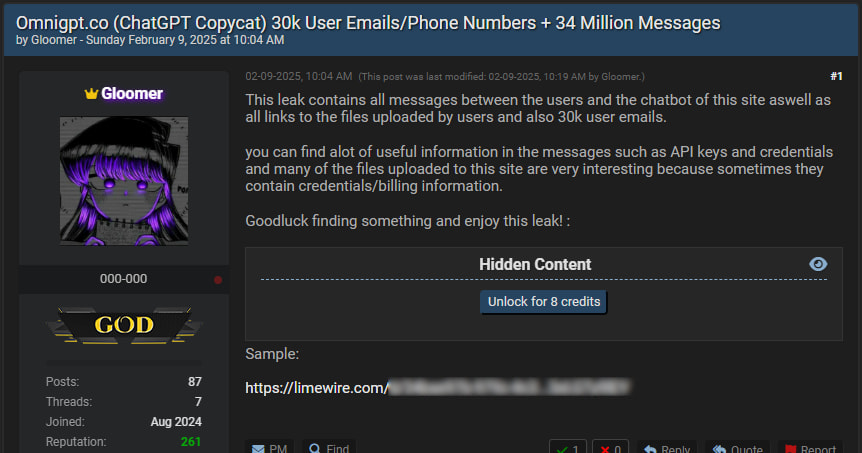
A threat actor going by the name “Gloomer” has claimed responsibility for a significant data breach at OmniGPT, an AI aggregator platform.
The hacker alleges that over 34 million user-chatbot interactions, 30,000 email addresses, and phone numbers have been leaked on BreachForums, a notorious hacking forum. Additionally, the breach is said to include links to user-uploaded files, some containing sensitive data such as API keys, credentials, and billing information.
OmniGPT is an AI aggregator that allows users to interact with multiple AI models from different providers, including OpenAI's ChatGPT, Google's Gemini, and Anthropic's Claude. The platform simplifies access to AI by eliminating the need for multiple subscriptions, making it popular among researchers, developers, and businesses experimenting with AI technologies.
The data was posted online on February 9, 2025, with “Gloomer” asserting they had successfully infiltrated OmniGPT's systems. The exposed dataset includes:
- User emails and phone numbers: At least 30,000 users have had their contact details leaked.
- Chatbot conversations: A massive archive of 34 million interactions between users and various AI models has been exposed.
- Uploaded files: Numerous files stored on OmniGPT's servers have been compromised, with some reportedly containing financial information and login credentials.
Hackers on the forum have expressed interest in the data, particularly in extracting valuable credentials from chatbot conversations.
Impact and response
CyberInsider has reached out to OmniGPT requesting a comment on Gloomer's allegations, and we will update this post when we hear back. As of writing, the platform has not made any public statements.
If confirmed, this breach could have serious consequences. Exposed chatbot interactions may contain personal, financial, or proprietary business information, raising privacy concerns. API keys and login credentials within the leaked dataset could also lead to account takeovers or further security breaches.
OmniGPT users are recommended to reset their passwords immediately, revoke all API keys, and treat unsolicited communications with extreme caution. If available, enable multi-factor authentication on your account.







Leave a Reply