Eric Vance during internal security testing at Cisco. The first vulnerability, CVE-2024-20439, is due to an undocumented static administrative credential in the Cisco Smart Licensing Utility. This flaw allows an attacker to gain administrative privileges by exploiting the static credential to log in through the API. Once inside, attackers could potentially control and configure licensing services.
The second issue, CVE-2024-20440, involves excessive verbosity in a debug log file, which could allow an attacker to access sensitive information, including credentials, by sending specially crafted HTTP requests. These credentials could then be used to further exploit the system’s API.
Affected are systems that are running vulnerable releases of the Cisco Smart Licensing Utility, as long as the service is actively running. Cisco clarified that the vulnerabilities are independent of each other and do not require exploitation of one to take advantage of the other. However, both pose significant risks due to the potential for unauthorized system access and data breaches.
Cisco
Cisco Smart Licensing Utility is a tool used by businesses to manage and monitor software licenses across their Cisco products. This service is crucial for organizations that use Cisco’s wide array of networking and communication solutions. Since the vulnerabilities affect systems that rely on this tool, the implications could be severe for companies relying on Cisco’s licensing solutions.
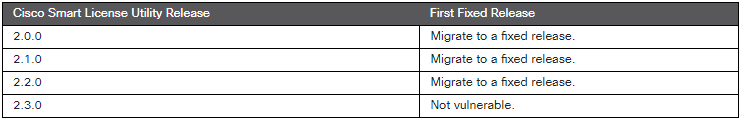
To mitigate the risk, Cisco has released fixed software versions and urges all affected users to update their systems immediately. There are no temporary fixes or workarounds, and the only defense is to upgrade to a patched version. Users can check for the appropriate fixed releases on Cisco’s advisory page, which lists the affected versions and provides guidance on securing their systems.







Leave a Reply