
Hudson Rock has exposed widespread infostealer malware infections affecting employees in the U.S. military, government agencies, and major defense contractors.
The findings reveal that compromised credentials — available for as little as $10 on cybercrime marketplaces — could be exploited to gain unauthorized access to classified networks, VPNs, email systems, and development tools.
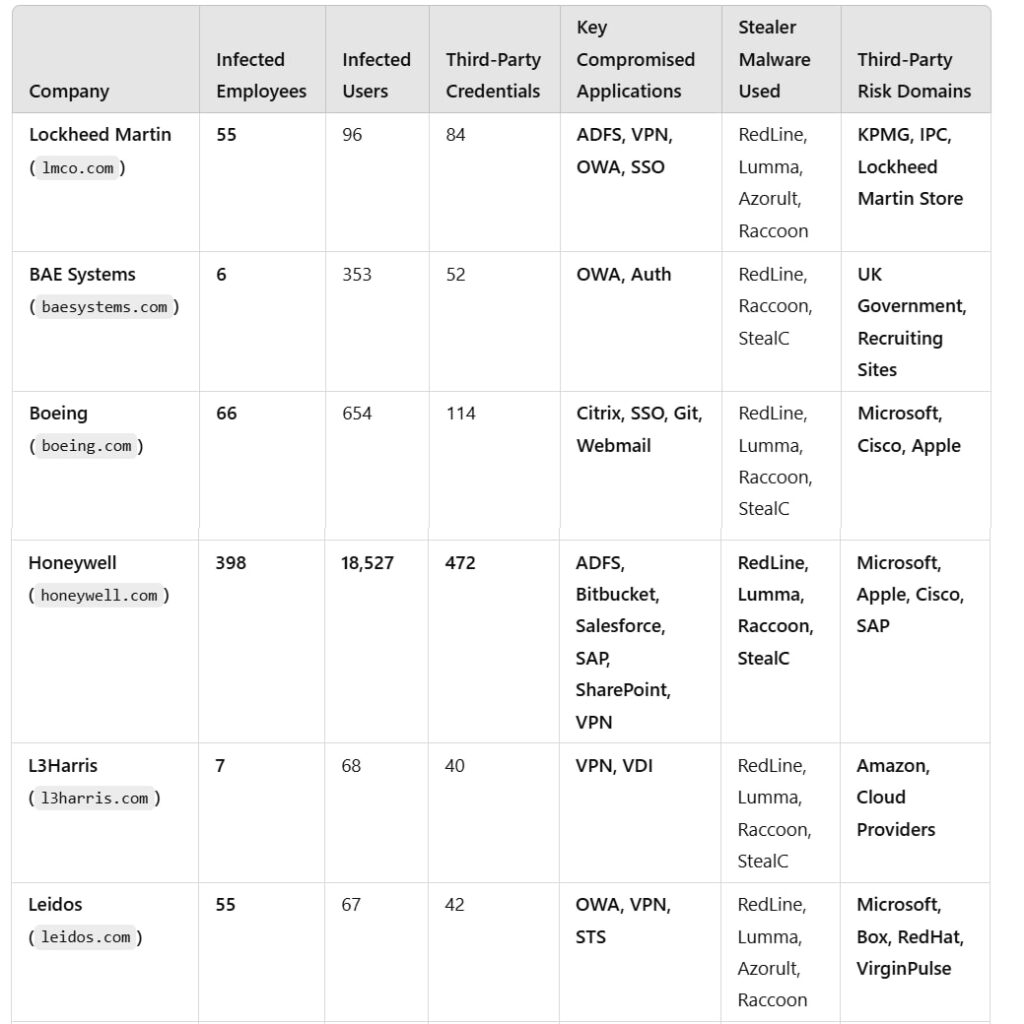
Hudson Rock’s report highlights significant breaches at some of the most critical organizations in U.S. national security, including Lockheed Martin, Boeing, and Honeywell, as well as the U.S. Army, Navy, FBI, and Government Accountability Office (GAO). These infections expose login credentials, multi-factor authentication (MFA) session cookies, and access to sensitive internal tools such as GitHub, Jira, and SharePoint.
The malware responsible for these breaches, infostealers, does not rely on brute-force attacks but instead extracts stored credentials from infected devices. Victims unknowingly download the malware through infected PDFs, game modifications, or pirated software, allowing cybercriminals to collect:
- VPN credentials for secure military and contractor networks
- MFA session cookies to bypass authentication barriers
- Email logins for government and defense agencies
- Development tool access for internal software projects
- Stored documents, browser autofill data, and history
This attack effectively transforms compromised employees into insider threats, potentially providing adversaries the means to move laterally within classified networks.
Hudson Rock
One of the most alarming cases uncovered by Hudson Rock involves Honeywell, a key player in aerospace and defense manufacturing. Over the years, 398 Honeywell employees have been infected, leaking login credentials for internal authentication portals, development tools, and cloud integrations with Microsoft, Cisco, and SAP.
A 30-year veteran engineer at Honeywell, for instance, was found to have 56 corporate credentials and 45 third-party credentials compromised. Among the exposed login portals were:
- Honeywell’s internal intranet for employee communications
- Active Directory Federation Services (ADFS), used for single sign-on (SSO) access
- Identity and Access Management (IAM) tools controlling user permissions
This breach underscores the systemic risk of infostealer infections in defense supply chains. Even firms that maintain strong cybersecurity hygiene can be compromised indirectly if their partners, vendors, or subcontractors are infected.
The report also reveals that 30 U.S. Navy personnel had their credentials stolen, exposing authentication data for critical systems like Outlook Web Access (OWA), Citrix, and FTP servers. Additionally, 256 third-party credentials tied to military training platforms and security software were leaked, raising concerns about the possibility of state-sponsored cyber intrusions.
Even the FBI and GAO, which oversee national security investigations and cybersecurity policies, had employees with compromised credentials — highlighting the vulnerability of even the most security-conscious organizations.
The findings from Hudson Rock paint a disturbing picture of national security risks posed by infostealer malware. The ease with which stolen credentials can be purchased on cybercrime marketplaces underscores the urgency for enhanced cybersecurity measures that, unfortunately, for now, aren’t there.







Leave a Reply