
Nothing Chats, a messaging service that promised to give users of Nothing phones the ability to chat with their friends over iMessage as if they would do from an iPhone device, has been removed from Google Play store over concerns about its security.
This comes only a few days after the smartphone maker with the meteoric rise to popularity ran an aggressive marketing campaign about supporting “blue bubbles,” which is a burning matter in the U.S.
The official explanation the consumer electronics startup gave on X was that they had to retract the app to “fix several bugs.”
Android security researchers directly disputed this excuse and instead raised much more alarming issues. Specifically, the assurances that the service provider, Sunbird, gave about the use of end-to-end encryption were shown to be doubtful, if not outright false.
nothing.tech
Over the weekend, French Android software developer Dylan Roussel revealed that Sunbird has access to all user messages and files, which are transmitted in clear-text form on Nothing Chats, so there’s no effective end-to-end encryption involved.
h
Another analyst, @uwukko, also published a thread on X where similar results are presented, claiming that communications on Nothing Chats aren’t encrypted, allowing Sunbird or any other intermediary to capture sensitive user communications.
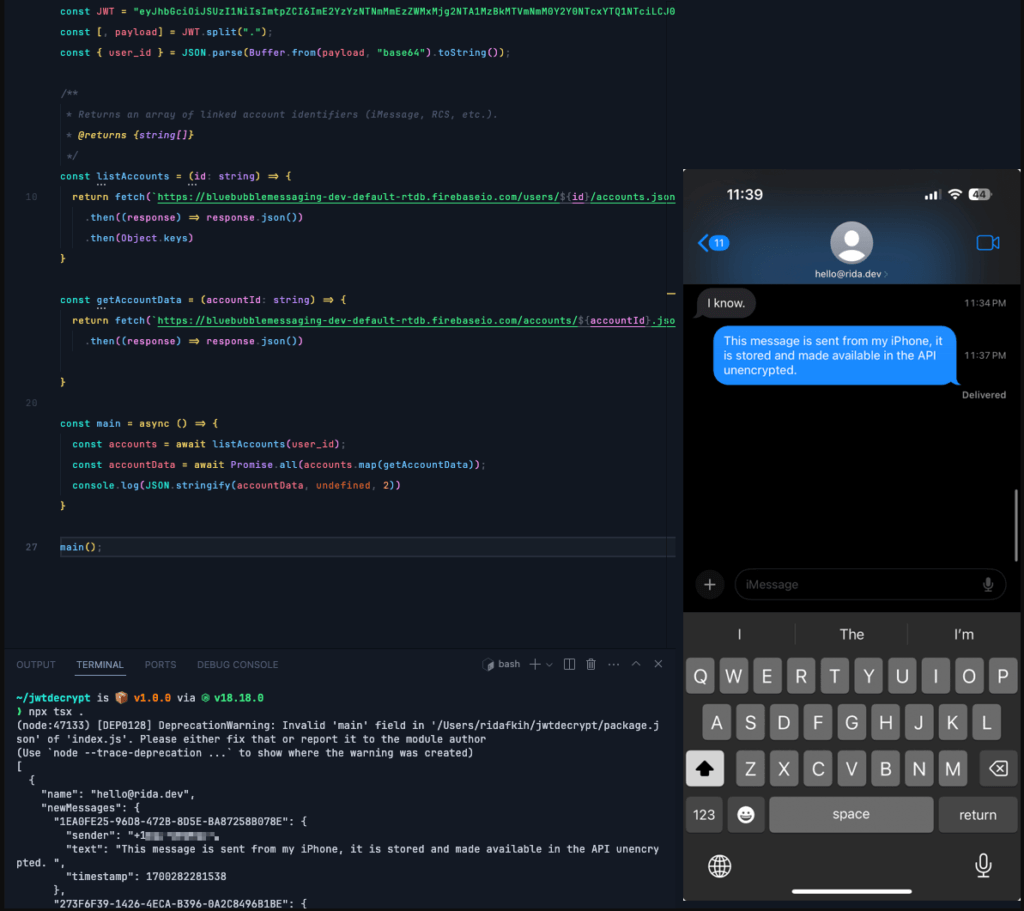
Android security researcher Kishan Bagaria even went as far as to publish a proof-of-concept script on GitHub to showcase that Sunbird stores user messages in clear text in databases on their servers and then transmits them onto the user devices. In a detailed writeup on his blog, Bagaria presents two major vulnerabilities on Nothing Chats concerning data in transit flaws and data at rest gaps.
Specifically, Bagaria has found the following issues:
- Sending JWT (JSON Web Token) via unsecured channels, making all requests vulnerable to interception.
- Having an exposed registration endpoint that handles sensitive Apple ID information.
- Sending API tokens outside SSL protection, potentially giving attackers access to all user data (account details, messages, attachments) in real-time.
- Inadequate end-to-end encryption implementation that is negated by Sunbird decrypting and storing unencrypted data payloads in their database.
- Exposure of messages and attachments to attackers monitoring the Firebase Realtime DB.
- An attacker who has intercepted JWT can access and download all user information and conversations.
texts.blog
All that constitutes an egregious breach of user privacy on Nothing Chat, compounded by the failure of both Nothing and Sunbird to publicly acknowledge any wrongdoing, significantly undermines trust.
The absence of transparency regarding this situation only exacerbates the issue, making it challenging to regain user confidence should Nothing Chats with iMessage support return on people’s devices.







Leave a Reply