
A security researcher has demonstrated an innovative phishing attack that takes advantage of Google’s debatable decision to offer risky top-level domains (TLDs) such as ZIP, for use on websites and email addresses.
At the beginning of the month, Google expanded the internet’s namespace by adding eight new TLDs, namely .dad, .phd, .prof, .esq, .foo, .zip, .mov, and .nexus. The ZIP and MOV, in particular, spurred a series of debates within the cybersecurity community, with critics warning that the decision blurs the line between file names and web addresses.
The concerns are that filenames ending with “.zip” (archives) or “.mov” (videos) are now automatically converted into clickable URLs by many apps and online services, creating ambiguity that creative threat actors can easily exploit.
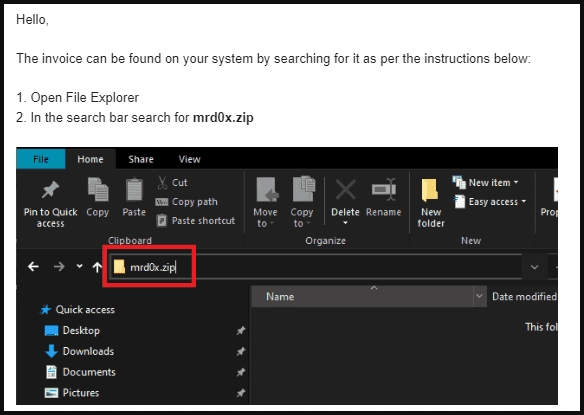
The problem is further magnified when considering the novelty of the ZIP domains, which guarantees that many people will remain ignorant about their existence for a prolonged period, giving attackers a first-class opportunity to explore the exploitation potential of this new domain space.
ZIP in the Browser
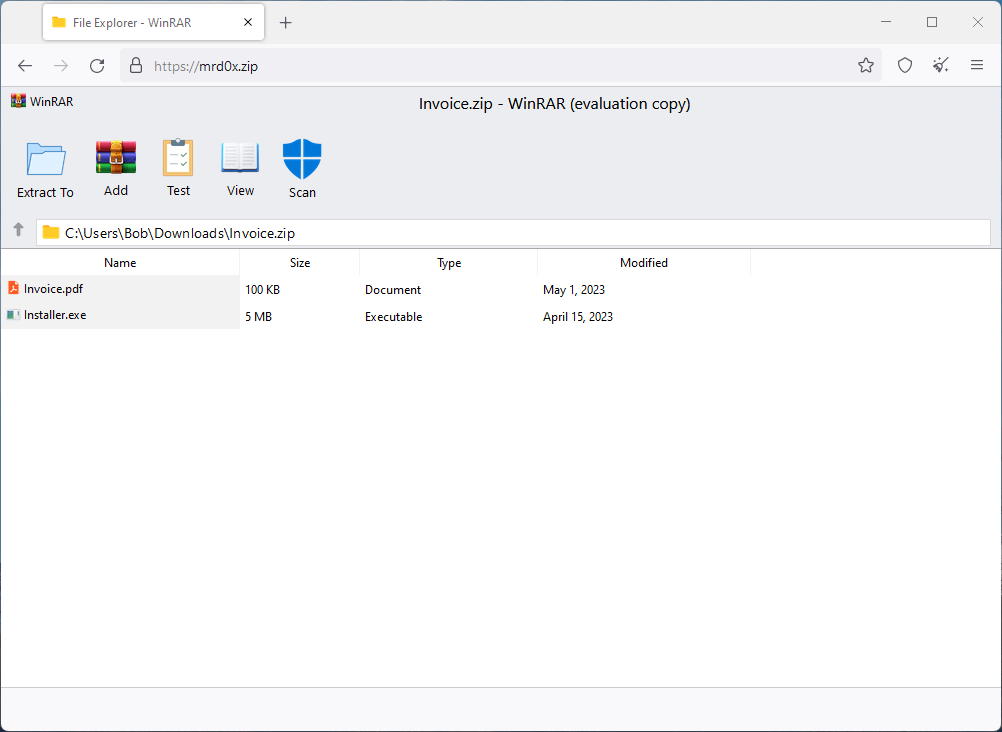
A security researcher using the ‘mr.dox’ moniker has demonstrated a phishing technique that emulates a file archiver in the browser using a ZIP domain, which creates a very deceptive setting that could convince a significant percentage of the site’s visitors.
RestorePrivacy
The phishing pages the researcher shared on GitHub can create false in-browser instances of familiar file archiving software like WinRAR or the Windows File Explorer. When a user visits a .zip domain, it appears as though they have opened a ZIP archive and are viewing its contents. This level of deception is possible due to intricate design elements on the sites, such as a fake security ‘Scan’ button, which assures users that the files are safe.
Moreover, the pages are designed for both credential theft and malware delivery. For example, it might show a PDF file that, when clicked, actually downloads a similarly named executable file (.exe). Given that Windows does not show file extensions by default, users may inadvertently run the malicious executable, thinking it’s a harmless PDF.
mrd0x.com
The attack proves that fears about the abuse potential of ZIP TLDs are neither unsubstantiated nor overstated, as the risk of confusion between file names and domain names has reached a new level. Also, it is essential to note that ‘Archiver in the Browser’ is merely one example of the many that competent phishing kit developers are bound to create in the forthcoming period.
In light of these new developments, it’s crucial that users maintain a high level of vigilance against tricky phishing pages like those created by ‘mr.dox.’
It is vital to treat ‘.zip’ and ‘.mov’ links with ultimate caution and suspicion, and avoid downloading files from those sites unless they can be verified as trustworthy. Any files downloaded from the internet should be scanned on an AV tool before launching, as nasty malware infections are only a double-click away.







Google is the devil Bobby.
Google has a reputation for coming up with and approving ideas from their own employees (not the public).
They have these “amazing” ideas that are like spaghetti. They toss them on the wall and see what sticks.
Mamma’s right