
Microsoft Threat Intelligence has uncovered a new spear-phishing campaign by the Russian threat actor Star Blizzard, marking a significant shift in their tactics. The campaign, observed in mid-November 2024, exploits WhatsApp’s account linking feature to gain unauthorized access to messages. This is the first time Star Blizzard has used WhatsApp as an attack vector, following previous disruptions to their infrastructure by Microsoft and U.S. law enforcement.
Star Blizzard, previously known for targeting government officials, diplomats, defense policy researchers, and NGOs related to Ukraine, traditionally relied on email phishing to steal sensitive data. However, after Microsoft and the U.S. Department of Justice took down more than 180 of their phishing websites in October 2024, the group quickly adapted by shifting to new domains. Now, they have changed their approach entirely by compromising WhatsApp accounts.
Microsoft assesses that this pivot was likely a response to heightened scrutiny from cybersecurity firms and national security agencies. Although the campaign wound down by late November, the move underscores Star Blizzard’s persistence and adaptability.
Targeting WhatsApp accounts
The phishing attempt begins with an email impersonating a U.S. government official, a known tactic of Star Blizzard to establish credibility. The email invites the recipient to join a WhatsApp group focused on supporting NGOs in Ukraine and includes a QR code for joining. However, the QR code is intentionally broken, prompting the recipient to respond to the email.

Microsoft
If the target replies, the attackers send a second email containing a t[.]ly-shortened malicious link wrapped with Microsoft Safe Links to appear legitimate. When the victim clicks this link, they are redirected to a webpage with a new QR code, which mimics WhatsApp’s device-linking feature. If scanned, this QR code grants Star Blizzard access to the victim’s WhatsApp account, allowing them to view and exfiltrate messages using common browser plugins designed for exporting WhatsApp chat data.
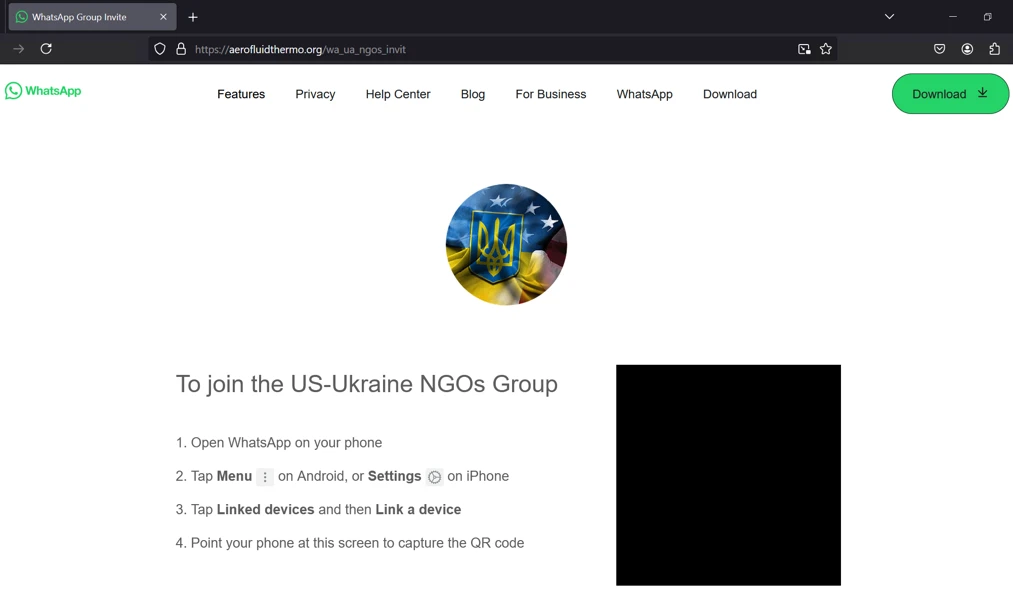
Microsoft
Persistent threat to high-profile targets
Star Blizzard has been a longstanding cyber threat, primarily focusing on intelligence gathering and disinformation campaigns. The group has previously attacked civil society organizations, including journalists, think tanks, and NGOs, to interfere with their operations. Their latest move to exploit WhatsApp highlights their ability to quickly adapt to disruptions and find new ways to compromise targets.
Microsoft has notified organizations and individuals affected by this attack and is urging potential targets to remain vigilant against phishing emails. Given Star Blizzard’s history, it is likely they will continue refining their tactics to evade detection.
To mitigate risks associated with this campaign, organizations and individuals in targeted sectors should:
- Be cautious of unsolicited emails, especially those containing QR codes or links to external sites.
- Verify the sender’s identity by contacting them through a previously used and trusted email address.
- Enable multi-factor authentication (MFA) for WhatsApp and other sensitive accounts.







Leave a Reply