
In an extraordinary case of cyber-espionage, the Russian state-sponsored group Secret Blizzard has been revealed to have hijacked the infrastructure of other hacking groups for its operations, with a recent campaign targeting the Pakistan-based espionage cluster Storm-0156 (also known as SideCopy, Transparent Tribe, or APT36).
Secret Blizzard, identified by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) as operating under Russia's Federal Security Service (FSB), has a track record of targeting ministries, embassies, and defense organizations worldwide. Unlike many other groups, Secret Blizzard often repurposes tools from state-sponsored and criminal actors.
Simultaneously published reports from Microsoft Threat Intelligence and Lumen's Black Lotus Labs highlight how Secret Blizzard turned Storm-0156's command-and-control (C2) servers into a platform to collect intelligence from Afghan and Indian networks.
This method — leveraging another group's tools and access — allows Secret Blizzard to obscure its operations and complicate attribution, a hallmark of their tradecraft that has been seen in multiple campaigns over the last seven years.
Their previous campaigns include leveraging Iranian group Hazel Sandstorm's infrastructure in 2017, reusing the Andromeda malware in 2022 to deploy QuietCanary backdoors, and compromising Kazakhstan-based group Storm-0473 in attempts to target Ukrainian networks.
Hijacking Storm-0156's operations
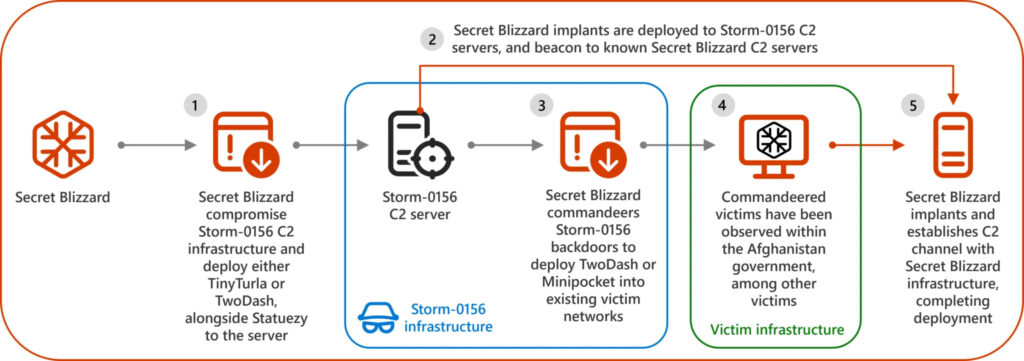
Secret Blizzard first infiltrated Storm-0156's infrastructure in late 2022, beginning with a C2 server used to store exfiltrated data from Afghan and Indian targets. Over time, Secret Blizzard expanded their reach across 33 of Storm-0156's nodes. By mid-2023, they used this privileged access to deploy their own malware, including the TwoDash downloader and the Statuezy clipboard monitor. These tools were injected into Afghan government networks, such as the Ministry of Foreign Affairs and the General Directorate of Intelligence.
Storm-0156's typical operations include targeting South Asian governments with tools like CrimsonRAT and a Go-based backdoor called Wainscot, often used to steal sensitive information from defense and political entities. Secret Blizzard's intervention allowed them to manipulate this infrastructure, extracting Storm-0156's collected data and piggybacking on their operations to establish additional footholds.
By April 2023, Secret Blizzard moved further, infiltrating the workstations of Storm-0156 operators in Pakistan. This enabled them to seize credentials and additional malware, which they later redeployed in their campaigns.
Microsoft
Secret Blizzard's arsenal includes highly customized tools and innovative methods that blend seamlessly into the operations of their targets. Below is an overview of their espionage playbook:
- Hijacking Infrastructure: Secret Blizzard repurposes rival C2 servers to store and manage its malware deployments, disguising their activities as those of the original operators. Examples include the use of Storm-0156's CrimsonRAT backdoor and Microsoft-detected malicious payloads like TinyTurla and MiniPocket.
- Masquerading as Storm-0156: Secret Blizzard sideloads their malware, such as TwoDash, using techniques identical to Storm-0156, including DLL hijacking with tools like credwiz.exe.
- Strategic Deployment: In Afghanistan, Secret Blizzard actively deployed backdoors to critical government networks, maintaining long-term access. In India, their approach was subtler, with most activity limited to harvesting data exfiltrated by Storm-0156, suggesting that Secret Blizzard prioritized stealth over direct intrusion.
- Clipboard Monitoring: The Statuezy trojan monitors clipboard activity, capturing sensitive text like passwords or classified data for exfiltration.
Secret Blizzard's distinctive approach of “hacking the hackers” is both efficient and evasive, allowing the hackers to quickly establish footholds while masking their activities behind the operational noise of their victims.
An organization breached by one threat actor may unknowingly become a vector for additional attackers. For organizations in South Asia, particularly those in governmental and defense sectors, this campaign serves as a stark reminder of the sophistication of state-sponsored cyber threats and the importance of proactive cybersecurity measures.







Leave a Reply