
The latest version of Rhadamanthys Stealer, v0.7.0, has introduced an AI-powered optical character recognition (OCR) feature to extract cryptocurrency wallet seed phrases from images.
Active since 2022, Rhadamanthys has had at least ten iterations and is evolving rapidly to bypass security measures. It poses a global threat, primarily targeting the United States, with a developer known as “kingcrete2022” who uses underground channels to distribute and advertise the malware.
Recorded Future
Highlights of the latest Rhadamanthys version
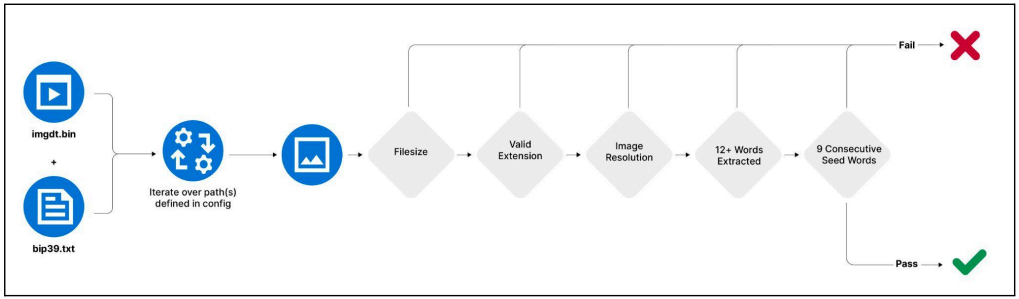
The most notable innovation in v0.7.0, according to a report by Recorded Future, is the AI-based OCR feature. It enables Rhadamanthys to search for and extract seed phrases from images on infected devices. These seed phrases are critical for cryptocurrency access and security, making them a valuable target for cybercriminals.
The malware uses both client- and server-side components to identify potential seed phrase-containing images on a client and then extracts the seed phrase once the image is exfiltrated to the command-and-control (C2) server. This feature significantly expands the data that Rhadamanthys can compromise, moving beyond traditional text-based information theft to image-based data as well.
Additionally, the stealer has included the ability to execute Microsoft Software Installer (MSI) files, which are typically seen as legitimate software packages and may evade standard security detections. This tactic allows the malware to embed malicious payloads within seemingly innocuous MSI files, increasing its chances of bypassing security tools.
Recorded Future
Threat actor profile
“kingcrete2022,” the developer behind Rhadamanthys, was banned from popular underground forums like XSS and Exploit for targeting Russian or former USSR entities. However, the actor remains active through private channels on TOX, Telegram, and Jabber to advertise the malware to prospective clients. The fee structure for Rhadamanthys makes it an affordable choice for cybercriminals, with costs starting at $250 for 30-day access and $550 for a 90-day license.
The malware is distributed through various means, including phishing campaigns, loaders masquerading as legitimate software, and other social engineering techniques. One prominent attack in October 2023 involved Rhadamanthys being deployed via MSIX installers impersonating software like Google Chrome and Webex. In another case in February 2024, a phishing campaign targeted the oil and gas sector with emails pretending to be from the Federal Bureau of Transportation, which contained malicious ZIP files leading to infection.
Technical profile and evolution
Rhadamanthys Stealer is designed to exfiltrate a broad range of data, including system information, credentials, browser data, and cryptocurrency wallets. The malware employs a range of anti-analysis and anti-detection techniques, such as:
- Anti-behavioral analysis: Includes timing checks, memory-write monitoring, and sandbox evasion tactics.
- Anti-static analysis: Uses code obfuscation and complex encoding to evade static analysis tools.
- Defense evasion: Encrypts and encodes its payload, uses legitimate Windows function calls, and alters file permissions.
- Execution and C2 communication: Leverages command or scripting interpreters like PowerShell for execution and uses HTTP/HTTPS protocols for C2 communication.
Recorded Future
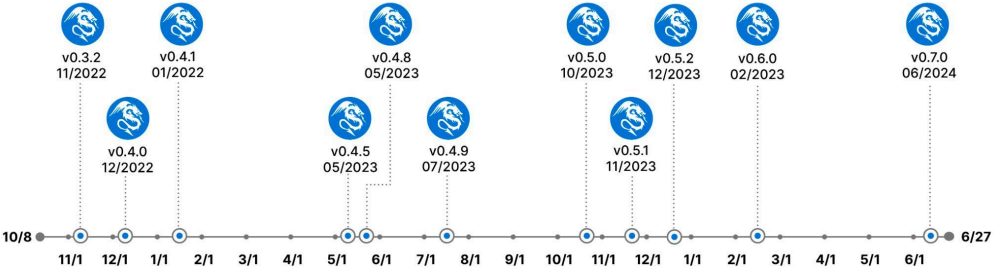
The constant updates and new features of Rhadamanthys are highlighted in its changelog, with v0.7.0 being the most significant so far, introducing rewritten frameworks for both client and server operations, AI-powered recognition for seed phrases, improved execution stability, and enhanced encryption and hashing for tamper-proof protection against re-execution within a configurable timeframe.
It's important to note that the use of OCR for password theft isn't new, and we recently reported about an Android malware named ‘SpyAgent' following a similar tactic to extract long seed phrases. However, the adoption of OCR by more malware, including highly popular projects like Rhadamanthys, creates an ever-increasing risk for users.







Leave a Reply