
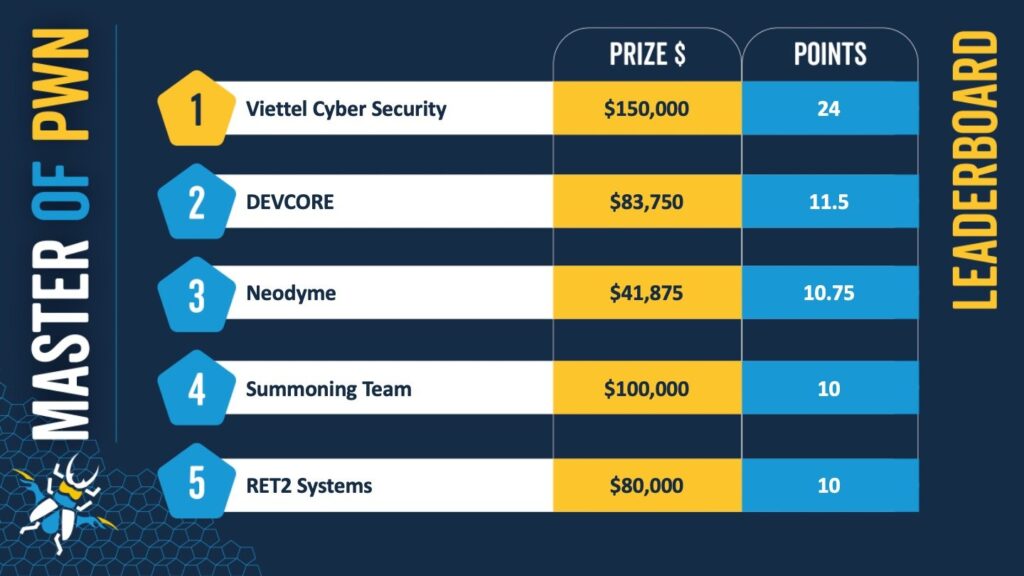
Day two of Pwn2Own Ireland 2024 concluded with $358,625 awarded to security researchers for their successful exploitation of over 15 devices, bringing the event total to $847,875. The Viettel Cyber Security team continues to lead the “Master of Pwn” standings, but several other teams had notable wins across a variety of smart devices and enterprise tech.
Viettel Cyber Security remains a strong contender, with team member dungdm successfully exploiting the Sonos Era 300 smart speaker using a use-after-free (UAF) vulnerability. This effort earned him $30,000 and six “Master of Pwn” points. The team also managed to exploit the HP Color LaserJet Pro printer through a type confusion bug, adding $10,000 to their winnings.
Another major success came from Ken Gannon of NCC Group, who used five distinct vulnerabilities, including a path traversal bug, to compromise the Samsung Galaxy S24, gaining a shell and installing an app. His exploit earned him $50,000 and five points, securing one of the day’s largest single payouts.
In addition to Viettel Cyber Security and NCC Group, several other teams made significant progress. Chris Anastasio and Fabius Watson of Team Cluck demonstrated expertise by chaining two bugs, including a CRLF injection, to exploit the QNAP TS-464 NAS (Network Attached Storage), netting them $20,000. InfoSect also scored a win with a heap-based buffer overflow exploit on the Sonos Era 300, earning $30,000.
Zero Day Initiative
However, not all attempts were successful. Teams such as Rapid7 and DEVCORE encountered difficulties, with some unable to complete their exploits in time. Neodyme had a partial success during a “SOHO Smashup” challenge, utilizing four bugs on a smart home hub but facing a collision where one vulnerability had already been used by another team earlier in the competition. Despite this, they still managed to secure $21,875 for their efforts.
The Pwn2Own competition, hosted by Trend Micro’s Zero Day Initiative, is known for its challenging environment where participants attempt to uncover and exploit zero-day vulnerabilities in widely used consumer and enterprise devices. With a growing focus on smart home technologies, including printers, NAS devices, and cameras, the competition highlights the importance of security in everyday devices.
With two days remaining, teams are still vying for the prestigious title of “Master of Pwn.” Though Viettel Cyber Security holds the lead, the competition remains tight, with teams like NCC Group and InfoSect making strong showings. The final days will likely feature even more high-stakes exploits as researchers aim for both financial rewards and technical prestige.







Leave a Reply