
Pwn2Own Berlin 2025 has concluded with a record-breaking total payout of $1,078,750, recognizing 28 previously unknown zero-day vulnerabilities across a broad range of systems.
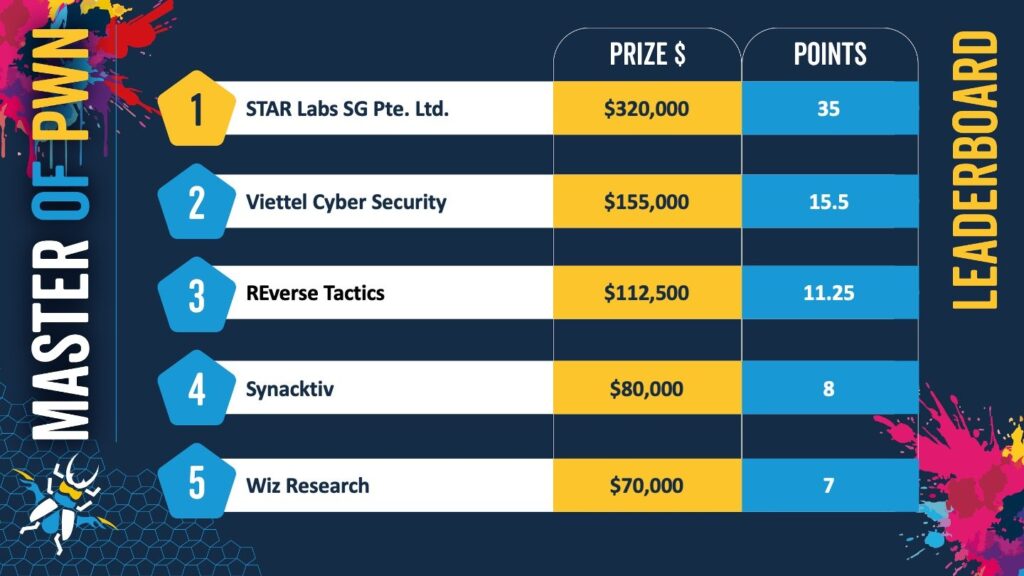
On the final day alone, researchers earned $383,750, pushing the contest past the $1 million milestone. STAR Labs SG emerged as the event's top team, earning the coveted Master of Pwn title after securing $320,000 and 35 points over the three-day competition.
ZDI
Pwn2Own, organized annually by ZDI, is a premier exploit competition that rewards researchers for disclosing zero-day vulnerabilities directly to vendors. Participants are paid for successful demonstrations, while vendors receive detailed technical information privately to allow time for patching before public disclosure.
The event, hosted by Trend Micro's Zero Day Initiative (ZDI) in partnership with OffensiveCon, saw global security teams demonstrating cutting-edge exploitation techniques across Windows, virtualization platforms, web browsers, and for the first time, AI systems. Seven of the 28 total zero-days targeted artificial intelligence infrastructure, highlighting a rising threat vector in modern computing environments.
Highlights of Day 3
Several standout entries defined Day Three, with successful exploits landing in categories that had proven resistant in prior rounds. Among them was a privilege escalation on Windows 11 by Miloš Ivanović, who leveraged a race condition bug to achieve SYSTEM-level access, earning $15,000 and 3 points.
Manfred Paul, a veteran Pwn2Own winner, returned to form by exploiting Mozilla Firefox using an integer overflow in the renderer process, securing $50,000 and 5 points. The entry underscores the persistent risk of memory management flaws in client-side software, even in hardened applications.
In the AI category, Wiz Research's Nir Ohfeld and Shir Tamari exploited the NVIDIA Container Toolkit by abusing an external initialization of trusted variables flaw, a novel attack path that earned them $30,000 and 3 points.
Corentin Bayet of Reverse Tactics achieved the day's highest single payout by combining two vulnerabilities — one of which was a unique integer overflow — to exploit VMware ESXi. Despite a collision on the second bug, the originality of his primary exploit secured $112,500 and 11.5 points.

Virtualization platforms remained a popular and lucrative target. Synacktiv's Thomas Bouzerar and Etienne Helluy-Lafont demonstrated a heap-based buffer overflow in VMware Workstation, earning $80,000 and 8 points. Meanwhile, STAR Labs' Dung and Nguyen chained a TOCTOU race condition to escape a virtual machine and an array index validation flaw to escalate privileges on Windows, netting $70,000 and 9 points.
The final day wasn't without setbacks. STAR Labs, despite their overall victory, failed to land a working exploit against NVIDIA's Triton Inference Server within the allocated time. And several otherwise successful attempts were affected by “collisions” — cases where the submitted vulnerabilities had already been reported to vendors, disqualifying them from full rewards. Notable among these was DEVCORE's Angelboy, who exploited Windows 11 for local privilege escalation but was credited only $11,250 due to overlap with known issues.
Pwn2Own Berlin 2025 marked the first European edition of the contest and the first to introduce a dedicated AI category, reflecting how security risks are expanding into machine learning systems and infrastructure. Vendors represented in this edition included Microsoft, NVIDIA, Mozilla, VMware, and Oracle, among others. Check here for Day 1, and here for Day 2 pwns.







Leave a Reply