
Binarly researchers have uncovered a significant vulnerability in the UEFI Secure Boot process, dubbed “PKfail,” which could compromise the security of numerous devices.
This issue revolves around the mishandling and exposure of Platform Keys (PK), a critical component of Secure Boot.
Discovery and details
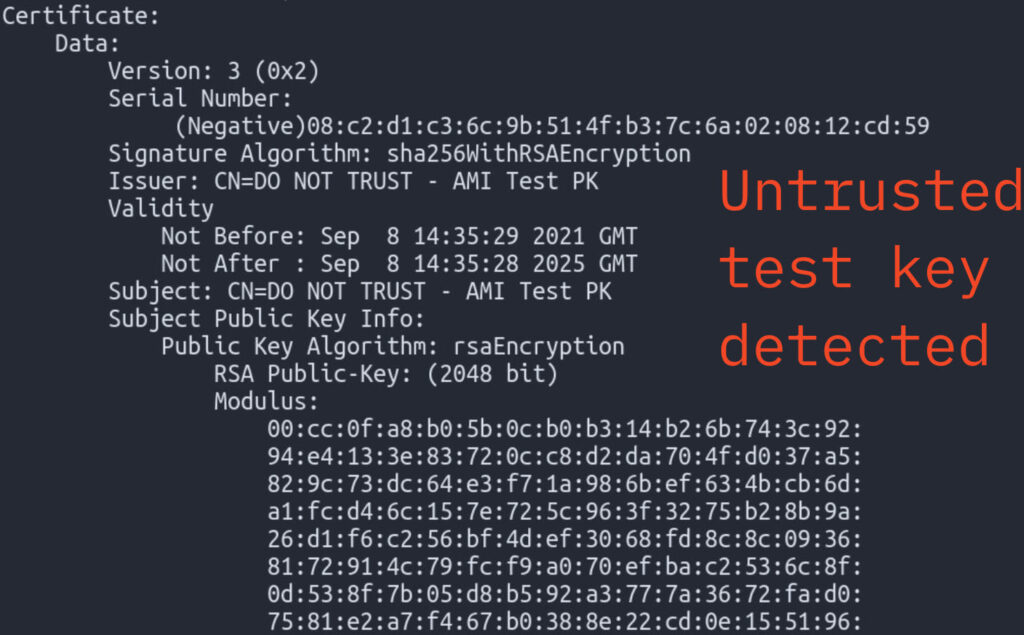
Binarly discovered this vulnerability earlier this year while analyzing a data leak involving American Megatrends International (AMI). The leak included the private key for Secure Boot, known as the Platform Key (PK), which was publicly exposed. This key, used in the firmware of multiple devices, including recently released enterprise devices, was found to be part of a non-production cryptographic key.
In 2023, the team had already identified a similar issue with Intel Boot Guard, where private keys were leaked and used in production, affecting several vendors. The recurrence of such incidents underscores systemic weaknesses in supply chain security within the industry.
Scope and impact
The PKfail issue affects hundreds of device models across the UEFI ecosystem. The vulnerability stems from the use of test Platform Keys generated by Independent BIOS Vendors (IBVs) like AMI, which were not replaced by downstream entities in the supply chain. These keys, intended to be untrusted and clearly marked as such, were found embedded in firmware images from various vendors.
A scan of Binarly's internal dataset of UEFI firmware images, representing tens of thousands of devices from major vendors including Lenovo, Dell, HP, and Intel, revealed that more than 10% of these images use untrusted Platform Keys. The first vulnerable firmware dates back to May 2012, with the latest identified in June 2024, highlighting a 12-year span of potential security risks.
From a technical perspective, PKfail can be summarized as follows:
- Poor cryptographic management: Private keys appeared directly in code repositories with hardcoded paths from build scripts.
- Non-production keys in production: Non-production cryptographic keys responsible for platform security were found in production firmware.
- Lack of key rotation: The same cryptographic keys were used across multiple product lines and devices, exacerbating the risk.
- Cross-OEM key usage: Keys were shared among different manufacturers, increasing the exposure.
PKfail mitigation
To address the PKfail vulnerability, Binarly has developed a free scanning tool, available at PK.fail, to help the security community detect vulnerable devices and firmware. This tool leverages Binary Intelligence technology and boasts a near-zero false positive rate.
Binarly has worked closely with CERT/CC and various vendors, including Dell, to mitigate the issue. Dell's collaboration was particularly noteworthy; they utilized the Binarly Transparency Platform to identify and address the vulnerability in their product lines. Although some Dell devices were initially found to be vulnerable, mitigations were successfully implemented in other product lines.
Recommendations for vendors:
- Ensure the generation and management of Platform Keys follow best practices, using Hardware Security Modules (HSMs).
- Replace any test keys from IBVs with securely generated keys.
Recommendations for users:
- Stay informed about firmware updates and apply security patches as soon as they're made available.
- Follow best practices for device and network security and restrict physical access on your machine.
- Check for PKfail signs on your devices by visiting pk.fail.







Leave a Reply