
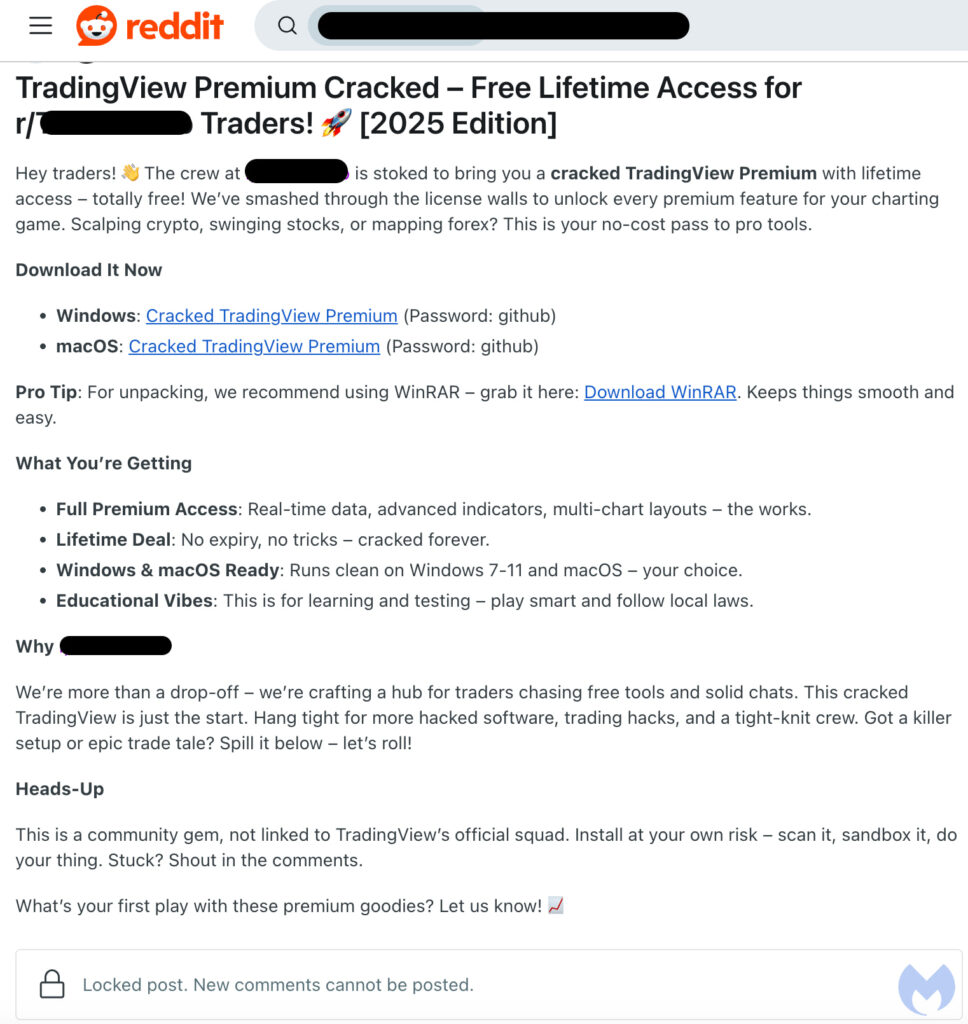
Cybercriminals are distributing AMOS and Lumma Stealer malware to Windows and macOS users via Reddit posts, luring cryptocurrency traders with promises of cracked versions of TradingView.
The malware-laced downloads have already resulted in stolen credentials and drained crypto wallets.
TradingView-themed attacks
According to a Malwarebytes report, attackers post on cryptocurrency-related subreddits, offering what they claim to be a fully unlocked version of TradingView, a widely used charting and analytics platform for financial markets. The posts include download links to both Windows and macOS versions of the software, but these files have been compromised with information-stealing malware.
Malwarebytes
Unlike typical phishing campaigns, the scammers behind this operation are actively engaging with Reddit users, responding to questions, and attempting to reassure skeptical downloaders. In some cases, they downplay security concerns, with one scammer even joking that “a real virus on a Mac would be wild.”
The malware files are hosted on a website belonging to a Dubai-based cleaning company, rather than a more conventional file-sharing service like Mega. This unusual hosting choice suggests the attackers have direct control over the server, allowing them to update and modify the payloads as needed.
Notably, the compromised site exposes its PHP version (7.3.33), which reached its end of life in December 2021. This outdated software is vulnerable to exploits, making it an easy target for attackers.
Both the Windows and Mac versions of the malware are delivered in a double-zipped format, with the final archive being password-protected — an evasion tactic commonly used to bypass security scans.
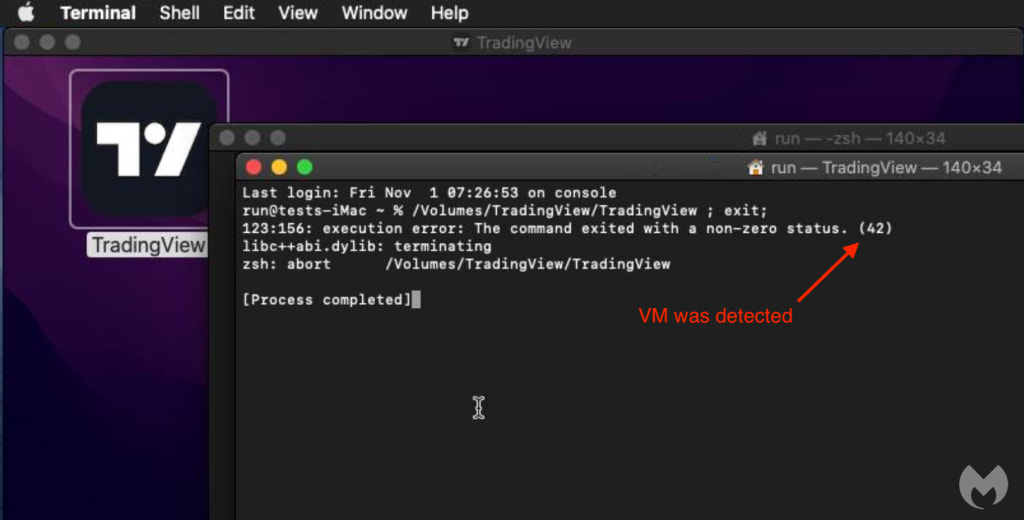
On macOS, the installer is a new variant of AMOS (Atomic Stealer), a well-known macOS infostealer. This version includes an anti-analysis feature that checks for the presence of virtual machines and halts execution if one is detected. If the malware runs successfully, it exfiltrates user data via a POST request to 45.140.13.244, a server located in the Seychelles.
Malwarebytes
On Windows, the infection begins with an obfuscated BAT file (Costs.tiff.bat), which executes a malicious AutoIt script (Sad.com). The script links together multiple file fragments before executing its payload. The Windows variant communicates with a command-and-control (C2) server at cousidporke[.]icu, a domain registered just a week ago by an individual in Russia.
Victims who have unknowingly installed the malware have reported stolen cryptocurrency wallets and subsequent impersonation attempts by attackers, who use the compromised accounts to spread further phishing links.
Protection advice
As cracked software continues to serve as a major malware distribution vector, users should remain highly cautious of free software offers, especially those promoted in online forums. To stay safe, never disable your security software when installing programs, even if an installer suggests it. Be wary of password-protected files, as this is a common trick to evade antivirus detection. Ultimately, avoid downloading files from unknown or suspicious websites, especially when they are unrelated to the software being offered.







Umm. Ok. Serves Reddit users right. Just Google PayPal mafia and Dark Maga….