
Microsoft researchers have uncovered a significant vulnerability in VMware ESXi hypervisors, exploited by ransomware operators to gain full administrative permissions on domain-joined systems. The vulnerability, CVE-2024-37085, allows threat actors to encrypt entire file systems and access hosted virtual machines, potentially leading to severe disruptions.
The discovery was made by the Microsoft Threat Intelligence team and disclosed to VMware through Coordinated Vulnerability Disclosure (CVD). VMware has since released a security update to address this issue, with Microsoft urging administrators to apply these updates immediately.
Vulnerability details
ESXi is a widely used bare-metal hypervisor installed directly on physical servers, providing control over the underlying resources. The identified vulnerability involves a domain group, “ESX Admins,” which, when created, is granted full administrative access to ESXi hypervisors without proper validation. This flaw allows ransomware operators to elevate their privileges on the hypervisors, enabling them to encrypt file systems and disrupt the functionality of hosted servers.
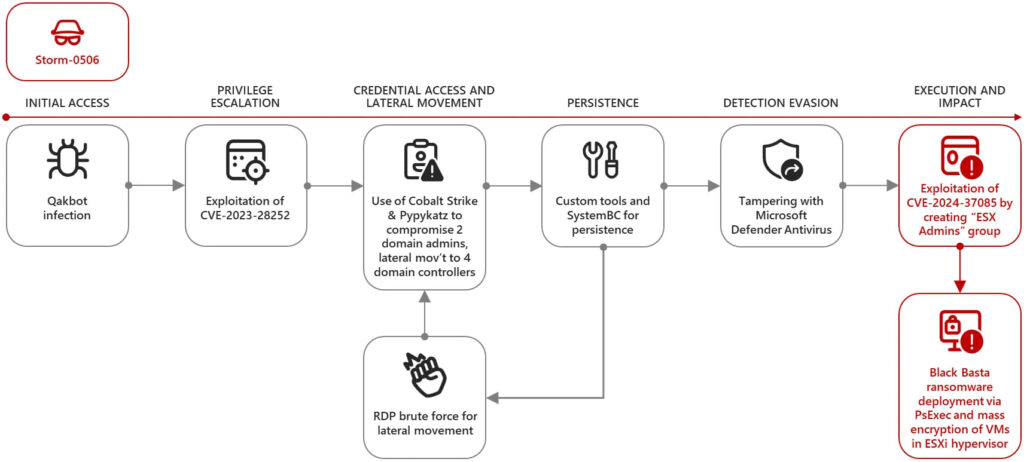
Microsoft's analysis revealed that ransomware groups, including Storm-0506, Storm-1175, Octo Tempest, and Manatee Tempest, have utilized this vulnerability. These groups have deployed ransomware, such as Akira and Black Basta, by exploiting CVE-2024-37085. The method involves creating the “ESX Admins” group in the domain and adding a user to it, thereby gaining full administrative access.
Three exploitation methods:
- Creating the “ESX Admins” group: A domain user with group creation rights can create the group and add themselves or others to gain administrative privileges.
- Renaming an existing group: Renaming any domain group to “ESX Admins” and adding a user to it, though not observed in the wild by Microsoft.
- Privileges refresh: Even if the administrator changes the management group, the full privileges of “ESX Admins” are not immediately revoked, allowing exploitation.
Microsoft
The impact of this vulnerability is profound. Ransomware operators can encrypt the ESXi hypervisor's file system, affecting the operation of hosted virtual machines. Additionally, they can exfiltrate data or move laterally within the network. In a notable attack earlier this year, Storm-0506 deployed Black Basta ransomware against a North American engineering firm, utilizing CVE-2024-37085 to escalate privileges and encrypt systems, disrupting the firm's operations.
Microsoft
VMware's response
VMware has released security patches to mitigate this vulnerability, so users are recommended to ensure all domain-joined ESXi hypervisors have the latest patches.
Microsoft has also provided detailed mitigation strategies, urging administrators to:
- Validate the “ESX Admins” group existence and harden its settings.
- Deny access for this group in ESXi settings if not required.
- Change the administrative group in ESXi hypervisors.
- Add custom detections for new group names in security monitoring tools.
- Monitor ESXi logs for suspicious activities.







Leave a Reply