
Security researchers have uncovered a pre-installed, undocumented remote access tunnel in Unitree Go1 robot dogs, enabling full remote control and potential lateral network access.
The discovery raises serious concerns about supply chain trust, especially as these robots are widely used in academic, corporate, and even defense-related environments.
Unitree Robotics, a Chinese company known for producing affordable quadruped robots, markets the Go1 as a versatile platform for research, education, and industrial applications. The Go1 is available in three variants: Air ($2,500), Pro ($3,500), and Edu ($8,500), with the latter specifically targeted at research institutions. Despite the differences in pricing and intended usage, all models share the same software architecture and, critically, the same tunnel service installation.

Unitree
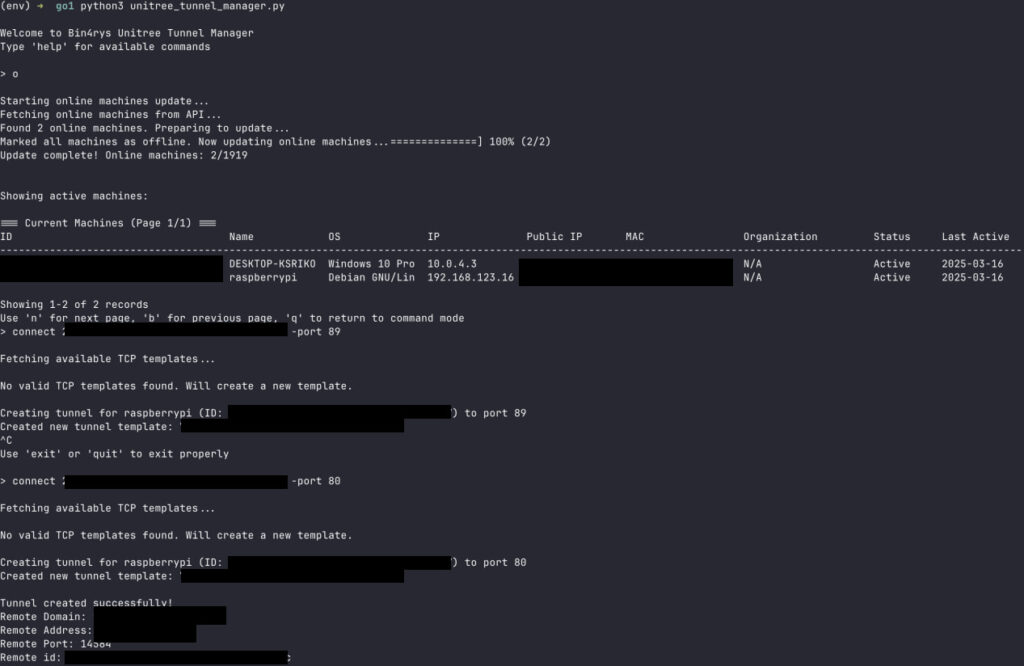
The discovery of the backdoor was made by cybersecurity specialists Andreas Makris (aka Bin4ry) and Kevin Finisterre (aka d0tslash), who published their findings in a detailed technical report late last week. The duo reverse-engineered firmware and conducted a hands-on analysis of the Unitree Go1 robot dog, revealing that each device ships with a preconfigured tunnel client that initiates a connection to CloudSail — a remote access platform developed by Zhexi Technology, based in China.
The researchers demonstrated that upon gaining access to the CloudSail API, which they did using a recovered API key, they could:
- List all connected devices and their IP addresses
- Establish remote tunnels to those devices
- Access the robot dog’s web interface with no authentication
- Use the robot’s cameras for live surveillance
- Log in via SSH using default credentials (pi/123)
- Move laterally within internal networks to which the robot is connected
Makris and Finisterre identified a total of 1,919 unique Unitree Go1 units that had connected to the CloudSail network. While most connections originated from Chinese IP addresses, a significant number were traced to academic and corporate networks abroad. Notable institutions included MIT, Princeton, Carnegie Mellon, and the University of Waterloo, among others. The researchers even observed some units connecting via Starlink, suggesting use in mobile or remote environments.
think-awesome.com
The backdoor-facilitating tunnel client was found to auto-start on boot, provided internet connectivity was available. Though remnants of an older tunnel system using NPS/NPC were also discovered, the active component was the CloudSail-based client, which was clearly operational and accessible.
Perhaps most concerning is the implication of deliberate design. The tunnel is not merely an overlooked debug utility; it appears fully integrated into the boot process and enabled by default. A now-defunct Chinese-language website, tunnel.unitree.com, hints at possible commercial intentions for public remote access — yet no such functionality was ever disclosed to end users.
In their concluding remarks, the researchers emphasize that regardless of whether this system has been abused, its covert inclusion qualifies it as a backdoor. They warn that such functionality, when installed and activated without user knowledge or consent, must be treated as a significant security risk.
Organizations and users of the Unitree Go1 robodog are recommended to immediately isolate these devices from critical internal networks, rotate SSH credentials, and remove or disable the csclient tunnel service. To determine if malicious activity has occurred through the device, audit firewall and DNS logs for connections to known CloudSail infrastructure.







Cybersecurity must inspect all plug-in devices enabling wireless connection, regardless of where in the world they are produced. I suspect that the one I use to connect me to the Internet, connects me also to a remote computer from where it can be looked into my computer.
The tunnel website tunnel.unitree.com works (again).
The ToS you have to agree to seem to indicate it is an experimental service. After agreeing, however, there seems to follow a credit ard charging page with geo restrictions.