
Security researchers at ESET have disclosed an actively exploited zero-day vulnerability in WinRAR (CVE-2025-8088), abused in targeted spear-phishing campaigns by the Russia-aligned threat group RomCom.
The flaw, a path traversal issue involving alternate data streams (ADSes), allowed attackers to hide and deploy malicious files outside the intended extraction directory. A patched version, WinRAR 7.13, was released on July 30, 2025, just twelve days after ESET privately notified the developer.
According to ESET’s report, the vulnerability was discovered on July 18, 2025, during analysis of a suspicious RAR archive posing as a job application. The file, Eli_Rosenfeld_CV2 – Copy (10).rar, appeared benign but contained hidden ADS-based payloads. When extracted or opened directly in WinRAR 7.12 or earlier, these streams deployed malicious DLL and LNK files to sensitive locations such as %TEMP% and the Windows Startup folder, enabling persistence on the victim’s system.
The campaign targeted financial, manufacturing, defense, and logistics firms in Europe and Canada. While ESET telemetry indicates that no recipients were successfully compromised, analysis revealed three distinct malware delivery chains:
- Mythic agent – A COM hijacking technique using msedge.dll, with AES-decrypted shellcode contacting srlaptop[.]com.
- SnipBot variant – A trojanized PuTTY CAC executable (ApbxHelper.exe) that checks for at least 69 recently opened documents before proceeding, fetching further payloads from campanole[.]com.
- MeltingClaw – A Rust-based downloader (Complaint.exe), linked to gohazeldale[.]com.
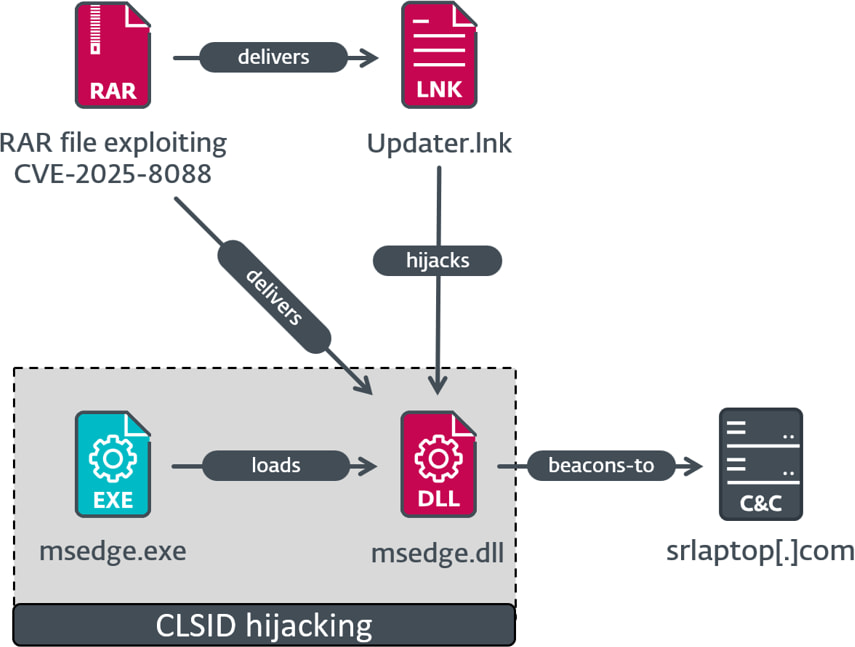
ESET
RomCom, also known as Storm-0978, Tropical Scorpius, or UNC2596, has a documented history of exploiting high-value zero-days, including CVE-2023-36884 in Microsoft Word and a 2024 Firefox vulnerability chain. Its operations blend financially motivated intrusions with espionage aligned to Russian geopolitical interests.
Russian cybersecurity firm BI.ZONE separately observed similar exploitation by a different cluster known as Paper Werewolf (aka GOFFEE), which used the same ADS-based directory traversal method against Russian targets. Paper Werewolf’s campaigns, alongside earlier use of CVE-2025-6218, delivered custom .NET downloaders that fetched additional payloads from domains such as indoorvisions[.]org and trailtastic[.]org.
Users are recommended to update to WinRAR 7.13 or later immediately and disable the opening of archives directly from email clients, as that could lead to malicious code execution without user interaction.
While Windows 11 now includes native RAR extraction support thanks to Microsoft’s integration of the open-source libarchive library, this feature is relatively recent, limited to unpacking only, and absent from older Windows versions still widely deployed in enterprise environments. Many organizations continue to rely on WinRAR for creating RAR archives, handling password-protected files, and accessing advanced features like recovery records, making vulnerabilities such as CVE-2025-8088 valuable targets for hackers.







Leave a Reply