
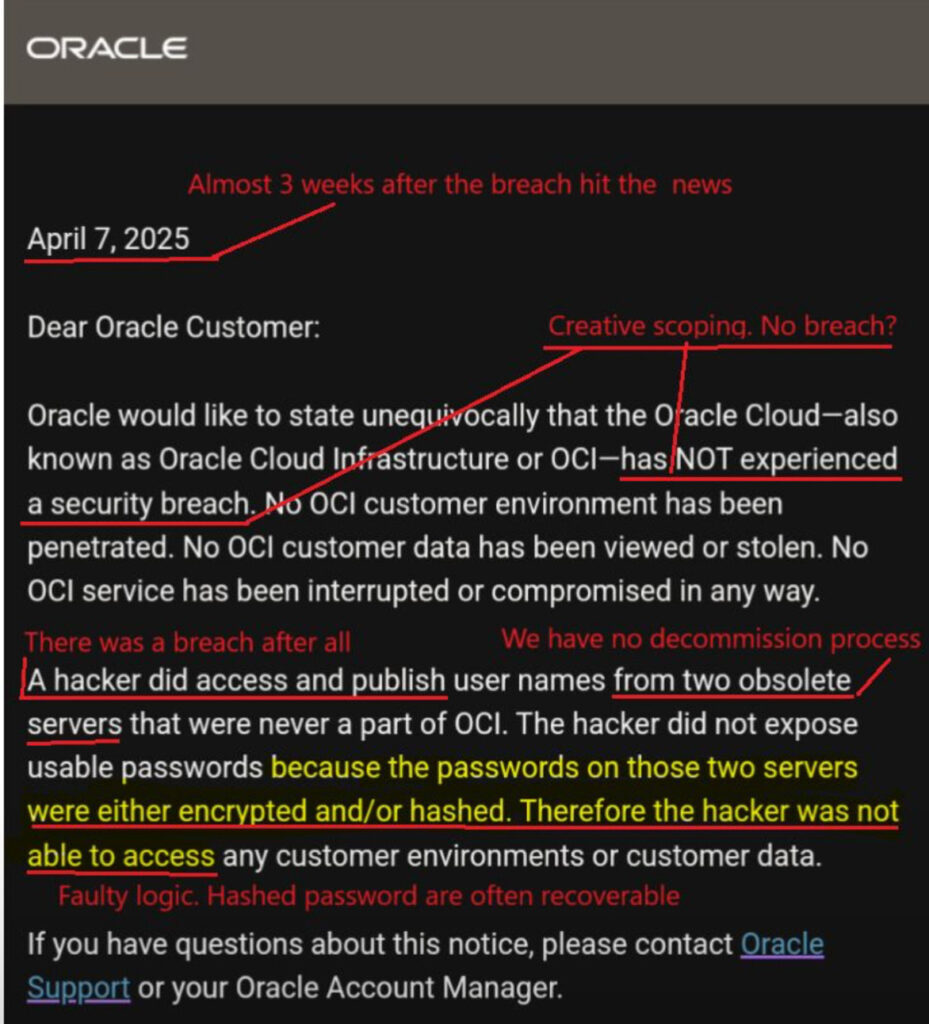
Oracle has begun quietly notifying customers of a recent cybersecurity incident — while simultaneously denying it qualifies as a data breach.
The notices, a sample of which was leaked by security researcher Kevin Beaumont on BlueSky, mark the first formal communication from the tech giant to customers impacted by the leak of millions of records from an outdated Oracle system.
The notification follows weeks of mounting pressure after Oracle initially dismissed reports of a breach, only to later admit that a legacy environment had been compromised. In the notice, Oracle claims that the affected environment was “isolated from Oracle Cloud Infrastructure (OCI),” emphasizing that no Gen 2 cloud systems were breached. Despite acknowledging unauthorized access to systems containing sensitive customer data, Oracle stops short of labeling the incident a breach — a semantic stance that has drawn criticism from the security community.
Beaumont | BlueSky
Beaumont, a respected incident responder and former Microsoft threat analyst, called Oracle's latest communication a case of “wordsmithing.” In his post, he pointed out that the breach affected Oracle's SaaS solutions — systems managed entirely by Oracle — and questioned how long the attacker maintained access, what they did with it, and why legacy systems remained “unmanaged and insecure.” He described Oracle's response as “exceptionally poor for a company who manage extremely sensitive data.”
The original breach, which came to light in March 2025, involves a threat actor using the alias “rose87168” offering to sell over six million Oracle customer records on the dark web marketplace BreachForums. Data leaked in the incident includes encrypted LDAP and SSO credentials, Java Keystore (JKS) files, and JPS keys used for managing enterprise authentication. While Oracle initially denied any cloud compromise, forensic analysis by firms such as Trustwave and CybelAngel confirmed the authenticity of the data.
Oracle eventually acknowledged that the breach stemmed from a deprecated “legacy environment,” claiming it had been decommissioned in 2017. However, records included in the leak show data as recent as 2024, undermining the company's timeline and raising questions about its internal data management practices. Sources familiar with the investigation said the attack likely originated through a known Java vulnerability in Oracle's first-generation cloud systems. Malware and a webshell were reportedly deployed to exfiltrate data from an internal identity management database.
Oracle Corporation, based in Austin, Texas, is a multinational technology company known for its cloud infrastructure, enterprise software, and database products. The company serves critical sectors, including finance, government, defense, and healthcare. While its Gen 2 infrastructure includes hardened security features, this incident highlights the risks posed by outdated environments that remain exposed and under-managed.
Despite Oracle's insistence that the attack was confined to legacy systems, researchers found indications that threat actor “rose87168” had access to Oracle Cloud subdomains, further complicating the company's claim that OCI remained untouched. The FBI and CrowdStrike are currently investigating the incident, while the attacker reportedly continues to demand a $20 million ransom.
For organizations relying on Oracle services, the lack of transparency in the company's incident response has created significant uncertainty. Given the situation, it is recommended that they rotate all credentials associated with Oracle SaaS or IDM systems, audit access logs for unusual activity dating back to January 2025, and segment legacy environments from production networks or fully decommission them.







Leave a Reply