
A new investigation by Citizen Lab has exposed the expanding reach of Israeli spyware vendor Paragon Solutions and its tool Graphite, revealing its use in WhatsApp zero-click attacks and an undisclosed iOS zero-day exploit.
The company's flagship spyware was discovered in targeted surveillance operations across multiple countries, including Italy, Canada, Australia, Denmark, Cyprus, Singapore, and Israel. These findings challenge Paragon's claims of an “abuse-proof” business model and raise concerns over the growing misuse of spyware by democratic governments.
WhatsApp zero-click attacks
Paragon's Graphite spyware was deployed using a zero-click exploit on WhatsApp, meaning victims were infected without needing to click malicious links or interact with harmful content. WhatsApp played a crucial role in detecting and neutralizing the attack, working with Citizen Lab to mitigate the infection and notify over 90 targeted individuals, including journalists and activists.

Citizen Lab
On Android devices, Graphite embedded itself within WhatsApp's process, allowing attackers to intercept encrypted conversations without installing separate spyware components. A forensic artifact called BIGPRETZEL confirmed active infections, with logs showing spyware activity as recently as January 31, 2025.
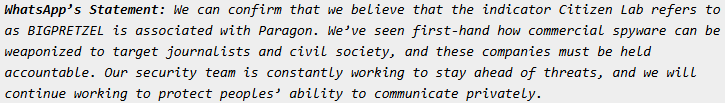
iOS exploit used against iPhone users
In addition to the WhatsApp attack, forensic analysis of an infected iPhone revealed signs of a zero-day exploit. The victim, a human rights activist in Italy, received an Apple threat notification in November 2024, and further analysis uncovered SMALLPRETZEL, a suspicious CloudKit-related anomaly on June 13, 2024.
Apple later confirmed that the attack exploited a previously unknown iOS vulnerability, which was patched in iOS 18. This suggests that Paragon or its clients had access to an undisclosed iOS zero-day exploit before it was publicly fixed — a major red flag regarding the company's true capabilities and client base.
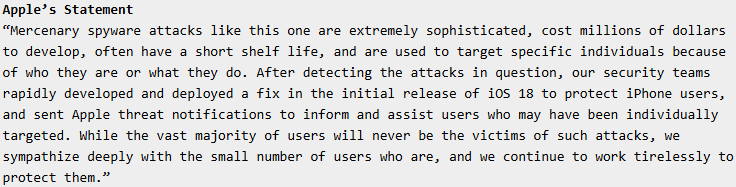
Targeting the civil society
Paragon's spyware was found targeting journalists and humanitarian workers in Italy, a confirmed Paragon customer. Among those infected:
- Francesco Cancellato, Editor-in-Chief of Fanpage.it, an outlet known for investigative journalism.
- Luca Casarini, founder of Mediterranea Saving Humans, an NGO rescuing migrants at sea.
- Dr. Giuseppe “Beppe” Caccia, a scholar and co-founder of Mediterranea Saving Humans.
WhatsApp's alerts and forensic evidence strongly suggest that Graphite was used for political surveillance, as these individuals worked on human rights and migration issues, areas of growing sensitivity in Italy.
Initially, Italy denied involvement but later admitted to purchasing and deploying Paragon's Spyware — while insisting it was not used against activists. Facing public backlash, the government suspended its deployment pending investigation.
Links to the U.S. and Canada
Citizen Lab's investigation also uncovered Paragon's suspected deployment in Canada, linked to the Ontario Provincial Police (OPP). Analysis of server infrastructure suggests that multiple Ontario-based law enforcement agencies have access to spyware, contributing to a growing domestic surveillance ecosystem.
Meanwhile, in the United States, Paragon has ties to law enforcement and intelligence agencies such as the U.S. Drug Enforcement Administration (DEA), which was previously reported to have used Graphite, and the Immigration and Customs Enforcement (ICE), which signed a $2 million contract with Paragon, later paused under White House review. Also, Paragon was acquired by AE Industrial Partners, a U.S. private equity firm, in a $900 million deal.
Defensive measures
While zero-click and zero-day exploits are notoriously difficult to defend against, users can take steps to minimize risk:
- Keep WhatsApp and iOS/Android updated by applying the latest security patches.
- Enable two-step verification to add an extra security layer to messaging accounts.
- Monitor device activity for unexpected reboots, battery drain, or high data usage.
- Use independent security tools, such as Citizen Lab's forensic tools or Amnesty International's Mobile Verification Toolkit (MVT), to detect infections.
The Paragon revelations highlight the growing challenge of regulating government-backed spyware in democratic nations. Despite claims of strict client screening, Graphite was used in WhatsApp-based attacks on journalists, human rights groups, and political critics—mirroring past abuses seen with NSO Group's Pegasus.
With evidence of a zero-day exploit, zero-click infections, and cross-platform targeting, Paragon's Graphite represents a new frontier in covert surveillance.







Leave a Reply