
In the wake of a Cyber Safety Review Board (CSRB) report on the 2023 compromise of Microsoft Exchange Online by the hacking group Storm-0558, the U.S. government has pointed fingers at Microsoft for a series of security missteps that made the breach possible.
The incident, which saw the compromise of email accounts belonging to top U.S. officials, among others, resulted from “a cascade of security failures at Microsoft,” according to the CSRB.
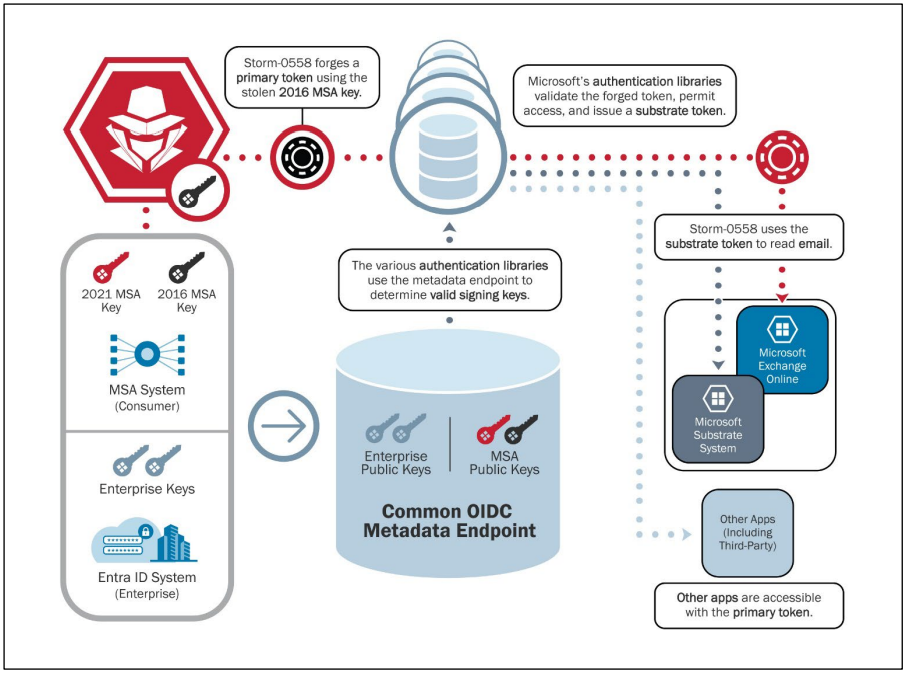
The intrusion, executed by Storm-0558 (APT31), a group linked to the Chinese government, exploited a key Microsoft created in 2016 to gain access to senior U.S. officials' official email accounts. This breach was not only a significant espionage win for China but also a stark reminder of the vulnerabilities inherent in cloud services, which have become ubiquitous in managing sensitive data globally.
Storm-0558 is a sophisticated China-based cyber espionage group active since around 2000, targeting diplomatic, economic, and technological sectors primarily for intelligence gathering to support the People's Republic of China's strategic objectives.
The report highlights a series of missteps by Microsoft that contributed to the breach. Firstly, the 2016 Microsoft Services Account (MSA) cryptographic key, which should have been retired in 2021, was still active due to delays in hardening the consumer key systems. Moreover, a flaw in Microsoft's token validation system allowed the hackers to use this key to access not just consumer but also enterprise email accounts, indicating a failure in properly segmenting and securing different parts of Microsoft's cloud infrastructure.
CSRB
The CSRB concluded that the intrusion was preventable, criticizing Microsoft's security culture and practices. It noted Microsoft's failure to detect the compromise of its cryptographic “crown jewels” independently, relying instead on an alert from a customer. The report also underscored the importance of cloud service providers (CSPs) like Microsoft in prioritizing security to protect the critical data they manage.
In response to the incident, the CSRB made several recommendations, including urging Microsoft to overhaul its security culture, focus on fundamental security-focused reforms, and improve transparency and accountability in its operations. It also called for industry-wide improvements in digital identity standards, victim notification processes, and audit logging norms to bolster cybersecurity resilience.
This incident serves as a wake-up call for CSPs to reassess their security frameworks and for customers to demand higher standards of accountability and transparency. The breach underscores the challenges of securing cloud environments against sophisticated nation-state actors and the need for constant vigilance and improvement in cybersecurity practices.







Leave a Reply