
A Chrome extension titled “Hide YouTube Shorts,” used by 100,000 people, was recently discovered to secretly collect users' browser activity, raising serious concerns about user privacy on Google Chrome Web Store.
Despite appearing to fulfill its stated purpose of hiding YouTube Shorts, the extension was caught transmitting detailed user data to an external server on AWS, potentially exposing numerous users to data theft and phishing attacks. The issue, brought to light by GitHub user ‘c0m4r' investigating suspicious activity, highlights significant security gaps in Google's vetting of Chrome extensions.
Doing more than hiding YouTube Shorts
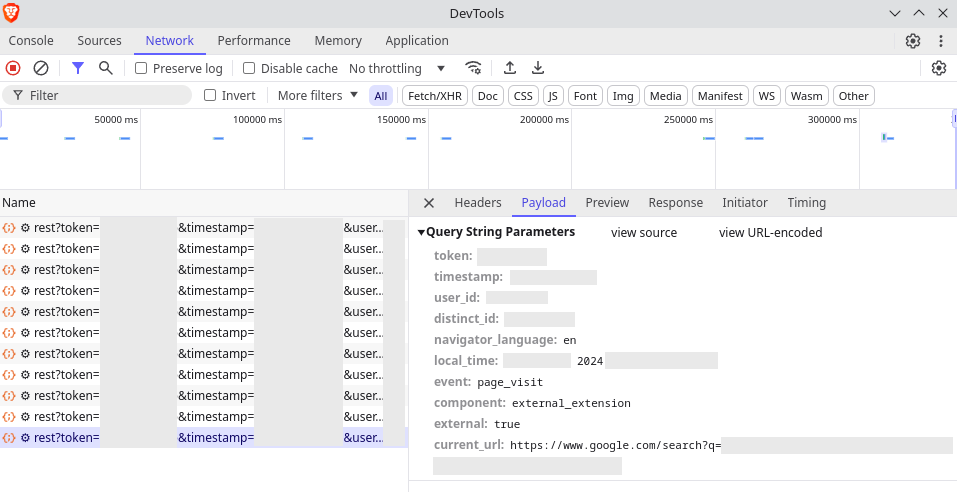
The extension's activity initially sparked suspicion when users began noticing unusual search suggestions on YouTube in various languages, seemingly disconnected from their search history. Further investigation into the extension's network activity revealed it was sending URLs, including specific paths and parameters, alongside other identifying information to a remote server on AWS. Detailed analysis uncovered that the extension was capturing sensitive browsing data, including a unique user ID, installation ID, timestamps, and potentially sensitive data from form entries.
After debugging the extension, c0m4r found that it was sending requests to a suspicious endpoint on AWS and redirecting some users to phishing sites. The extension's current version, 1.8.7, contains a script, background.js, which initiates these requests to an AWS-based API endpoint. Additionally, parts of the code reference an unfamiliar domain, “kra18.com,” which is associated with a potentially malicious DNS entry.
c0m4r | GitHub
Ownership change
Originally developed by a GitHub user named “Probably Raging,” the extension was taken over by a different developer, Roni Shilop. The GitHub repository for the extension was archived in September 2023, and the extension's behavior changed shortly afterward, suggesting a malicious modification post-transfer.
During this transition, the extension adopted broader permissions, which allowed it to access and transmit all visited URLs. The new developer defended these permissions in public comments, disregarding user concerns and signaling possible intentional misuse.
Implications and user impact
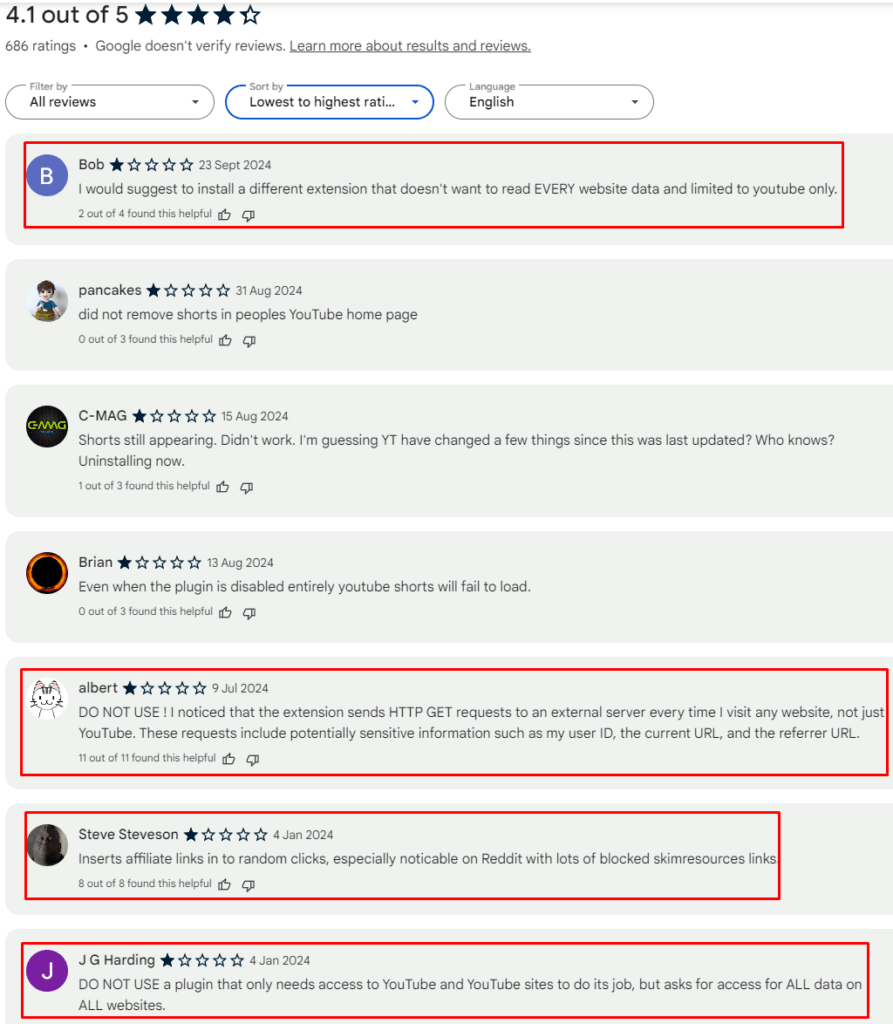
The “Hide YouTube Shorts” extension's unauthorized data collection capabilities give it broad potential to exploit user information, from viewing history to sensitive credentials. Browser extensions, often granted high-level permissions, can read web traffic, access form data, and send out HTTP requests silently, even when set to specific pages like YouTube.
Since Google's Chrome Web Store does not currently monitor such permissions rigorously, malicious extensions like this can infiltrate browsers with minimal oversight, endangering user privacy.
The Chrome Web Store, serving millions, has previously come under scrutiny for hosting malicious extensions. Despite Google's promises to improve extension security, many users report that the Chrome Web Store lacks sufficient reporting mechanisms and security checks, unlike Mozilla's Addons Store.
In this case, the extension continued to collect data and attract users even after reviews indicated potential security issues, and is still listed on the Web Store.
CyberInsider
Defense measures and recommendations
For users who have installed the “Hide YouTube Shorts” extension, immediate action is recommended:
- Uninstall the extension immediately and delete its data if possible.
- Clear browser cache and cookies to remove potentially saved data.
- Change all passwords used since the extension's installation, especially for sensitive accounts.
- Enable multi-factor authentication for added security on important accounts.
- Monitor accounts closely for any unusual activity.
To avoid nasty surprises with extensions that change behavior following ownership transfers, consider installing the ‘Under New Management' extension, which constantly monitors all other extensions installed on Chrome for such changes and alerts the user accordingly.







But I thought Manifest V3 was supposed to stop malware on the CWS?
Its almost like they did that for another reason…
this has been your daily reminder to switch to Firefox for 100% less corporate enshittification in your browsing experience
@D
Go ahead and switch to FF. It has an incredibly tiny market share. Some government and financial sites are not FF friendly. I wouldn’t be surprised if Mozilla retires FF within the next few years.
It’s clear that Google has completely dropped the ball on the Chrome Web Store and app store. It takes thousands of complaints over months for them to even notice, if they bother to act at all. The options for reporting malicious extensions are nearly useless. Plus, there are countless fake extensions that mimic popular tools like AdGuard and uBlock Origin. Google is a major sheet show right now.