
A newly upgraded version of a long-running malware strain called XorDDoS is being used to launch powerful distributed denial-of-service (DDoS) attacks, with the United States emerging as the primary target.
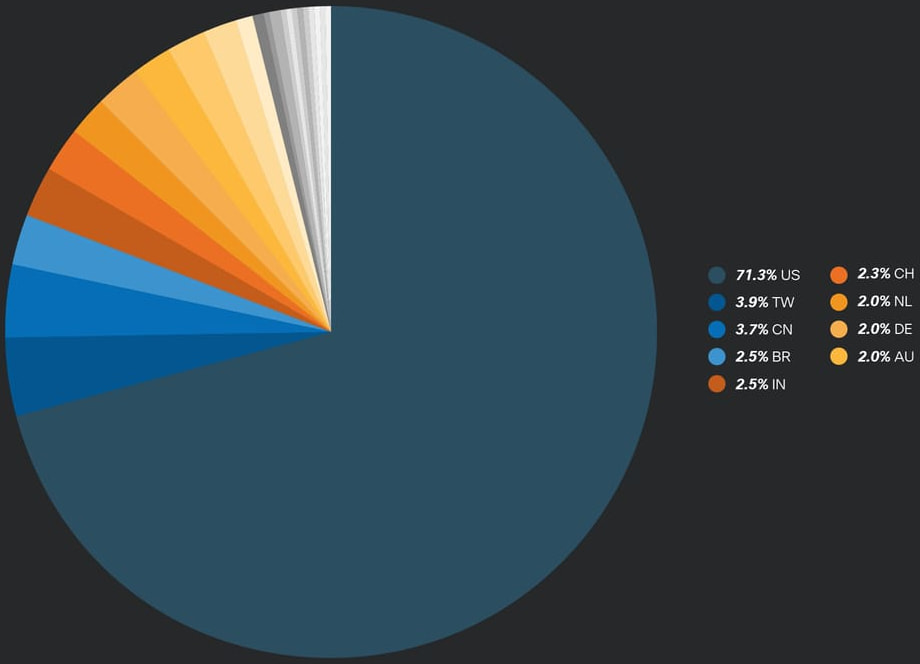
According to new research from Cisco Talos, over 70% of attempted attacks using the XorDDoS malware between late 2023 and early 2025 were aimed at U.S. systems.
The XorDDoS malware, which has been active for over a decade, infects Linux-based systems and turns them into remotely controlled “bots” that can be directed to overwhelm targets with traffic. This effectively knocks services offline and can cause widespread disruption. While this threat has been around since 2014, the latest version—referred to as the “VIP version”—represents a significant leap in sophistication and scale.
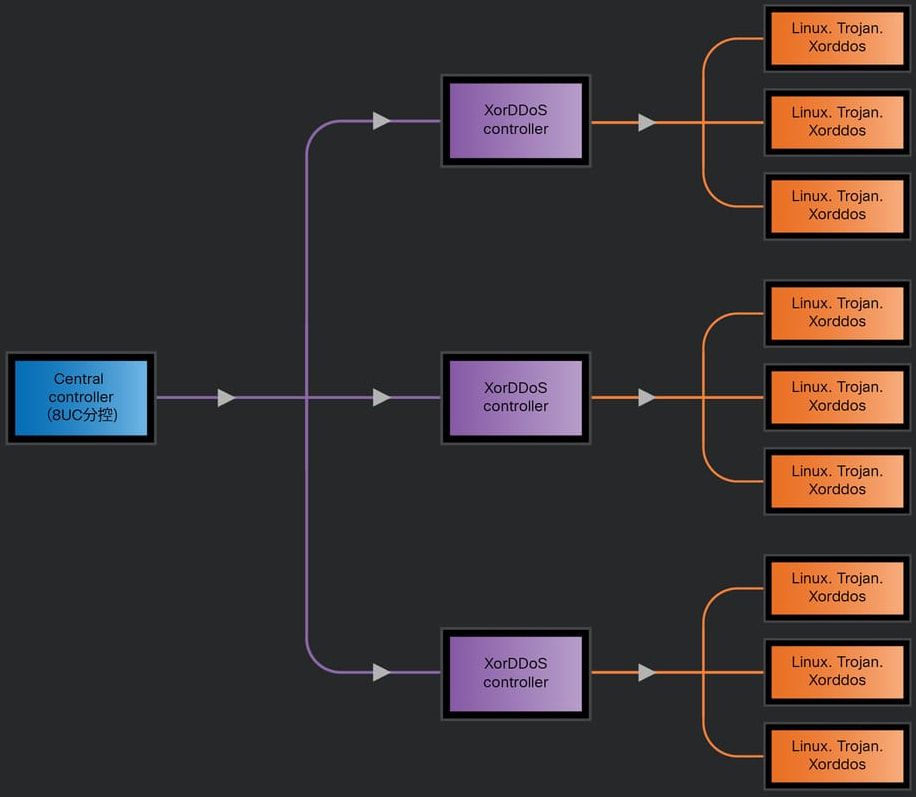
Cisco's analysis ties the infrastructure and control tools behind XorDDoS to Chinese-speaking operators. Researchers uncovered a multi-tiered command system featuring a newly built central controller that gives attackers a streamlined way to manage massive botnets and coordinate high-impact DDoS attacks globally, but with a sharp focus on the United States.
Between November 2023 and February 2025, Cisco observed that nearly half of all successfully infected systems were located in the U.S., with attackers attempting to use those compromised devices to target both domestic and international organizations. Other countries impacted include Canada, Japan, the U.K., Brazil, and Germany, but none saw the same level of targeting as the United States.
Cisco Talos
The new XorDDoS malware continues to spread primarily through brute-force attacks on systems running Secure Shell (SSH), a common remote login tool. Once attackers gain access using weak or default passwords, they install the malware, which then embeds itself deeply into the system to ensure it remains hidden and persistent.
The malware is designed to automatically reconnect to its command server and await instructions. It can also update itself or switch servers if needed — capabilities that make it especially resilient. The newly discovered “VIP version” adds performance upgrades, allowing infected systems to send significantly more data per second and handle much larger attack loads.
Cisco Talos
Industrial-scale DDoS-as-a-Service
The infrastructure powering this new version of XorDDoS appears to be part of a commercially developed toolkit. Cisco found evidence that the malware builder, sub-controller, and central controller are being packaged as a suite, likely for sale on underground markets. Translated features advertised in the builder's interface mention “anti-kick” stability, optimized resource usage, and the ability to manage over 10,000 infected systems at once.
One of the most concerning discoveries is a new central controller that allows attackers to remotely manage multiple sub-controllers from a single interface. This layered structure means a single attacker can efficiently operate and synchronize massive attack campaigns across hundreds or thousands of compromised systems. Cisco even found a QQ (a Chinese messaging app) contact left by the creator, suggesting a commercial intent behind these tools.
Cisco Talos
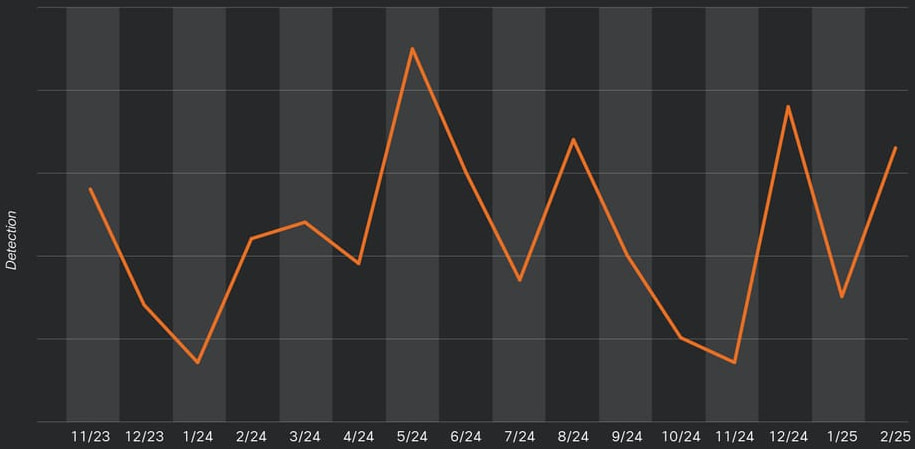
Despite years of industry efforts to detect and neutralize XorDDoS infections, Cisco continues to observe ongoing activity. The malware's adaptability — both in how it spreads and how it communicates with its control servers — means that many infected machines remain hidden and active.
The U.S. remains the prime target due to its dense concentration of internet infrastructure, cloud services, and enterprise systems, all of which are attractive to attackers seeking to disrupt services or extort businesses. With the introduction of more powerful tools like the VIP controller and its supporting infrastructure, the ability to launch larger, more precise attacks has become more accessible to cybercriminals.







Leave a Reply