
Kaspersky researchers warn of sophisticated schemes where attackers bypass two-factor authentication (2FA) by employing phishing tactics and advanced OTP (one-time password) bots. The cybersecurity firm says the revelation sheds light on the growing threats to online security and the need for heightened user vigilance.
OTP bots operation scheme
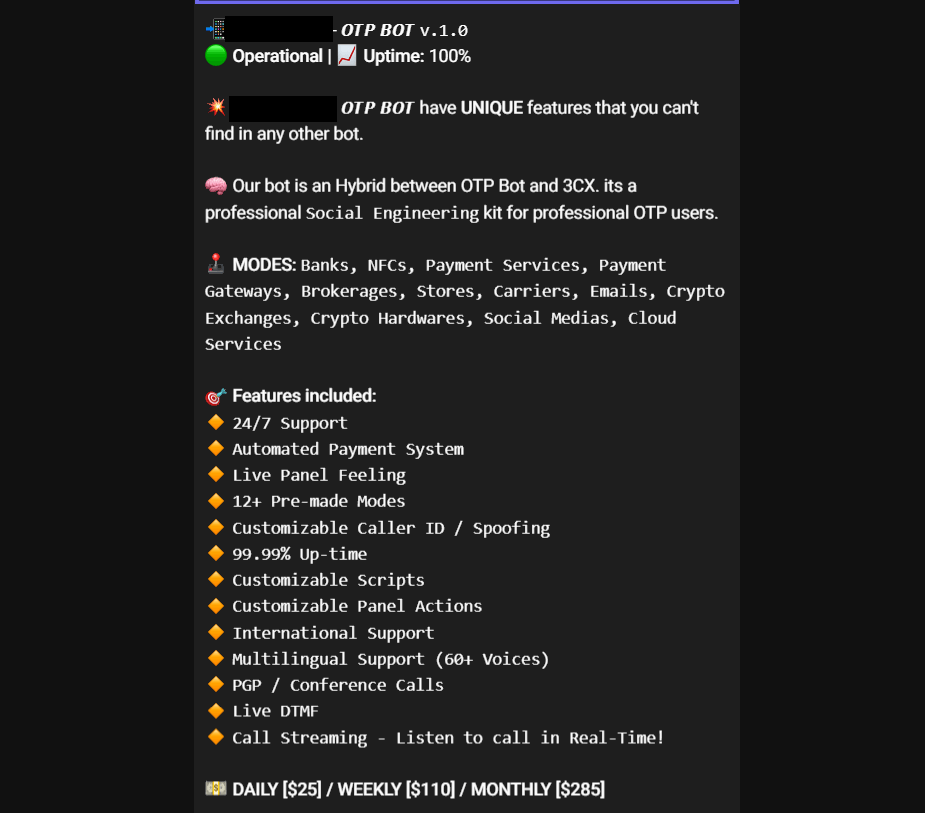
Kaspersky details how attackers exploit social engineering techniques and automation tools to bypass 2FA, particularly those relying on one-time passwords (OTPs). The OTP bots are designed to intercept these verification codes by manipulating victims into divulging them over phone calls.
OTP bots play a crucial role in this scheme by following a premeditated script to trick victims. The typical process includes:
- Obtaining the victim's credentials.
- Triggering an OTP request to the victim's phone.
- The OTP bot calling the victim and convincing them to share the code.
- The attacker using the received OTP to access the victim's account.
These bots are sophisticated, often featuring multilingual support, gender-specific voices, and spoofing capabilities to mimic legitimate organizations. Prices for these bots range from $140 to $420 per week, payable in cryptocurrency, making them accessible to a broad range of cybercriminals.
Kaspersky
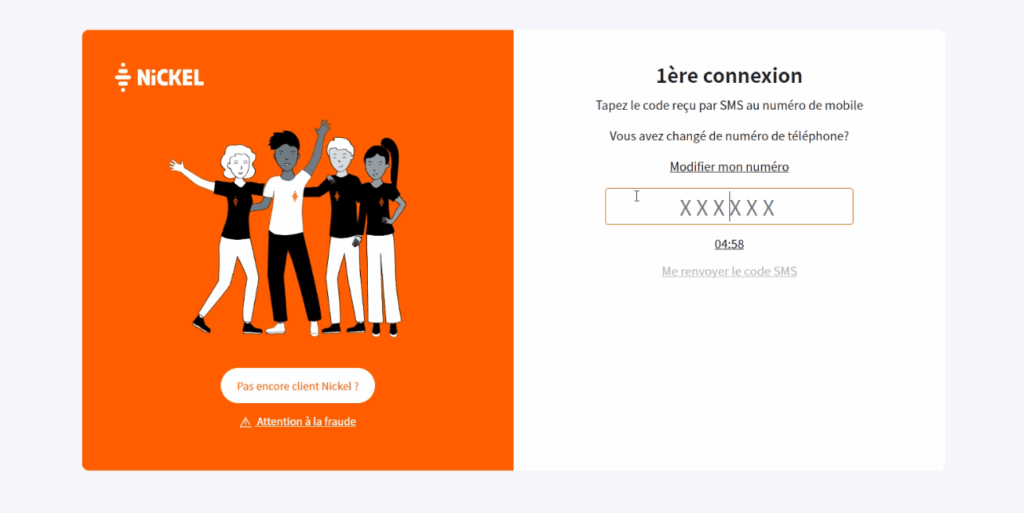
Phishing kits equipped with real-time interception capabilities have evolved to assist attackers in this process. These kits can generate convincing phishing sites and administer collected data via panels integrated with messaging platforms like Telegram. Once a victim's login details are entered, the attacker prompts for the OTP to gain instant account access.
Kaspersky
Widespread threat
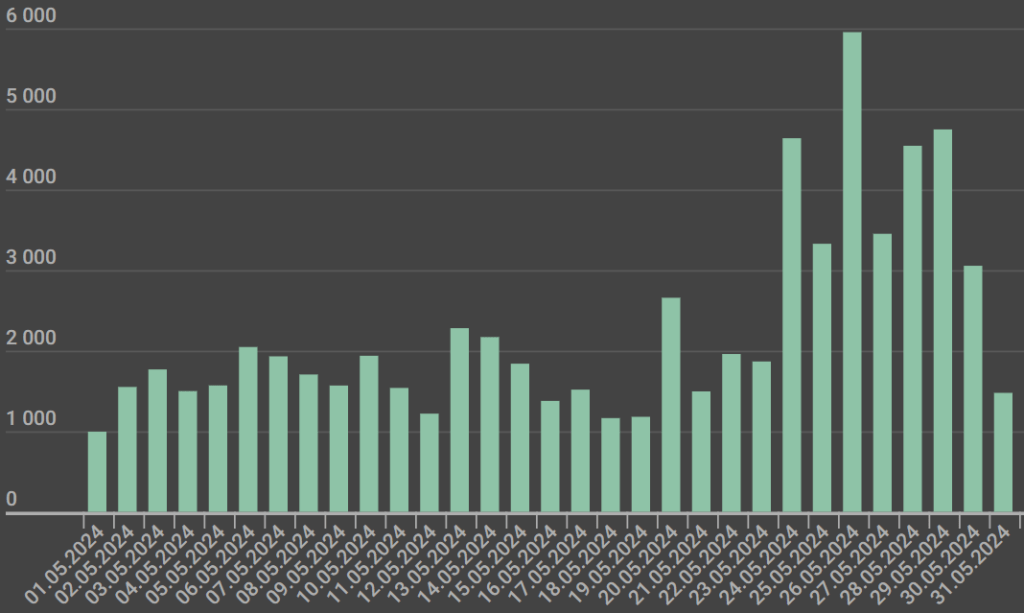
Kaspersky's research highlights the widespread use of such phishing kits. In May 2024 alone, the firm’s security products thwarted nearly 70,000 attempts to visit phishing sites targeting financial institutions. Additionally, over 1,200 phishing pages were identified as part of multi-purpose kits capable of real-time OTP interception.
Kaspersky
These attacks pose significant risks to both individual users and organizations, particularly financial institutions, which are frequent targets. The evolving nature of these threats underscores the need for robust security measures beyond just 2FA.
Recommendations
To safeguard against these sophisticated attacks, Kaspersky advises the following:
- Avoid clicking on links in suspicious emails; manually enter URLs into the browser.
- Verify the website's legitimacy before entering credentials.
- Never share OTPs over the phone, regardless of how convincing the caller may sound.
- Use reputable and up-to-date security solutions that effectively block phishing attempts.






Leave a Reply