
A research led by a team at Concordia University Montreal and the Hydro-Québec Research Institute has identified critical security vulnerabilities within the Open Charge Point Protocol (OCPP) backends used extensively in Electric Vehicle Charging Stations (EVCSs) worldwide. These flaws could potentially allow attackers to execute a range of cyber-attacks, including denial of service, firmware theft, and data poisoning.
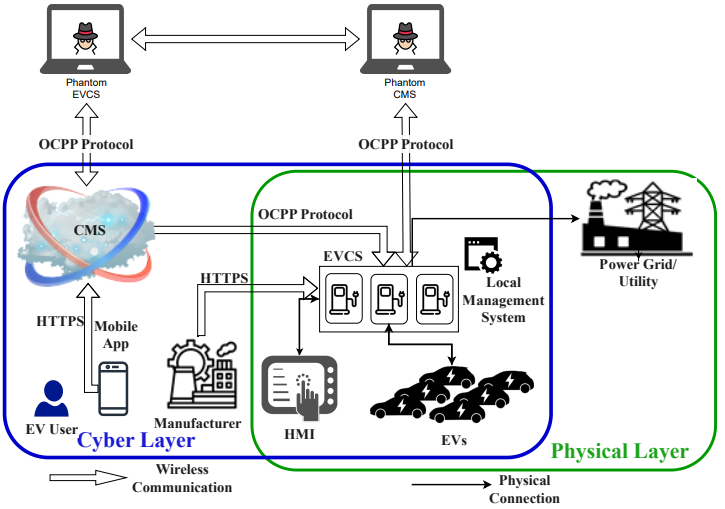
The rapid expansion of the EV market has necessitated a swift scale-up in charging infrastructure, which has inadvertently introduced security oversights. The researchers, including Khaled Sarieddine, Mohammad Ali Sayed, and Ribal Atallah, focused on the security of the EVCS Cloud Management System (CMS), particularly the interaction between EVCSs and the OCPP backend. They discovered six zero-day vulnerabilities across 16 different live systems used worldwide.
EV charging risks
The research, which is to be presented in the upcoming Asia CCS, highlights that the OCPP backend, a critical component in the communication chain between charging stations and the central management system, is plagued with security issues.
The vulnerabilities were identified through a custom-developed testbed that simulates real-world EVCS environments. The identified vulnerabilities include weak authentication processes, failure to limit the frequency of backend communications, and inadequate session management, among others.
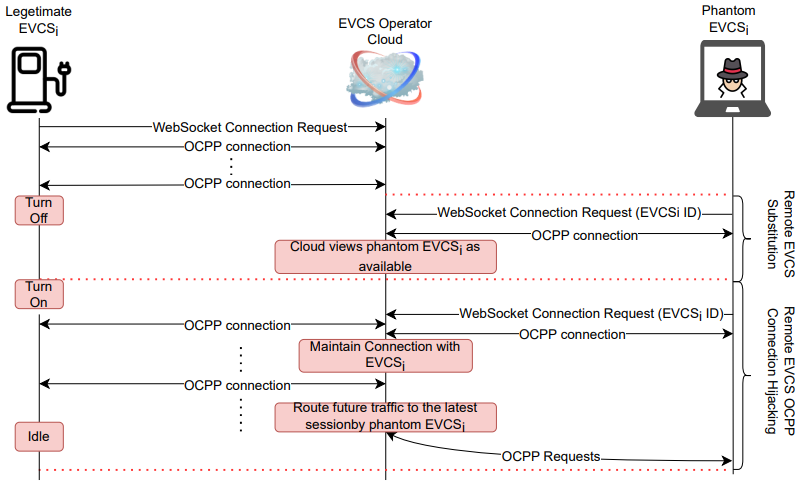
These vulnerabilities allow several attack vectors, such as:
- Man-in-the-Middle Attacks: Where attackers can intercept and alter communications between the charging station and the CMS.
- Denial of Service (DoS): Attackers could disrupt the service availability of EVCSs, affecting the reliability of charging infrastructure.
- Firmware Theft and Data Poisoning: Potential theft of proprietary firmware and manipulation of operational data to mislead decision-making or degrade system integrity.
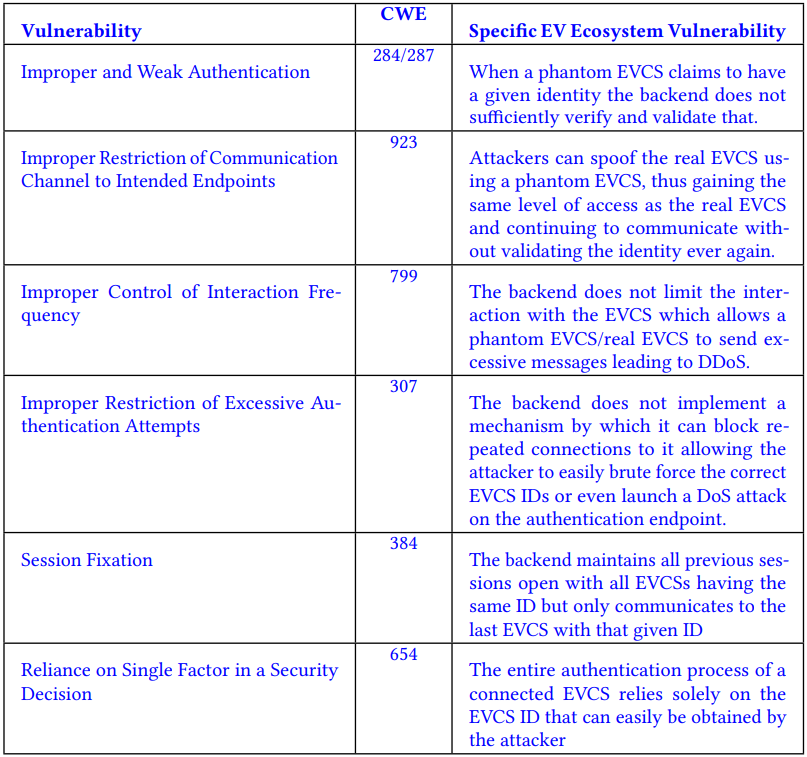
Recommendations for mitigation
The researchers have proposed several countermeasures in the available pre-print to mitigate these vulnerabilities, including:
- Implementing robust authentication mechanisms to ensure that only legitimate devices can interact with the backend.
- Enhancing monitoring and control mechanisms to detect and respond to unusual activities.
- Employing end-to-end encryption to safeguard communication data integrity and confidentiality.
- Conclusion and Next Steps:
- This study underscores the critical need for improved security measures as the infrastructure for electric vehicles continues to grow. The researchers have communicated their findings with the affected vendors, allowing them time to patch the vulnerabilities before the details were made public.
Moving forward, it is imperative for operators and manufacturers to collaborate closely to address these security gaps and ensure the resilience of the rapidly expanding EV charging infrastructure. The industry must adopt a proactive approach to security, integrating robust security practices throughout the design and deployment of EVCSs.







Leave a Reply