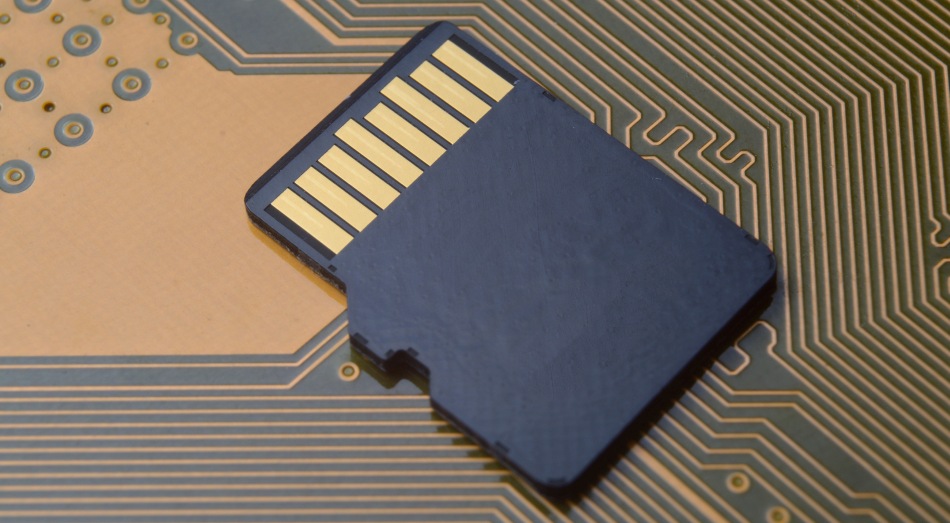
A recent Positive Technologies report sheds light on a novel vulnerability named DaMAgeCard, allowing attackers to exploit SD Express memory cards for direct access to system memory. This issue leverages the Direct Memory Access (DMA) feature introduced in SD Express to accelerate data transfer speeds but opens the door for sophisticated attacks on devices that support the standard. Researchers demonstrated how modified SD Express cards could bypass system protections like IOMMU, posing a significant threat to gaming consoles, laptops, and other high-speed media devices.
Understanding DaMAgeCard
Positive Technologies, led by embedded systems researchers, discovered the vulnerability during routine investigations into SD Express. The standard, first introduced in 2018, gained traction with devices adopting PCIe-based data transfer capabilities to achieve faster speeds. Despite the potential of SD Express for high-speed applications, the team identified gaps in how the industry secured its DMA functionalities.
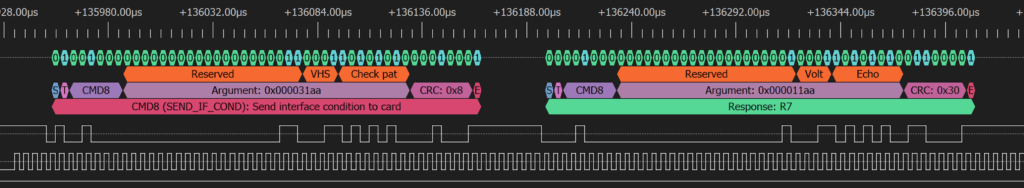
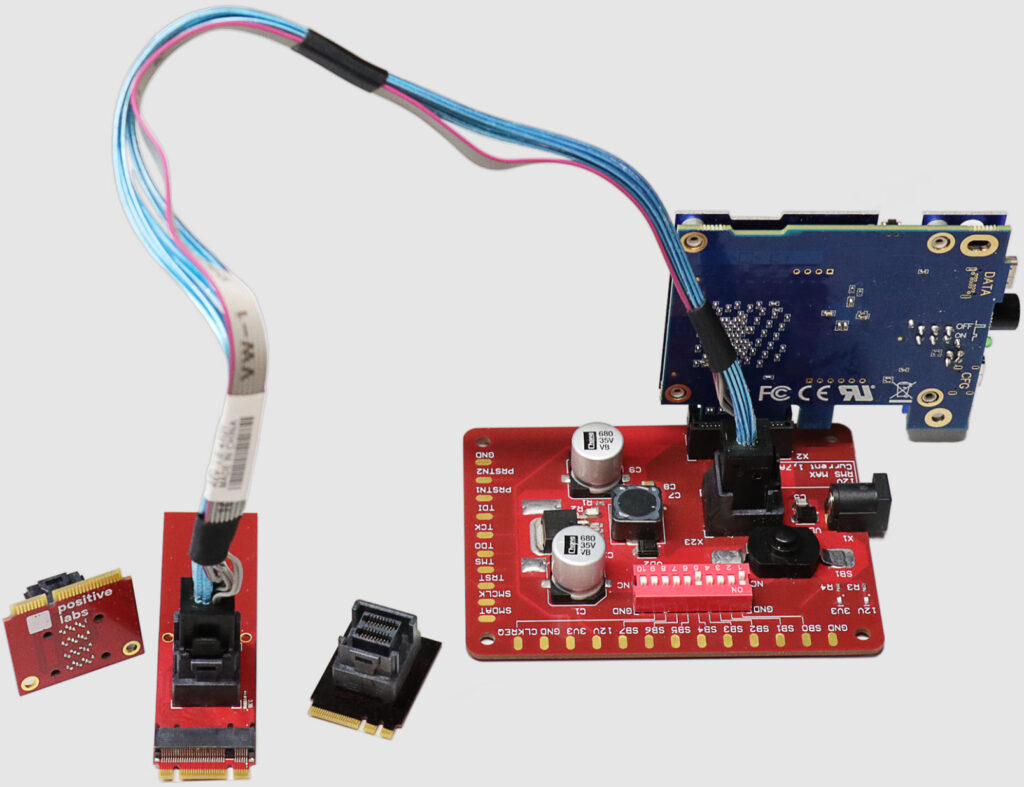
Using custom hardware modifications, the researchers demonstrated successful memory access on systems like the MSI gaming laptop and AYANEO Air Plus handheld console, revealing a lack of sufficient safeguards in devices transitioning between SDIO (legacy SD protocol) and PCIe modes.
Positive Technologies
SD Express, designed by the SD Association, combines legacy SD technology with PCIe and NVMe protocols to achieve transfer rates up to 985 MB/s. This performance boost, essential for managing large media files, introduced PCIe Bus Mastering, a feature allowing SD cards to access system memory directly. While intended to bypass CPU bottlenecks for speed, the implementation fails to adequately restrict unauthorized memory access.
The Realtek RTS5261 host controller and similar components allow SD Express cards to operate as PCIe NVMe devices once connected. This transition is where DaMAgeCard capitalizes: attackers can exploit poorly implemented controls to manipulate devices and access sensitive memory regions.
Positive Technologies
Impacted systems and risks
SD Express adoption is still relatively limited but growing, with high-end laptops, gaming consoles, and media devices incorporating the standard. Potentially impacted systems are listed below.
- Gaming consoles like the AYANEO Air Plus lack IOMMU protection, allowing unfiltered access to memory.
- Laptops, even including high-end systems with IOMMU like the MSI gaming laptops, could be manipulated to permit unauthorized DMA access through modified SD Express cards.
- PCIe-based external readers.
- Photography equipment, video cameras, and other embedded systems requiring high-speed data handling, where SD Express is a preferred standard.
Positive Technologies
To safeguard against DaMAgeCard and similar DMA-based attacks, Positive Technologies recommends the following measures:
- Ensure IOMMU is active on all PCIe-capable devices.
- Configure systems to restrict direct memory access to trusted devices only.
- Apply the latest firmware updates that might enforce secure transitions between SDIO and PCIe modes or verify SD Express cards through cryptographic signatures before granting DMA privileges.
- Disable hotplugging if not needed to prevent unauthorized device connections.
- Avoid using unfamiliar SD cards or external readers with sensitive systems.
- Inspect devices regularly for tampering, especially in shared environments.
The DaMAgeCard vulnerability underscores the challenges of balancing performance with security in modern peripheral standards like SD Express. As adoption grows, device manufacturers must prioritize implementing robust protections against DMA-based threats. Until then, users should remain vigilant, updating their systems and limiting exposure to unverified devices.







Leave a Reply