
Proofpoint researchers uncovered a high-volume email campaign distributing LockBit Black ransomware through millions of messages. This marks the first observed instance of LockBit Black, also known as LockBit 3.0, being propagated via the Phorpiex botnet, a noted shift in cyber threat tactics.
Phorpiex, a malware-as-a-service botnet, has been active in various capacities since 2011, involving data theft and now also ransomware dissemination. Despite numerous disruption attempts, it remains a potent threat in 2024.
LockBit Black represents an evolved form of the LockBit ransomware family, enhanced and released by ransomware affiliates in mid-2022. Its builder was infamously leaked on social media by a disgruntled developer, providing a broader range of threat actors with the means to create customized ransomware attacks.
The attacks observed by Proofpoint do not originate from LockBit's core team or RaaS affiliates but from independent actors using the leaked encryptor in mass-scale operations that do not align with the project's attack strategies. Still, they have the potential to impact a large number of systems worldwide, including corporate and home networks.
Latest LockBit attacks
Starting in late April, over the span of approximately one week, the Phorpiex botnet facilitated the distribution of a significant LockBit Black ransomware campaign. Originating from emails sent by “Jenny Green” from the address Jenny@gsd[.]com, the emails contained a ZIP file named “Document.zip”, which included an executable that, once opened, initiated the ransomware attack.
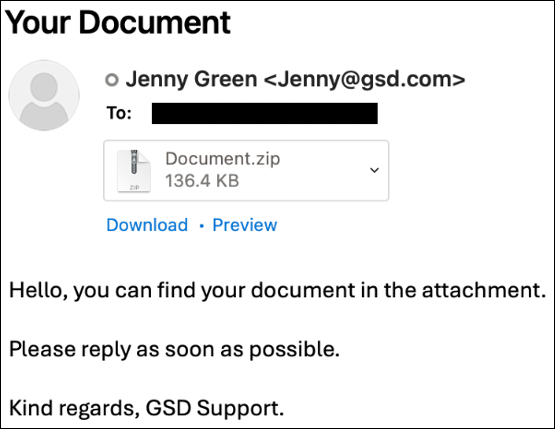
Proofpoint
The executable connected to the botnet's infrastructure to download and activate the LockBit Black ransomware on the victim's system. This campaign was particularly notable for its scope, targeting various global industries in an opportunistic manner rather than focusing on specific entities.
The attack chain is straightforward yet effective, relying on user interaction to succeed. When the attached ZIP file's executable is launched, it makes a network call to the Phorpiex botnet, which then downloads and deploys the LockBit Black payload.
This sample displays data theft behavior and aggressively takes over systems by encrypting files and shutting down essential services. In contrast to previous campaigns where the ransomware executed directly, this method involves significant network activity, making it harder to detect and block at the network level.
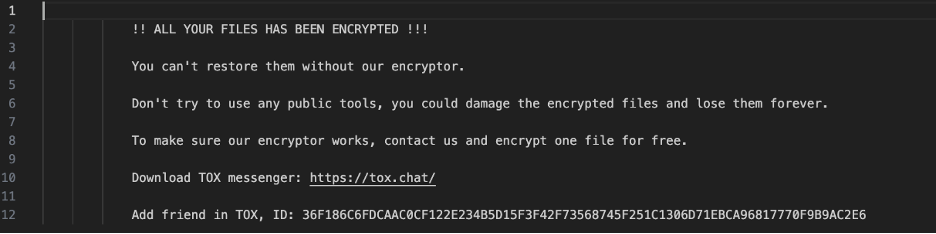
Proofpoint
The use of ransomware as a primary payload in email campaigns on such a massive scale is a significant deviation from recent trends. This method was not predominantly observed since the days preceding 2020, making the resurgence through LockBit Black particularly alarming. The scale of these operations, likened to the historic volumes seen during Emotet campaigns, underscores a concerning evolution in the landscape of cyber threats.
Organizations are advised to enhance their email filtering techniques, educate employees on the risks of opening attachments from unknown senders, and implement advanced endpoint detection and response systems to identify and mitigate such threats swiftly.







Leave a Reply