
A grand jury in Kansas City, Kansas, has indicted Rim Jong Hyok, a North Korean national, for his role in a ransomware conspiracy targeting U.S. hospitals and healthcare providers. The group, known as “Andariel,” used the ransom proceeds to fund further cyberattacks on defense and technology organizations globally.
The indictment reveals that Rim and his co-conspirators, working under North Korea’s Reconnaissance General Bureau, deployed Maui ransomware to extort U.S. hospitals. These attacks disrupted healthcare services and put patient care at risk. The ransom payments were laundered through Chinese facilitators to fund subsequent hacking operations targeting critical infrastructure.
The Justice Department and FBI identified Rim's involvement through extensive investigation. The indictment was announced yesterday, with charges including conspiracy to commit computer fraud and money laundering.
The ransomware attacks severely hindered the ability of healthcare providers to deliver timely care, endangering patients and causing significant financial losses. The group's actions highlighted the vulnerability of critical infrastructure to cyber threats.
Beyond healthcare, Andariel used the laundered ransom funds to lease servers for additional attacks. Victims included U.S. defense contractors, Air Force bases, and international entities in South Korea, Taiwan, and China. The group exploited vulnerabilities such as Log4Shell to steal sensitive information, including military and technical data.
According to a Mandiant report published yesterday, APT45, also known as “Andariel,” is a North Korean cyber operator active since 2009, now engaging in financially motivated ransomware operations. Distinct from other North Korean groups, APT45 has evolved from espionage targeting government and defense entities to include financially driven cybercrimes, including attacks on the healthcare sector using Maui ransomware.
The group's activities, which have also targeted nuclear facilities and crop science divisions, highlight its role in supporting North Korean state priorities and circumventing international sanctions to fund the regime's ambitions.
The investigation that uncovered the North Korean's identity involved multiple U.S. agencies, including the Air Force Office of Special Investigations, NASA-OIG, and the Department of Defense Cyber Crime Center. International partners, such as South Korean and UK agencies, also contributed to the efforts.
Seizures and rewards
Authorities in the U.S. have interdicted approximately $114,000 in virtual currency linked to the ransomware attacks. Previously, $500,000 in virtual currency was seized in related operations.
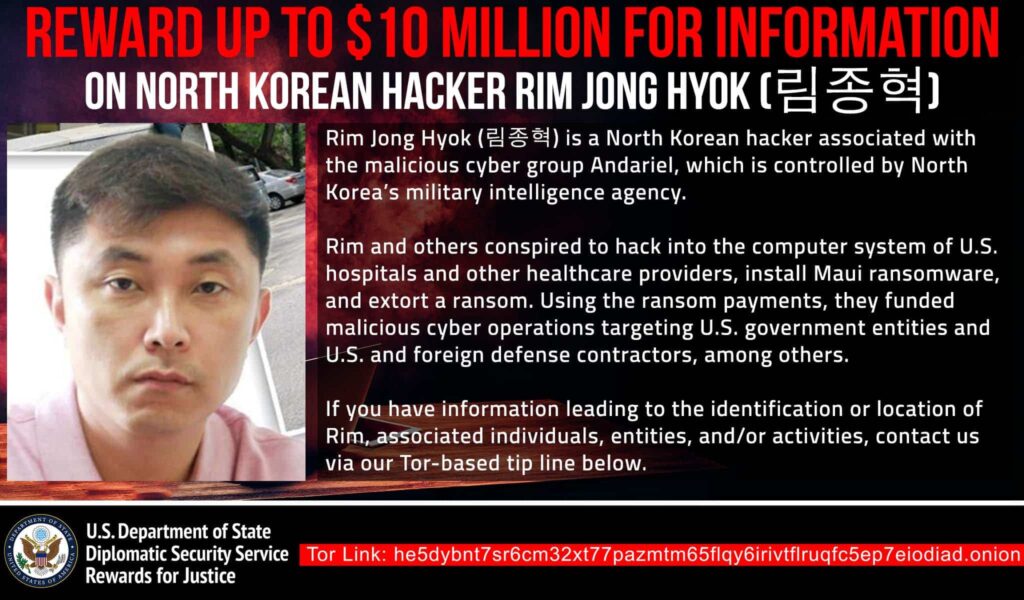
The U.S. State Department is now offering up to $10 million for information leading to Rim's location or identification. This reward is part of the broader Rewards for Justice program, targeting foreign government-directed cybercriminals.







Leave a Reply