
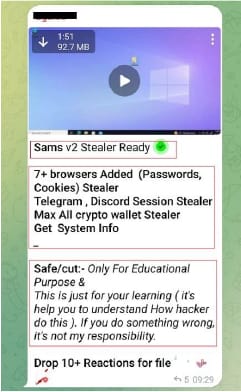
CYFIRMA researchers have identified a new information-stealing malware named “SamsStealer” that targets Windows systems.
This .NET-based executable infiltrates a variety of browsers and applications to extract sensitive data like passwords, cookies, and cryptocurrency wallet details, posing a significant threat to user privacy and security.
SamsStealer discovery and capabilities
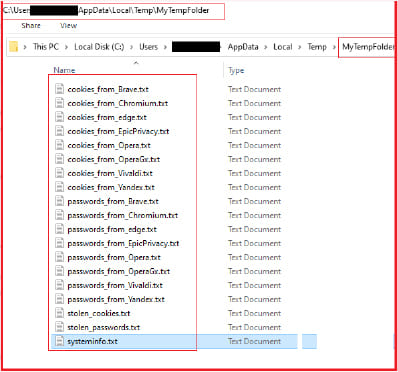
CYFIRMA's research team discovered SamsStealer circulating on the Telegram channel “SamsExploit.” This malware, written in .NET, is designed to stealthily gather and exfiltrate sensitive information. The analysis revealed that SamsStealer is a 32-bit Windows executable. Upon execution, it creates a temporary folder named “MyTempFolder” in the system's temporary directory. It then proceeds to collect system information, passwords, cookies, session data, and cryptocurrency wallet details from various sources.
CYFIRMA
SamsStealer targets an extensive range of browsers and applications, including Discord, Telegram, Chrome, Firefox, Opera, Brave, Vivaldi, and Yandex. It also targets cryptocurrency wallets such as Bitcoin, Ethereum, Zcash, Armory, Bytecoin, Jaxx, Exodus, Electrum, AtomicWallet, Guarda, and Coinomi. The malware stores the stolen data in the temporary folder as text files.
CYFIRMA
Upon execution, SamsStealer creates “MyTempFolder” in the system's temporary directory. It then proceeds to steal data and stores it in the temporary folder. The malware compresses the folder into “Backup.zip,” uploads the ZIP file to “gofile.io,” and sends the download link via Telegram to the attacker. The stealer's asynchronous data collection and efficient use of concurrency make it highly effective in gathering and exfiltrating sensitive information.
The stealer begins by creating the temporary folder and storing the gathered information. It compresses the collected data into a ZIP file named “Backup.zip,” uploads it to the file-sharing service “gofile.io,” and sends the download link to the attacker via Telegram.
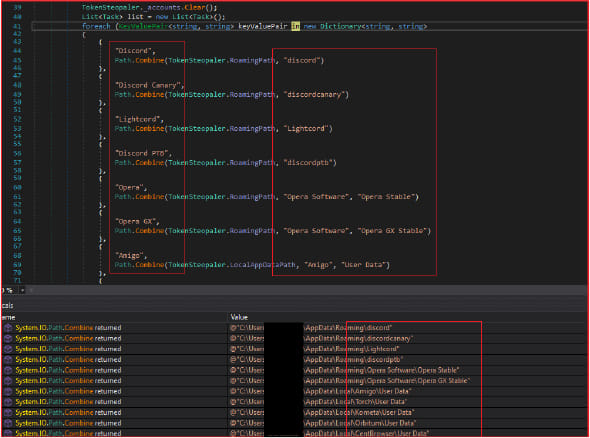
SamsStealer's enhanced capabilities, seen in its latest version (V2), include targeting additional browsers and applications to steal passwords and cookies. The group's primary language suggests a South Asian origin, particularly from India. OSINT investigations revealed multiple samples of SamsStealer submitted online since April 2024, indicating widespread use and distribution.
CYFIRMA
SamsStealer specifically targets popular browsers and messaging applications for data theft. These include:
- Browsers: Chrome, Firefox, Opera, Brave, Chromium, Vivaldi, Yandex
- Messaging Applications: Discord, Telegram
- Cryptocurrency Wallets: Bitcoin, Ethereum, Zcash, Armory, Bytecoin, Jaxx, Exodus, Electrum, AtomicWallet, Guarda, Coinomi
Defense recommendations
To defend against SamsStealer and similar threats, organizations should use advanced endpoint security solutions and reputable antivirus software, ensure regular updates, and employ network segmentation. Employee training on phishing and social engineering tactics is crucial. Configuring firewalls to block malicious IP addresses, implementing behavior-based monitoring, and enforcing application whitelisting can significantly enhance security. Regular backups, a comprehensive incident response plan, and staying informed with the latest threat intelligence are essential steps for proactive defense.







Leave a Reply