
Cybersecurity researchers at Forescout Research – Vedere Labs have uncovered a new malware campaign by the Chinese APT group Silver Fox, which exploits trojanized versions of Philips DICOM medical imaging viewers to deploy a remote access trojan (RAT), keylogger, and cryptocurrency miner on victim computers.
The malware, which has evolved over multiple stages since July 2024, uses advanced evasion techniques to bypass security defenses and establish persistent access.
The campaign was identified during a routine threat hunt for new malicious software, where researchers found 29 malware samples masquerading as Philips DICOM Viewers. These trojanized versions of MediaViewerLauncher.exe, the primary executable for Philips’ medical imaging software, were uploaded to VirusTotal from the United States and Canada between December 2024 and January 2025. Further analysis revealed additional samples dating back to July 2024, showing increasing sophistication over time.
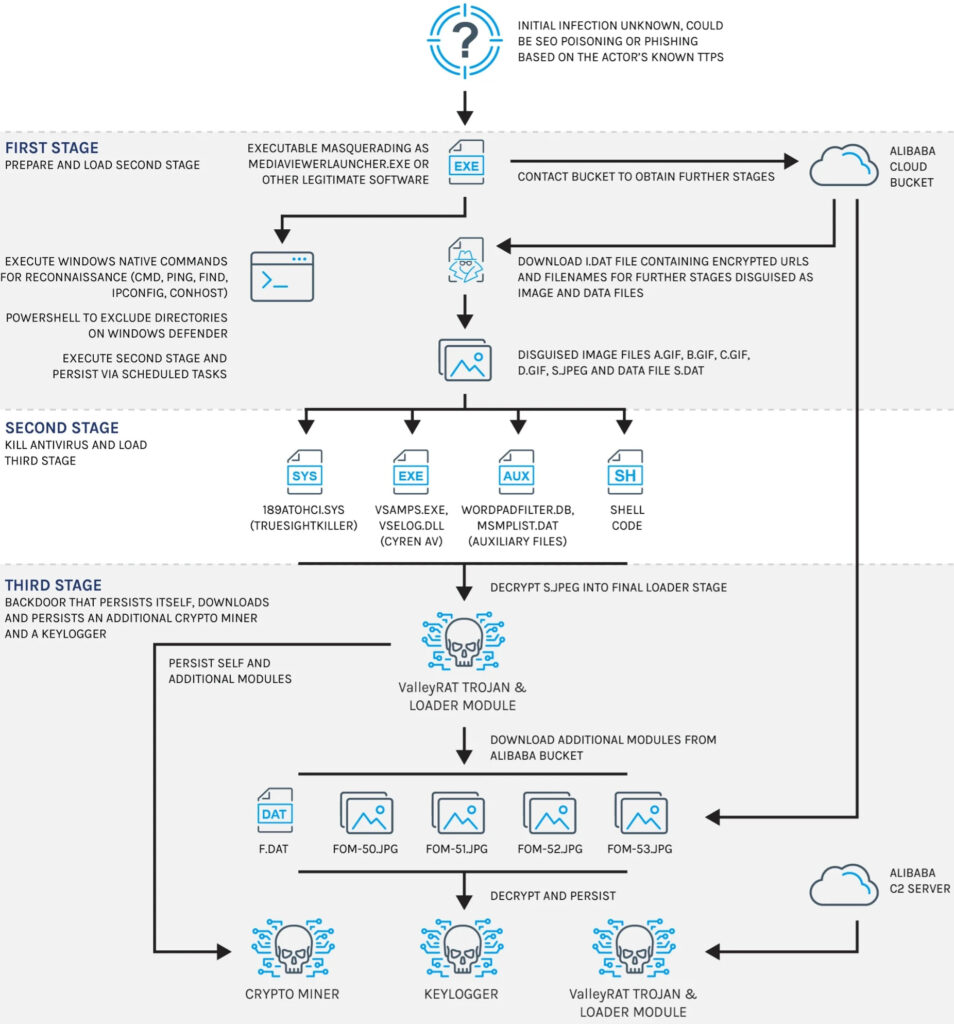
The initial infection stage involves executing Windows utilities like ping.exe, find.exe, cmd.exe, and ipconfig.exe for reconnaissance. The malware then modifies Windows Defender settings to exclude system directories from scanning, making detection more difficult. Later stages involve downloading encrypted payloads from an Alibaba Cloud bucket, including TrueSightKiller, a tool that disables antivirus software, and a modified version of ValleyRAT for remote access and command-and-control (C2) communication.
Targets and impact
Philips, a multinational healthcare technology company, develops DICOM (Digital Imaging and Communications in Medicine) viewers used by hospitals and patients to review medical images such as MRIs and CT scans. While these infections primarily target patients using trojanized versions of the software, they pose a serious indirect risk to healthcare delivery organizations (HDOs).
If infected patient devices are connected to hospital networks — such as during hospital-at-home programs — the malware could provide Silver Fox with an initial foothold into critical healthcare infrastructure.
Philips statement and clarification
Philips has responded to reports about the malware campaign, emphasizing that Philips DICOM viewers downloaded from authorized Philips sources remain secure and unaffected.
A Philips spokesperson stated: “Philips is aware of security researcher reports that a known hacker group is distributing malware disguised as Philips medical imaging viewer software (also known as DICOM viewers) to unsuspecting users via unauthorized sites and methods, including phishing techniques. Philips DICOM viewers that are downloaded from authorized Philips sources – as required – are not affected by this issue and continue to be safe for use. This reported malware campaign does not originate with Philips products or servers. Philips DICOM viewers from legitimate sources have not been compromised, and this is not a security vulnerability with the product itself.”
Furthermore, Philips advises users to download DICOM viewers only from authorized Philips sources to ensure security. Customers with questions about this issue may contact the Philips Product Security team at: productsecurity@philips.com.
Forescout Research – Vedere Labs has also clarified that there is no indication Philips or its medical devices were compromised to spread these malicious versions of the DICOM Viewer. The attackers behind this campaign are known to rely on phishing and watering hole tactics to distribute malware.
Technical details
The malware consists of multiple stages designed to evade detection and maintain persistence.
The first-stage payload (MediaViewerLauncher.exe) conducts system reconnaissance and modifies Windows Defender settings to exclude key system directories from scanning. The second-stage payload, downloaded from Alibaba Cloud, deploys TrueSightKiller to disable antivirus protections and terminates security processes. Finally, the malware installs ValleyRAT for remote access, a keylogger to steal credentials, and a cryptominer to exploit system resources.
Forescout
For obfuscation, it uses API hashing and indirect API retrieval to conceal function calls. To evade detection, the malware implements long sleep intervals, masked DLL loading, and system fingerprinting. Finally, to establish persistence on compromised systems, it registers Windows scheduled tasks to relaunch the malware at every system boot.
This attack follows a recent campaign by another Chinese APT group, Tonto Team, which exploited ultrasound imaging software to deploy malware in healthcare networks. The similarities between these operations suggest a growing trend of targeting medical imaging applications as entry points into healthcare systems.







Leave a Reply