
Threat actors are selling over 18,317 AnyDesk credentials on the hacking forum “Exploit[.]in” for $15,000, one day after the maker of the popular remote access tool disclosed a catastrophic data breach.
AnyDesk is a remote desktop application that allows users to access and control computers from anywhere in the world. It’s known for its speed and lightweight design, making it a popular choice for IT professionals, businesses, and individual users who need remote access to their computers or want to provide remote support to others.
As previously seen in cases like the Mitsu stealer and the HotRAT malware, AnyDesk is both a lucrative target and an effective bait for cybercriminals, thanks to the software’s popularity and widespread use in high-value environments.
On February 2, 2024, AnyDesk announced that it suffered a cyberattack that compromised its production systems. The firm collaborated with CrowdStrike to contain the threat and later took extensive security measures, including revoking and replacing certificates. The software vendor also advised users to change their passwords immediately, though it assured that no user devices had been affected by the incident.
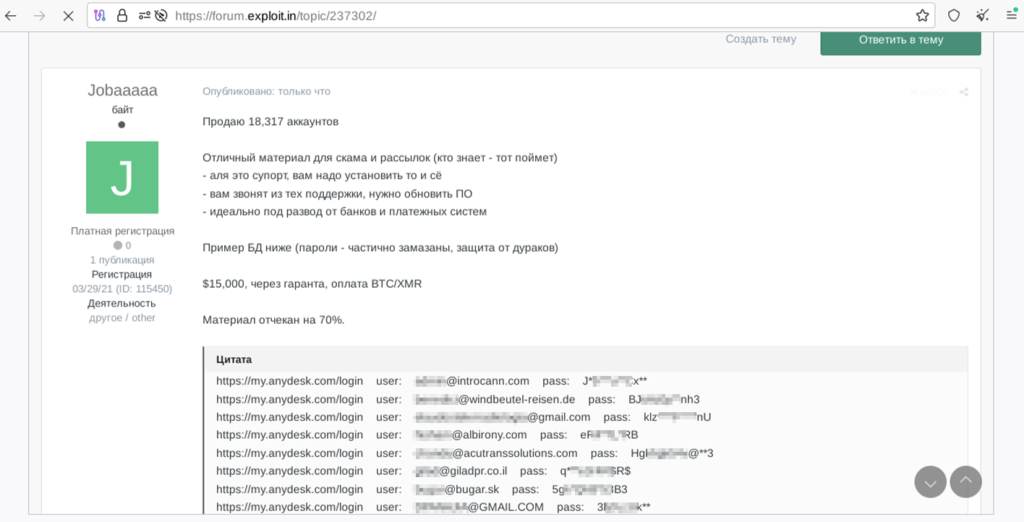
Researchers at Resecurity who discovered the AnyDesk credentials sale online report that the situation might be more complicated than the vendor cares to admit. A user named “Jobaaaaa” is selling a large set of AnyDesk account credentials on a hacking forum, which threat actors could leverage to establish remote access to sensitive computer systems or perform lateral phishing from within breached networks.
Resecurity
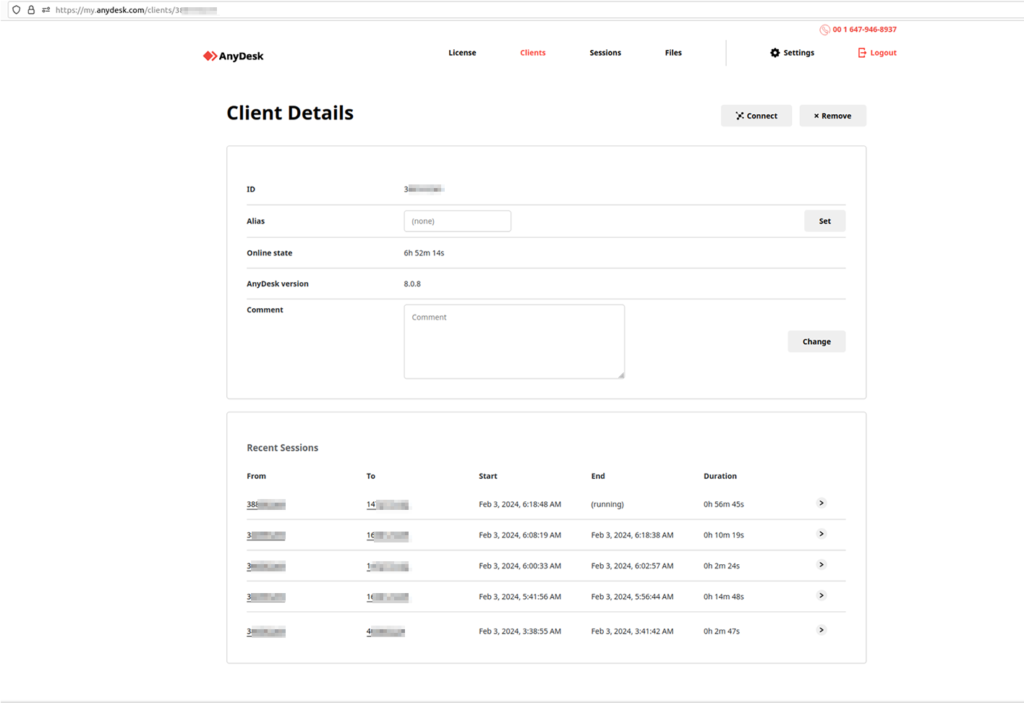
Also, by accessing other people’s AnyDesk accounts, buyers of this set can access their license key, connection details, session info, email address, account status, and other valuable data that can be used for effective social engineering and scams. According to the seller’s screenshots, some of the impacted accounts were accessed on February 3, so the unauthorized activity took place after the disclosure of the data breach.
Resecurity
Resecurity has validated parts of the data found in the samples shared for free by Jobaaaa and confirms that it is authentic, belonging to people who are currently using AnyDesk, or used it at some point in the past.
On the subject of how those credentials were acquired, Resecurity cannot draw safe conclusions given the available evidence.
“The sources and methods for acquiring data of this nature may vary depending on threat actors’ unique Tactics, Techniques, and Procedures (TTPs),” reads the Resecurity report.
“While this credential leak is widely believed to be the result of infostealer infections, this uncertainty nevertheless creates a new area of concern.”
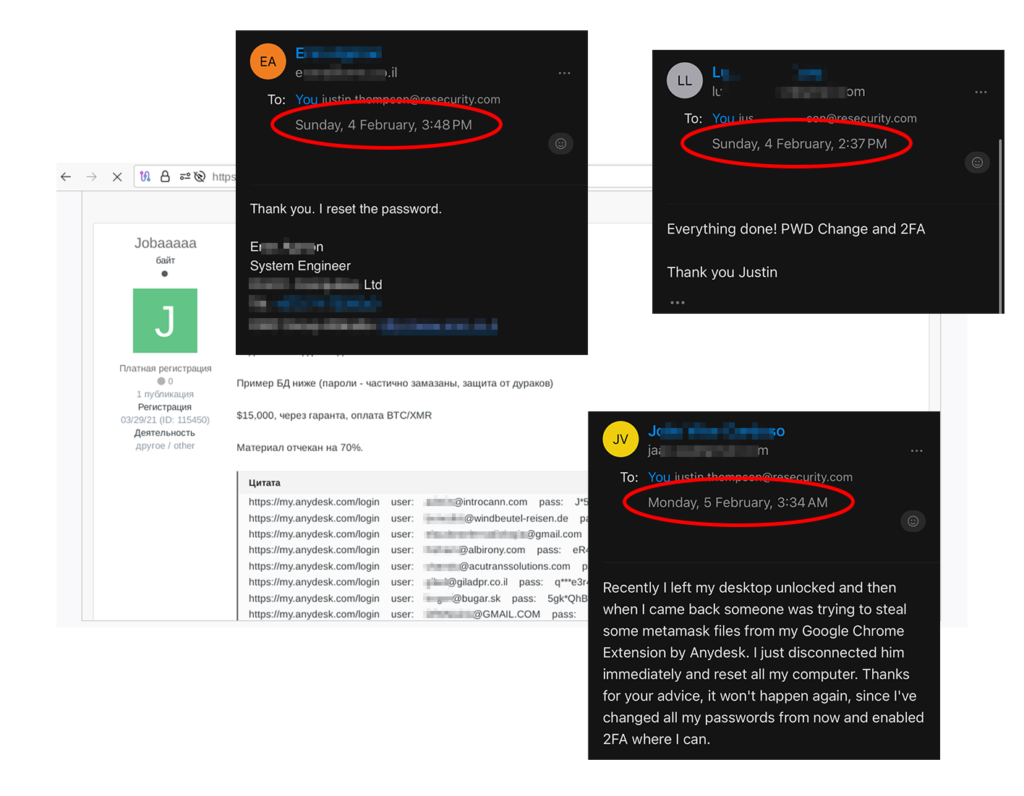
If the dataset, which has yet to be confirmed as authentic, is real, AnyDesk should move quickly to impose a global password reset despite the operational disruption that this may cause. Also, implementing a mandatory two-factor authentication (2FA) step for all AnyDesk accounts would be a very effective security measure in preventing these hijacks.
Resecurity
Unfortunately, it took AnyDesk several days to publicly admit the cybersecurity incident, and the software vendor has not shared all the details about it yet. This has left many users in the dark about what has happened, and a notable percentage of them still need to take appropriate action to secure their accounts (password reset + MFA).
Resecurity recommends that AnyDesk admins reset all user passwords, enable 2FA, monitor activity logs, and set up whitelists that only allow connections to trusted user IDs and namespaces.
Further reading:
- Fake AnyDesk Website Pushes new Stealer Malware “Mitsu”
- CyberGhost VPN Client Vulnerable to Man-in-the-Middle Attacks
- Razer Investigating Data Leak After Files Appear on Hacker Forum
- Internet Giant Cloudflare Hacked by Nation-State Using Okta Token
- Why You Shouldn’t Be Worried About MOAB, the “Mother of All Breaches”







Leave a Reply