
Sandworm, an infamous Russian state actor, has been leveraging pseudo-hacktivist accounts on Telegram to claim responsibility for cyber-attacks against American critical infrastructure.
This marks a significant evolution in cyber warfare tactics, blending traditional state-sponsored activities with the guises of grassroots hacktivism to obfuscate the direct involvement of the Russian intelligence services.
Sandworm, whom Mandiant (Google) now designates as APT44, has been active for over a decade and is directly linked to the Main Intelligence Directorate of the Russian General Staff (GRU).
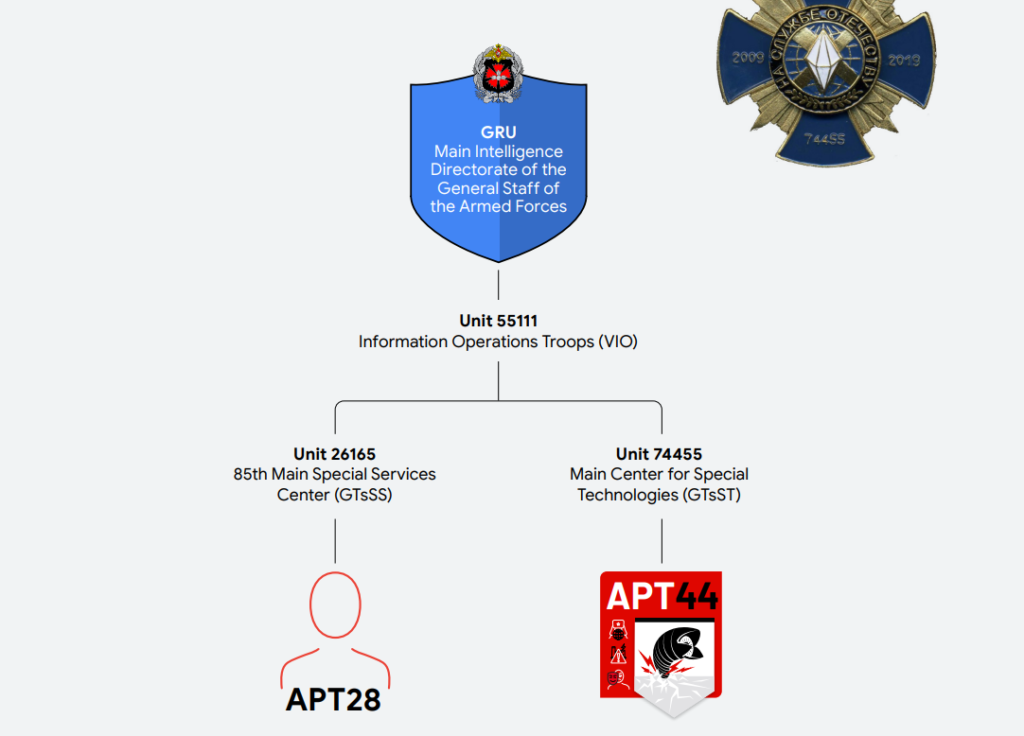
Mandiant
The group is notorious for its aggressive cyber operations globally, often targeting governments and critical infrastructure to advance Moscow's geopolitical interests. Their operations range from disruptive cyberattacks to espionage and influence operations, showcasing a sophisticated command over various cyber warfare tactics.
Boosting impact of operations on Telegram
The use of Telegram by Sandworm to announce breaches and manipulate public perception illustrates a strategic pivot towards information warfare. This platform serves as a perfect stage due to its encrypted nature and popularity among activist groups.
Sandworm uses this to their advantage, creating pseudo-hacktivist personas that claim cyber-attacks, which are, in reality, orchestrated by this state-backed entity.
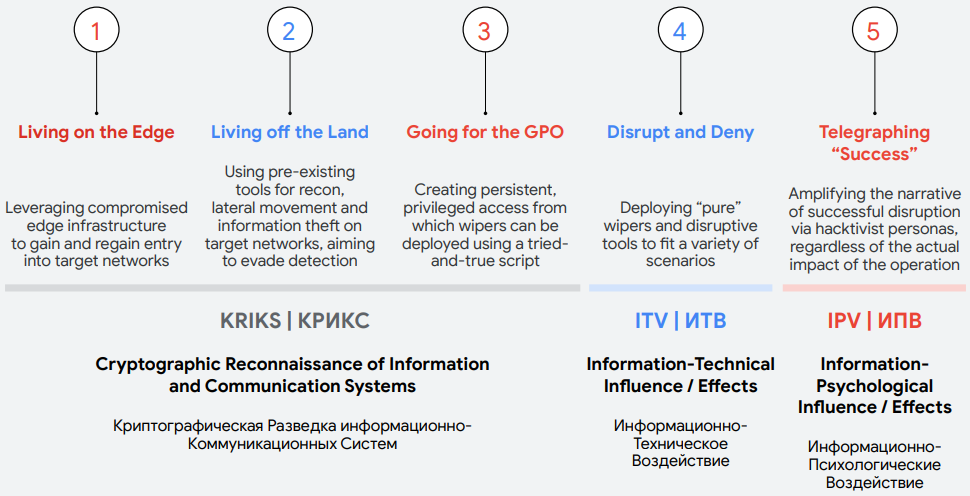
Mandiant
Notably, personas like CyberArmyofRussia_Reborn have been actively used to disseminate misinformation and claim responsibility for attacks, thereby muddling the waters of attribution and enhancing the psychological impact of their operations.
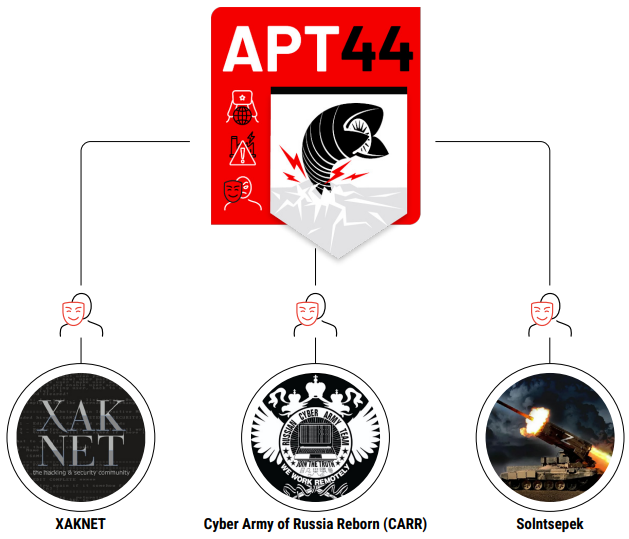
Mandiant
Sandworm has been particularly active in targeting American utilities, including a documented incident where they manipulated interfaces of operational technology assets at water utilities in the US. This operation was first broadcasted through one of their managed Telegram channels, which later correlated with real-world disruptions in these facilities.
Between 17 and 18 January 2024, the group's Telegram channel posted videos taking credit for the manipulation of human machine interfaces (HMI) controlling operational technology (OT) assets at Polish and U.S. water utilities.
On 02 March 2024, the group posted an additional video claiming to disrupt electricity generation at a French hydroelectric facility by manipulating water levels.
Each of the videos posted by CyberArmyofRussia_Reborn appear to show an actor haphazardly interacting with interfaces controlling the respective water or hydroelectric facilities' OT assets.
Mandiant
The audacity of such claims and the subsequent confirmation of disruptions highlight the severe implications of Sandworm's continued cyber operations, which now impact the Western world on a new level.
Organizations, especially those within critical infrastructure sectors, should heighten their vigilance and enhance their cybersecurity measures against sophisticated state actors. Implementing robust network monitoring, incident response plans, and user education on phishing and other social engineering tactics are crucial.
As the landscape of cyber warfare evolves, the blend of traditional espionage with modern information warfare tactics by groups like Sandworm demands a proactive and dynamic approach to cybersecurity.







Leave a Reply