
A critical security vulnerability in Subaru's STARLINK-connected vehicle service exposed all Subaru vehicles and customer accounts in the U.S., Canada, and Japan to potential remote hijacking, tracking, and data theft. The flaw, discovered by security researchers Sam Curry and Shubham Shah on November 20, 2024, allowed attackers to unlock, start, stop, and track any Subaru vehicle using minimal personal information. Subaru patched the issue within 24 hours of receiving the report.
Curry and Shah began their investigation by auditing the MySubaru mobile app, which allows users to control their vehicles remotely. Despite a thorough examination using Burp Suite to intercept telematics requests, they found no immediate security gaps. However, their approach shifted when they discovered an internal Subaru employee portal, STARLINK Admin Panel, by analyzing subarucs.com domain subdomains.
Through brute-forcing hidden JavaScript files, they found a password reset vulnerability that allowed them to reset any employee's password without email verification. By using LinkedIn to identify Subaru employees and a security question enumeration flaw, they confirmed valid email accounts and successfully took over an admin account.
samcurry.net
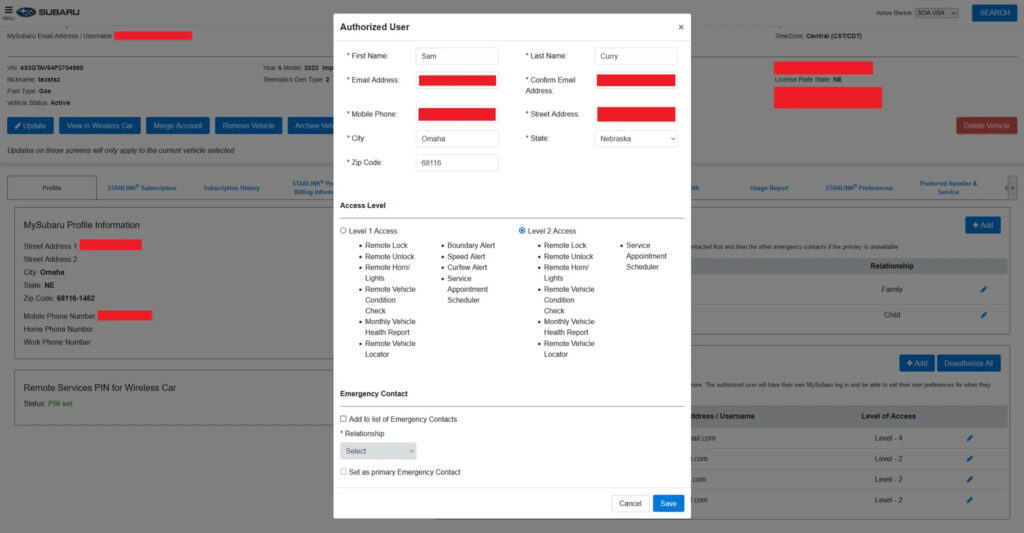
Once inside the STARLINK Admin Panel, the researchers bypassed two-factor authentication (2FA) by simply removing the client-side overlay in the website's JavaScript. With full access, they could:
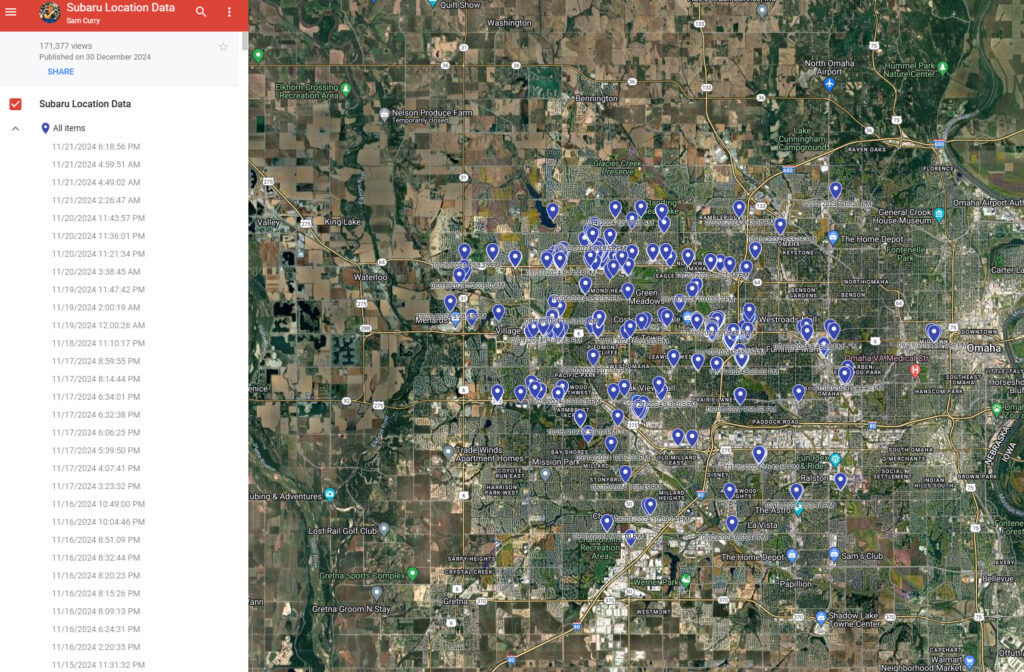
- Track any Subaru vehicle in real-time and retrieve one year of location history, down to 5-meter accuracy.
- Unlock, start, and stop any Subaru remotely.
- Modify vehicle access permissions, allowing them to add unauthorized users.
- Retrieve personal customer data, including emergency contacts, home addresses, phone numbers, and partial billing details.
samcurry.net
To confirm the severity of the exploit, they tested it on a friend's vehicle using only the license plate number. Within seconds, they unlocked the car remotely — with no alert or notification sent to the owner.

Millions of Subaru cars at risk
Subaru Corporation, a major Japanese automaker, has a strong presence in North America and Asia, with millions of vehicles equipped with STARLINK — its connected car system for remote access, diagnostics, and security features. This vulnerability exposed every internet-connected Subaru vehicle in multiple countries to potential abuse, putting customer safety and privacy at serious risk.
Despite the severity, Subaru's security team responded swiftly, patching the flaw within 17 hours of being notified. They also stated that the flaw had not been exploited maliciously, although it's doubtful they could determine this with any certainty, given that the attack does not leave any traces.
Vehicle owners should regularly check their connected car accounts for unauthorized users/access and review privacy settings. With more vehicles integrating cloud-based remote management features, car owners should bear in mind that large-scale abuse and remote attacks, often totally stealthy, are plausible scenarios.







Leave a Reply