
The first day of the inaugural Pwn2Own Berlin wrapped with $260,000 awarded to security researchers for successful zero-day exploits across Linux, Windows, virtualization software, and — for the first time in Pwn2Own history — AI systems.
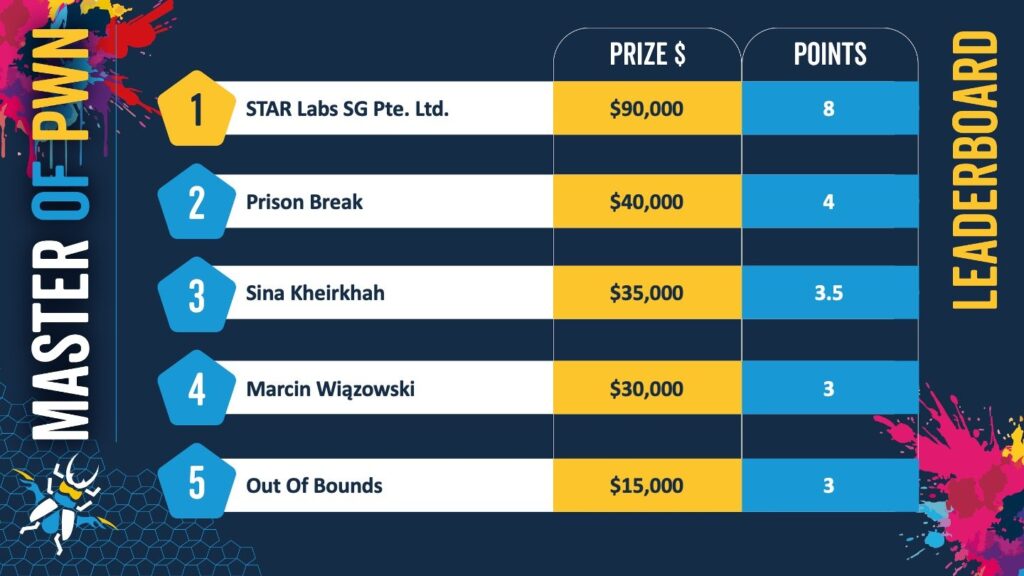
STAR Labs has taken an early lead in the “Master of Pwn” leaderboard, but several competitors remain in close contention.
Pwn2Own, operated by Trend Micro's Zero Day Initiative (ZDI), is a well-known exploit contest where researchers demonstrate previously unknown vulnerabilities against major software platforms. Vendors are notified of bugs privately, allowing them to patch before public disclosure. This year's Berlin edition features categories spanning local privilege escalation, virtualization, servers, and now AI, reflecting the growing attack surface in machine learning infrastructure.
Earlier today, researchers from top security teams around the globe executed 11 exploit attempts, with several earning high payouts for innovative attacks.
Among the standout entries was Pumpkin (@u1f383) from the DEVCORE Research Team, who exploited an integer overflow to achieve local privilege escalation on Red Hat Enterprise Linux. The successful demonstration earned $20,000 and two points toward the Master of Pwn title.
Chen Le Qi (@cplearns2h4ck) from STARLabs SG followed with a sophisticated Windows 11 exploit, combining a use-after-free (UAF) and integer overflow to escalate to SYSTEM-level privileges. This high-value exploit netted $30,000 and three Master of Pwn points, contributing significantly to STAR Labs' early dominance.
Pwn2Own's new AI category saw its first successful demonstration when Sina Kheirkhah (@SinSinology) of the Summoning Team, exploited Chroma, a machine learning system, earning $20,000 and two points. Kheirkhah, who won the last competition, also attempted an attack on NVIDIA's Triton Inference Server but encountered a “collision” — the bug used was already known to the vendor. Although the issue had not been patched, the result was still eligible for a $15,000 reward and 1.5 points.

ZDI
Elsewhere, virtualization software and container security were also put to the test. Team Prison Break, competing under the banner “Best of the Best 13th,” used an integer overflow vulnerability to escape Oracle VirtualBox and execute code on the host OS — an exploit that garnered $40,000 and four points. Meanwhile, STAR Labs' Billy and Ramdhan executed one of the day's most lucrative exploits, leveraging a UAF in the Linux kernel to escape Docker Desktop and gain code execution on the underlying system, earning $60,000 and six points.
Other participants also contributed notable entries, including Marcin Wiązowski, who used an out-of-bounds write to escalate privileges on Windows 11, earning $30,000, and Hyeonjin Choi of Out Of Bounds, who leveraged a type confusion vulnerability to achieve similar results, earning $15,000.
Three separate teams targeted NVIDIA Triton Inference Server during the day, including Wiz Research and Viettel Cyber Security. Though successful in demonstrating their exploits, each encountered bug collisions, indicating that their vulnerabilities had already been reported to the vendor. These collisions still qualified for partial rewards under ZDI rules.
ZDI
Pwn2Own Berlin 2025 will continue for two more days, until Saturday. The schedule is packed, and you can check it here.







Leave a Reply