
A new attack called U-Print can passively identify smartphone users by capturing and analyzing encrypted Wi-Fi traffic.
Unlike previous methods that focused on app recognition or required IP-level access, U-Print operates solely on the wireless MAC-layer and can infer not just which apps are in use, but also specific in-app actions and the identity of the user, without needing to decrypt traffic or defeat MAC address randomization.
arxiv.org
Profiling through Wi-Fi metadata
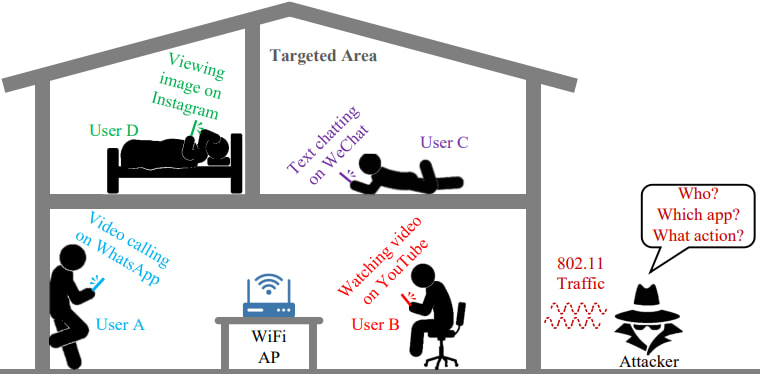
The U-Print threat model, developed by Chinese researchers, assumes that an attacker places a passive sniffer within the wireless range of a target environment (e.g., an office or home). No password or network access is required, only proximity to the Wi-Fi signal. The system then builds behavioral profiles of individuals based on their interaction patterns with apps, potentially enabling inferences about private attributes like age, gender, or even mental health.
Previous attacks could detect app usage but failed to reliably identify the human user behind the traffic, especially under MAC address randomization, a defense now widely adopted on modern smartphones.
The U-Print approach is built around the idea that individual preferences, such as the choice of apps and the way people use them, generate distinct patterns in MAC-layer metadata like packet size, timing, and direction. For instance, two users might both use WhatsApp, but one might favor text chat while the other uses voice messages, leading to subtly different traffic patterns.
arxiv.org
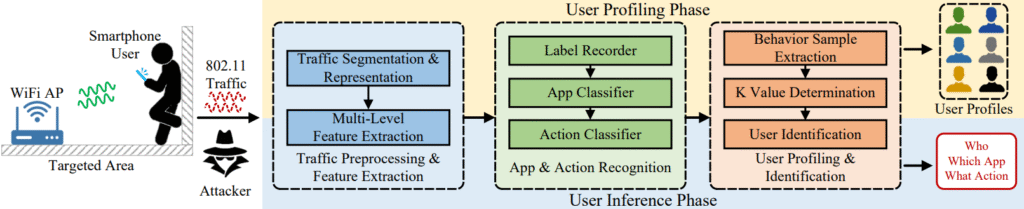
To capture these nuances, U-Print performs three major steps:
- Traffic preprocessing: It captures 802.11 frames and filters only the data frames, extracting metadata such as arrival time, frame size, and direction (uplink or downlink).
- App and action classification: Using Temporal Convolutional Networks (TCNs) with OpenMax extensions, U-Print identifies apps and specific in-app actions even when those apps were not present during training (open-world classification).
- User profiling and identification: It converts traffic into behavioral sequences, applies clustering to profile unique users, and recognizes individuals in future traffic sessions without relying on static MAC addresses.
arxiv.org
Experimental results
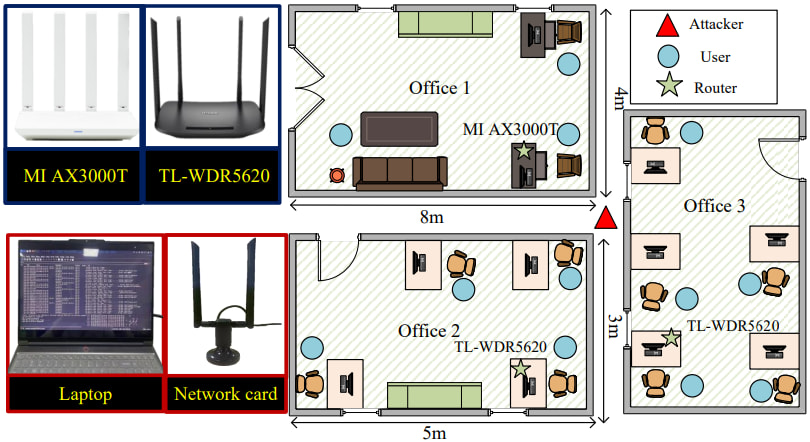
The researchers tested U-Print in real-world office environments using a Lenovo laptop and a Kali Linux-equipped network card to passively capture Wi-Fi traffic from 12 smartphone users across 40 mobile apps. The results are striking:
- App classification accuracy: 98.7% in closed-world and 87.6% in open-world settings.
- Action classification accuracy: 96.8% in closed-world and 86.1% in open-world settings.
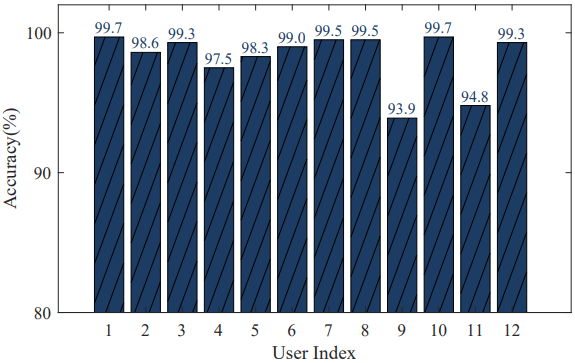
- User identification accuracy: 98.4% with an F1 score of 0.983, even under randomized MAC addresses.
arxiv.org
The system’s performance remained robust despite common real-world challenges such as:
- Packet loss: Tolerant up to 15% packet drop with minimal performance degradation.
- Background app noise: Still accurately classifies user behavior even when multiple apps generate concurrent traffic.
- Environmental variation: Performed consistently across three separate office locations
While U-Print is theoretical, the research exposes a significant gap in current wireless security assumptions, where even encrypted Wi-Fi networks using modern standards like WPA3 and MAC randomization are not enough to prevent inference attacks that target user identity and behavior.
To defend against U-Print-style fingerprinting, users and developers can consider traffic obfuscation, randomized packet size and timing, MAC randomization, and mixing behavioral signals.







Lots of fluff in the blog. Here is what you need to know:
* The study used a small test group—just 12 people and 40 apps—so results might not hold up with larger or more varied users.
* Testing happened in quiet indoor Wi-Fi setups, not in busy public spaces where signals are messy.
* The system works best when it already knows which apps it’s looking for. Accuracy drops when it sees new or unfamiliar apps.
* If a person uses several apps at once or there’s lots of other Wi-Fi traffic nearby, accuracy goes down.
* The method relies on learning a person’s habits, so if they change how they use their phone or the app updates, the system’s recognition weakens.
* An attacker would need to be physically close enough to capture a device’s Wi-Fi signals and collect a lot of data over time.
* The research didn’t test cases where people share phones, use VPNs, or switch between Wi-Fi networks.
* It’s a controlled proof of concept, not a real-world attack that has been observed outside the lab.
Thanks.
CyberInsider, would you consider adding Like/Dislike reader reactions to comments (if it can be done without sacrificing privacy)?
Hey Finch, yes we can look into that.