
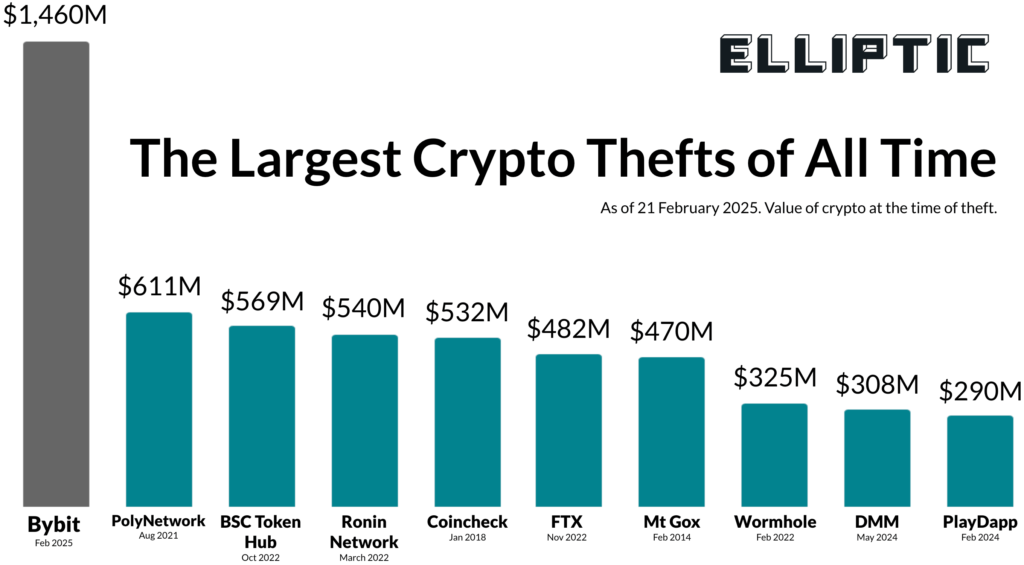
The cryptocurrency industry has been rocked by the largest digital asset theft in history, as hackers stole approximately $1.5 billion from Bybit, a Dubai-based crypto exchange.
Initial investigations suggest the attackers manipulated a multisig cold wallet by deceiving signers through a compromised user interface (UI), marking a significant evolution in attack tactics. Cybersecurity firms, including Check Point Research, Elliptic, and TRM Labs, have attributed the attack to North Korea’s Lazarus Group, which has a long history of targeting the crypto sector.
Bybit is one of the largest cryptocurrency exchanges globally, with millions of users and billions of dollars in daily trading volume. Founded in 2018 and headquartered in Dubai, it has positioned itself as a key player in the crypto derivatives market. The exchange offers a mix of spot and futures trading and has recently expanded its services to include staking and decentralized finance (DeFi) integrations. The sheer scale of this hack underscores the vulnerability of even the most well-established platforms, raising serious concerns about the security of institutional crypto holdings.
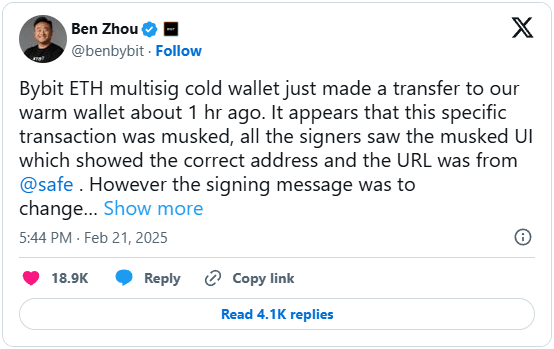
The breach was first detected on February 21, 2025, when multiple blockchain monitoring systems flagged an anomaly in Bybit’s cold wallet transactions. The attackers leveraged an advanced social engineering scheme that tricked signers into unknowingly approving a transaction that altered the wallet’s smart contract logic. Instead of exploiting a flaw in Bybit’s underlying smart contract code, the hackers manipulated the UI display, ensuring that the signers saw a legitimate transaction request while actually authorizing a hostile takeover of the cold wallet.
Bybit’s CEO, Ben Zhou, confirmed on X that the attack affected only one of the exchange’s Ethereum cold wallets. He described the incident as a “masked UI” attack, meaning the displayed transaction details were falsified to mislead the signers. Once the hackers gained control, they swiftly transferred the assets to an unknown address. Despite the severity of the breach, Zhou reassured users that all withdrawals remained operational and that Bybit had sufficient reserves to cover the losses.
Hallmark Lazarus laundering
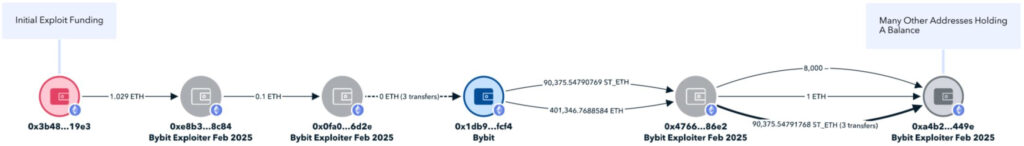
Blockchain analytics firms Elliptic and TRM Labs have both linked the Bybit hack to North Korea’s Lazarus Group. Elliptic’s forensic analysis found that the laundering techniques used to move the stolen funds matched previous Lazarus Group operations. The attackers quickly converted stolen Ethereum-based tokens into native Ether (ETH) through decentralized exchanges (DEXs), preventing issuers from freezing the assets. Within two hours, the stolen assets were split across 50 wallets, each holding roughly 10,000 ETH, a strategy designed to complicate tracking efforts.
Elliptic
TRM Labs corroborated these findings, stating with “high confidence” that the attack was conducted by North Korean hackers. Their assessment was based on blockchain address overlaps with previous Lazarus-linked incidents. Notably, this single attack nearly doubled North Korea’s total crypto theft from 2024, when they stole approximately $800 million. These illicit funds are believed to be funneled into North Korea’s ballistic missile program, making the Bybit hack not just a financial crime but also a geopolitical concern.
Cold wallet security challenged
The Bybit hack challenges long-held assumptions about the security of cold wallets and multisignature (multisig) protections. Traditionally, these measures were considered among the safest ways to store digital assets. However, this attack demonstrates that:
- Multisigs are not foolproof – If signers can be deceived, multisig wallets can still be compromised.
- Cold wallets aren’t inherently safe – Even offline storage solutions can be hacked if UI deception or insider threats are involved.
- Supply chain and UI manipulation attacks are becoming more sophisticated – Attackers are no longer relying solely on protocol vulnerabilities but are targeting human operators with advanced social engineering tactics.
The Bybit hack is a wake-up call for the entire crypto industry. Even with robust cryptographic defenses, human error and social engineering remain the most significant security risks.







Leave a Reply