
A newly disclosed cyberespionage operation linked to Russian intelligence has successfully circumvented multi-factor authentication (MFA) by manipulating targets into voluntarily creating and handing over app-specific passwords (ASPs).
The campaign targeted prominent critics of the Russian government, including British academic Keir Giles, highlighting an alarming evolution in social engineering techniques.
The attack was detailed in a joint report by Citizen Lab researchers John Scott-Railton, Rebekah Brown, and Bill Marczak, and corroborated by Google's Threat Intelligence Group (GTIG). GTIG tracks the threat actor as UNC6293, a state-sponsored group believed with low confidence to be linked to APT29, also known as “Cozy Bear,” a unit of Russia's Foreign Intelligence Service (SVR).
Anatomy of the MFA bypassing attack
On May 22, 2025, Giles, an expert on Russian disinformation and military operations, received an email from an individual posing as “Claudie S. Weber,” a purported U.S. State Department official. The attacker used a Gmail address while CC'ing several spoofed @state.gov email addresses to lend credibility. These addresses exploited a configuration of the State Department's email system that accepts messages to non-existent accounts without generating bounce-backs.
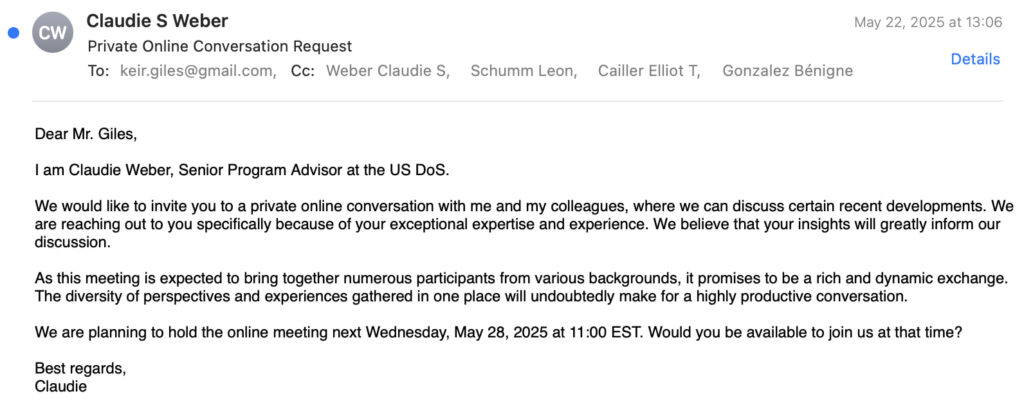
Citizen Lab
The message invited Giles to a fake consultation and ultimately prompted him to join a fabricated “MS DoS Guest Tenant” platform, allegedly for external collaborators. The attackers followed up with a well-crafted PDF masquerading as a secure government registration guide. This document instructed Giles to generate an ASP from Google's account settings page and share the code under the guise of setting up secure communications.

An App-Specific Password (ASP) is a randomly generated 16-character code that allows third-party apps to access a user's account when standard MFA mechanisms are incompatible. While these passwords are commonly used for legacy software, they bypass MFA entirely once created.
By reframing the ASP creation process as a routine registration for a secure U.S. government system, the attackers obtained full access to Giles' email accounts. The operation spanned several weeks and over ten email exchanges, demonstrating a patient and adaptive approach far from the usual hallmarks of mass phishing campaigns.
Google detected and neutralized the intrusion after observing suspicious activity. GTIG also found evidence of a broader campaign, with a second phishing operation using Ukrainian and Microsoft-themed ASP prompts. Both campaigns used the same infrastructure, including a specific residential proxy.
While the PDFs used in the attack contained no malware, the deception alone was enough to compromise accounts. The lures were linguistically polished and timed during U.S. business hours, likely with the assistance of large language models (LLMs), according to the researchers. The attackers also tailored their tactics in response to Giles' feedback, demonstrating a level of agility and domain knowledge not typically seen in opportunistic phishing efforts.
To defend against similar threats, high-risk users like journalists, researchers, and dissidents should enroll in Google's Advanced Protection Program (APP), which disables ASP creation entirely. Organizations should audit ASP usage and disable them where unnecessary.






Leave a Reply