
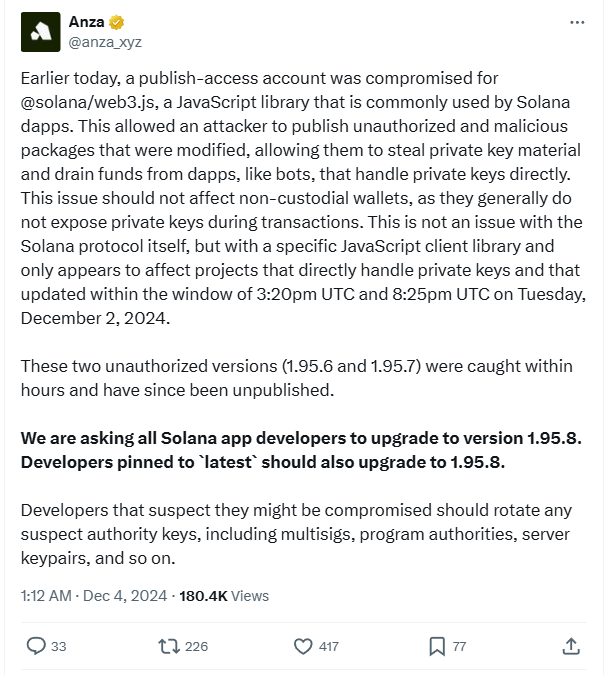
A supply chain attack has compromised versions 1.95.6 and 1.95.7 of the @solana/web3.js library, a critical JavaScript tool widely used for building Solana blockchain applications. The library, which sees over 350,000 weekly downloads on npm, contained malicious code that could steal private keys, posing significant risks to developers and end-users.
The issue came to light on December 3, 2024, and involves injected code that exfiltrates private keys to a hardcoded Solana address: FnvLGtucz4E1ppJHRTev6Qv4X7g8Pw6WPStHCcbAKbfx. Developers integrating the compromised versions risk exposing sensitive keys, potentially enabling attackers to drain funds from affected cryptocurrency wallets.
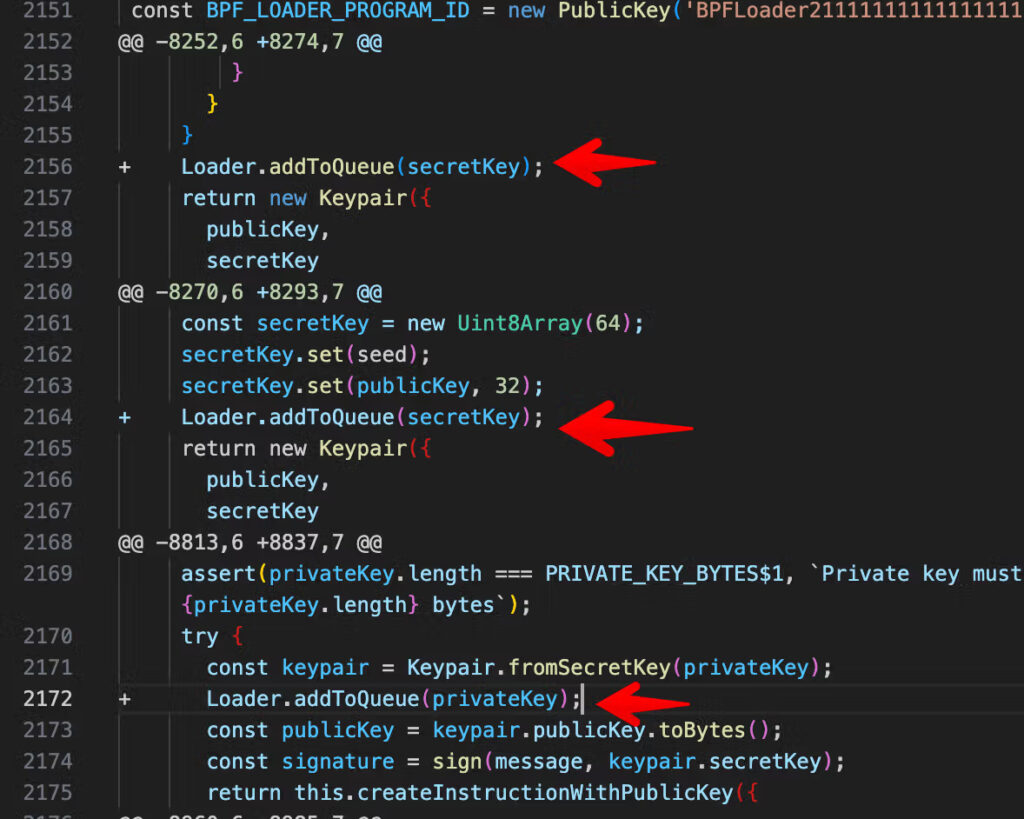
Security researchers believe the attack was the result of a phishing or social engineering campaign targeting maintainers of the @solana/web3.js library. Christophe Tafani-Dereeper, a cloud security researcher at Datadog, analyzed the malicious updates and noted that the injected “addToQueue” function exfiltrates private keys via Cloudflare headers. This functionality was concealed within legitimate code paths, making detection difficult. The command-and-control (C2) server, hosted on the domain sol-rpc[.]xyz (registered on November 22), is currently inactive.
Socket
This issue primarily affects:
- Developers using @solana/web3.js versions 1.95.6 or 1.95.7 may expose private keys in their applications.
- Users with wallets managed by applications that rely on these versions are vulnerable if private keys are handled directly.
Importantly, non-custodial wallets remain unaffected, as they do not expose private keys during transactions. Anza, a Solana-focused research and development firm, clarified that this attack stems from a compromised publish-access account rather than an inherent flaw in the Solana protocol.
Immediate actions for developers
- Audit Dependencies: Check all projects for the usage of @solana/web3.js versions 1.95.6 or 1.95.7.
- Rollback or Update: Revert to a version prior to 1.95.6 or upgrade to the newly released version 1.95.8, which has removed the backdoor.
- Inspect Code: Examine the node_modules directory for suspicious modifications.
- Revoke Access: Regenerate any compromised keys and revoke permissions associated with them.
Developers can also use tools like Socket’s CLI scanner (socket scan create .) to detect affected dependencies in their repositories.
npm has acted promptly to remove the malicious versions from its registry, limiting further downloads. While this prevents new users from acquiring the compromised library, existing implementations remain at risk.







Leave a Reply