
Over the past 48 hours, we have been watching the news about the RockYou2021 “Password Leak” blowing up in the media. Unfortunately, there are many misconceptions about this so-called “leak” floating around, so let's take a closer look and examine the facts.
But before we dive in, let's cover a quick background of the story.
What started this news frenzy was this post on a hacking forum claiming to offer billions of passwords:
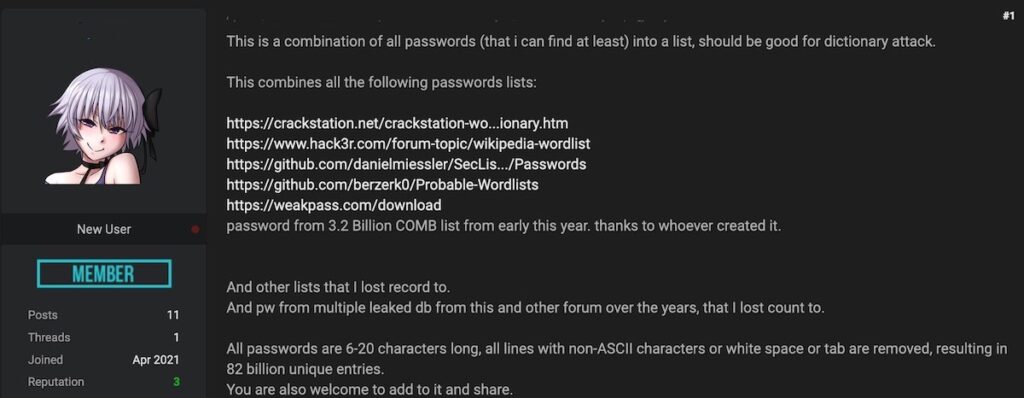
As you can see in the screenshot above, the user is offering a combination of existing lists, as well as data from “other lists” that are not specified.
Following this post, news outlets began trumpeting stories about 8 billion passwords being leaked online, or “the mother of all password leaks, with billions of credentials exposed” according to Yahoo and others.
But is this really the case?
Answer: No. Here are the facts.
A giant list of words – NOT new passwords
As you can see in the original forum post above, the user was simply posting existing lists from various sources. In other words, these are not new, real-world passwords, but instead mostly wordlists from sources like Wikipedia.
To see this, we only need to look at the sources that the user included in the list:
- The Crackstation.net Dictionary – This contains every wordlist, dictionary, and existing password leak data, as well as every word in Wikipedia and words from Project Gutenberg. In short, this is a giant list of words, with a few old passwords mixed in.
- The Hack3r Wikipedia Wordlist – Again, just another giant wordlist from Wikipedia.
- Daniel Meissler's SecLists on Github – This includes common credentials, words, permutations, default credentials, as well as some existing credentials from leaks and honeypots.
- Berzerk0's Probable Wordlists on Github – This includes existing passwords and dictionaries.
- The Weakpass list – Another compilation of wordlists and existing passwords.
- Data from COMB – This is the Combination of Many Breaches, which is another combination list that includes some existing passwords.
As you can see, there is no new data here and no new credentials being exposed or “leaked” to the public. This is merely a list that combines existing lists. And what's more, it is composed mostly of wordlists.
Nothing new or unique
As you have probably gleaned by looking at the actual sources of this so-called leak, there is actually nothing new or unique being offered here. So why is anyone sounding the alarm, and how did this become news?
Even calling this “RockYou2021” is a stretch, because there is no new information, unlike the original Rock You leak in 2009. Troy Hunt, the security expert behind the Have I Been Pwned project, took to Twitter to put this so-called “password leak” into context. He also explained why he will not be adding any of the data to his own lists:
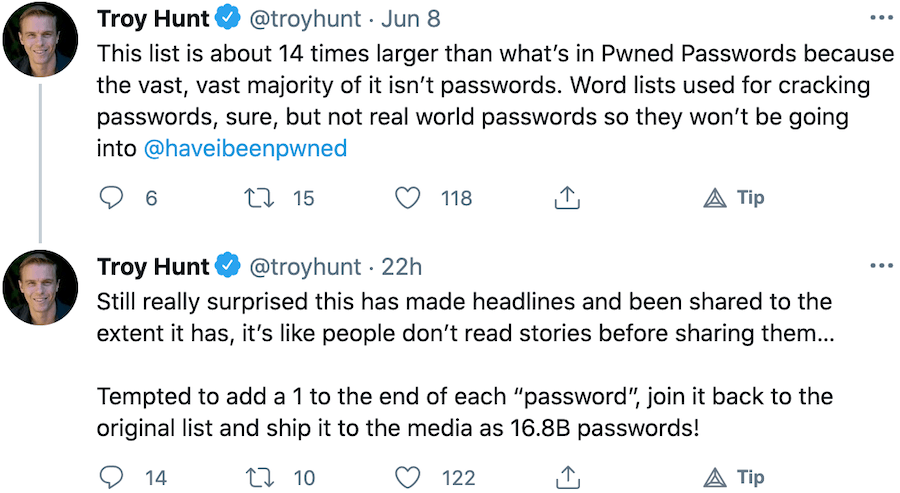
This leads us to our next question.
Is the data even useful?
If you were a threat actor looking for an actual list of passwords to exploit, then no, this \”leak\” would not be very useful.
However, this list could be useful for a dictionary attack, simply because it compiles a giant list of words. And this is exactly what the user on the hacker forum posted in his opening sentence: “should be good for a dictionary attack.” (For those wondering, a dictionary attack is simply using words from a dictionary as potential passwords when trying to gain access to an account.)
So if this leak is mostly a giant list of words, and does not contain any new compromised passwords, then how did this story explode? Why do we find Yahoo telling people, “If you’re reading these words, suffice it to say you probably need to change your passwords.”
You should already be using strong, unique passwords
For years we've been discussing the importance of using strong, unique passwords. We have a basic guide on how to create strong passwords, which is a good refresher. And of course you should not be recycling passwords for different websites and accounts. This could give someone access to everything you secure with the common password (if it were to be compromised somehow).
And if you find the thought of managing lots of complex passwords daunting, there are some great tools for that, too. Enter the password manager. A good password manager will not only store all your passwords in a secure location, but it can also help you generate secure passwords.
For example, we'll look at Bitwarden, which is a free and open source password manager. With it, you can generate complex, unique, and secure passwords with the click of a button, as you can see here:
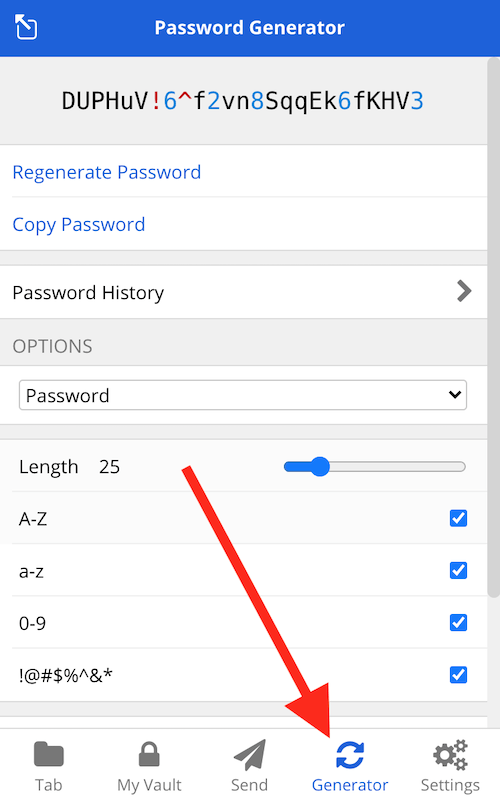
And for more info on this topic, check our guide on password managers here.
Lastly, if you are concerned about your passwords being exposed or leaked, you can always check out the Have I Been Pwned passwords page to see.







Leave a Reply