
Researchers from ESET have unveiled a sophisticated cyber-espionage campaign targeting a European ministry of foreign affairs with advanced backdoors named LunarWeb and LunarMail.
The cyberespionage tools, likely deployed by the Russia-aligned Turla APT group since 2020, demonstrate sophisticated tactics and techniques, raising significant security concerns for government entities and diplomatic missions globally.
Discovery and attribution
The detection of Turla's malicious activities was credited to Filip Jurčacko and the ESET research team. Their investigation began with identifying a suspicious loader decrypting a payload on an unidentified server. The depth of the analysis revealed the two novel backdoors, part of a broader toolkit referred to as the “Lunar toolset.” Based on the operational tactics, techniques, and procedures (TTPs), ESET attributed these attacks to the Turla group, known for its alignment with Russian intelligence operations.
Turla has a notorious history dating back to the early 2000s, targeting high-profile government and diplomatic institutions across Europe, Central Asia, and the Middle East. Their sophisticated strategies include the compromise of the US Department of Defense in 2008 and the Swiss defense company RUAG in 2014.
LunarWeb and LunarMail
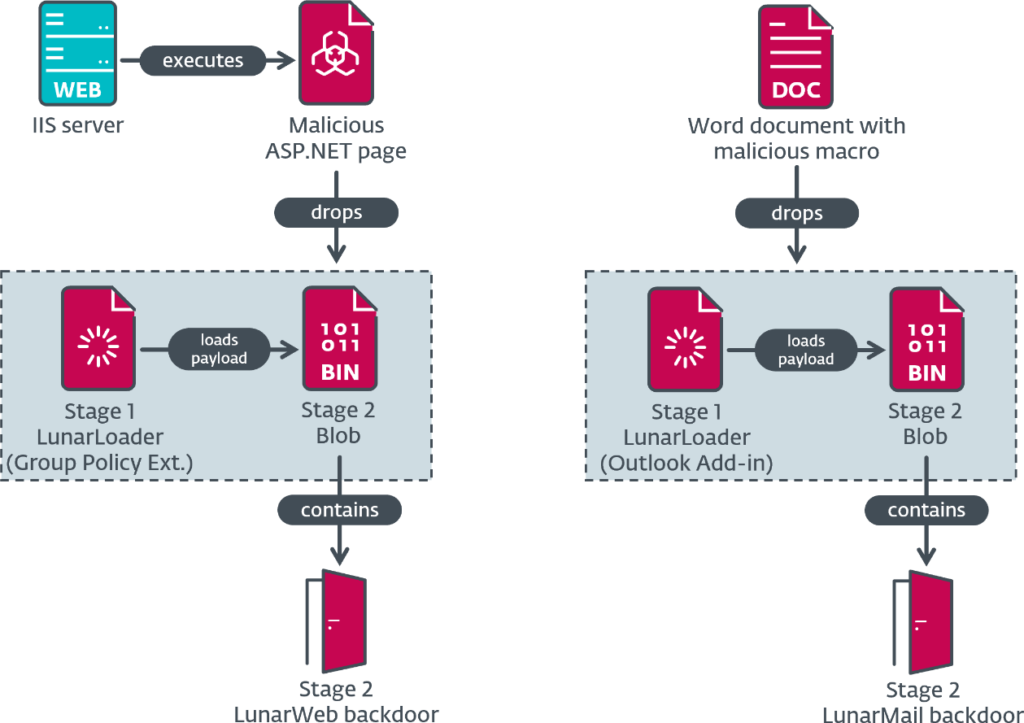
The LunarWeb backdoor was primarily deployed on servers, utilizing HTTP(S) communications masked as legitimate traffic to camouflage its presence and operations within the network. It employed advanced techniques such as steganography—hiding commands within images—to evade detection.
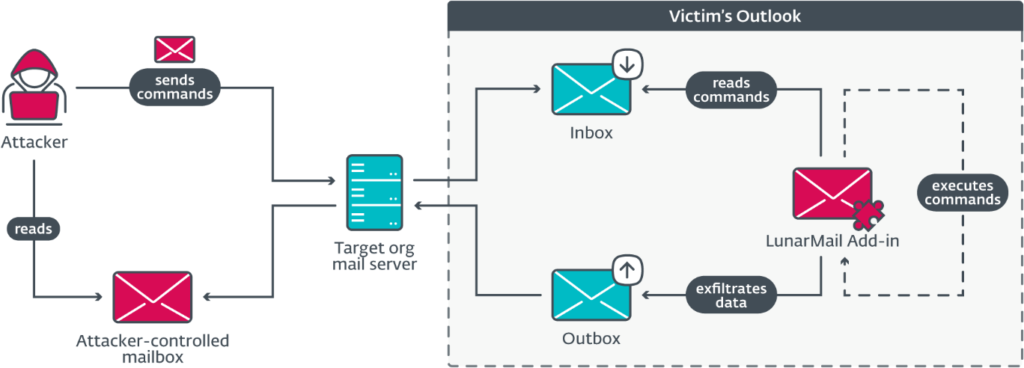
Meanwhile, LunarMail targeted workstation levels, integrating itself as an Outlook add-in and using email messages for its command and control (C&C) operations.
ESET
Both backdoors shared common features, including the capability to execute Lua scripts and a loader utilizing the DNS domain name for decrypting payloads, demonstrating the intricacies of Turla's operational tactics.
Initial entry points for these attacks were varied, including potential spearphishing and the exploitation of misconfigured network monitoring software, such as Zabbix. The attackers adeptly mimicked legitimate network logs and used compromised emails to execute their backdoors. Once inside, they demonstrated capabilities for lateral movement and persistence, illustrating a deep understanding of network topologies and security systems.
ESET
Defense recommendations
Given the complexity and stealth of the Lunar toolset, organizations, particularly governmental and diplomatic bodies, must adopt robust, multi-layered security strategies. This includes regular auditing of network configurations, continuous monitoring for anomalous activities, and comprehensive endpoint protection.
Enhancing user awareness about spearphishing and maintaining up-to-date system patches are also critical in defending against such sophisticated threats.







Leave a Reply